Cyber criminals are targeting Australian businesses right now. Moreover, phishing attacks have increased by 58% in Australia over the past year. Therefore, understanding these threats is crucial for your business survival.
As a Brisbane and Gold Coast business owner, you face constant email threats. Furthermore, these attacks are becoming more sophisticated every day. Consequently, knowing the difference between phishing types can save your business thousands of dollars.
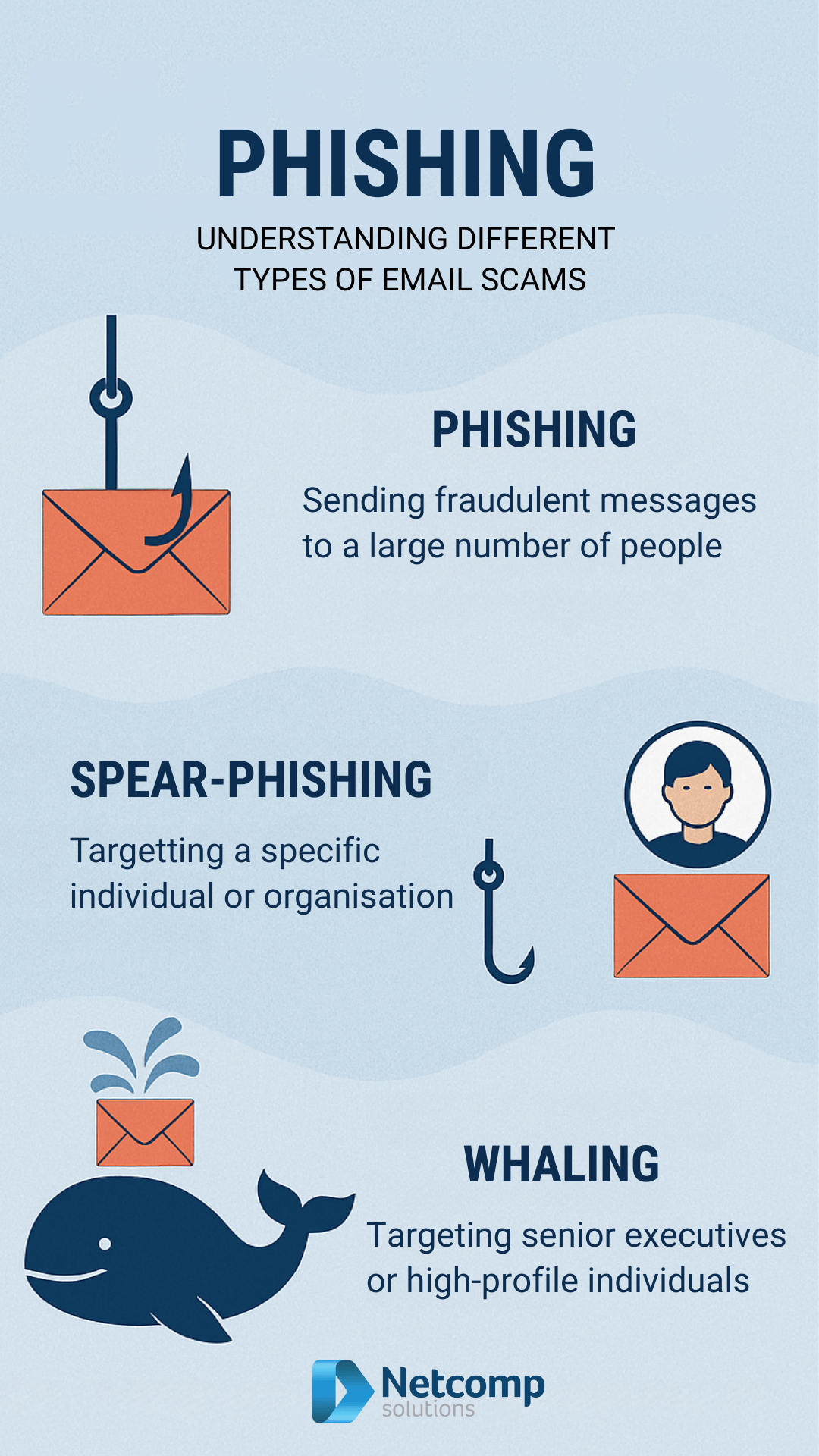
What Is Phishing?
Phishing represents a cybercrime where attackers impersonate legitimate organisations through fraudulent communications. Typically, criminals send emails that appear to come from trusted sources. Subsequently, they trick victims into revealing sensitive information.
Common phishing targets include:
- Banking credentials and passwords
- Credit card numbers and financial data
- Personal identification information
- Business account login details
- Employee payroll information
Additionally, phishing emails often create urgency to bypass your natural caution. Therefore, recognising these tactics is your first line of defence.
Understanding Spear-Phishing Attacks
Spear-phishing takes phishing to a more dangerous level through personalisation. Unlike generic phishing, attackers research specific individuals or organisations thoroughly. Consequently, these emails appear incredibly convincing and relevant.
Key characteristics of spear-phishing include:
- Personalised messages using your name and job title
- References to actual colleagues or business partners
- Mentions of recent company events or projects
- Use of company-specific terminology and language
- Highly targeted approach to specific employees
Moreover, spear-phishing success rates are significantly higher than standard phishing attempts. In fact, approximately 65% of cyber attackers use spear-phishing as their primary method. Therefore, Australian businesses must implement stronger verification processes.
What Makes Whaling Different?
Whaling specifically targets high-level executives and senior management within organisations. Furthermore, these attacks aim for the biggest fish in your company. Consequently, the potential damage from successful whaling attacks is exponentially greater.
Whaling attacks typically target:
- Chief Executive Officers (CEOs)
- Chief Financial Officers (CFOs)
- Company directors and board members
- Senior management team members
- Business owners and founders
Additionally, whaling emails often impersonate other executives or important business partners. Subsequently, they request urgent wire transfers or sensitive company information. Therefore, executive teams need specialised security training.
The Financial Impact on Australian Businesses
Australian businesses lose millions annually to phishing-related cybercrimes. Furthermore, the average cost of a data breach in Australia reached $4.9 million in 2024. Consequently, prevention is far more cost-effective than recovery.
Financial losses typically include:
- Direct monetary theft through fraudulent transfers
- Recovery costs for compromised systems
- Legal fees and regulatory fines
- Lost productivity during incident response
- Reputational damage affecting future business
Moreover, small businesses often struggle to recover from major phishing incidents. Therefore, investing in cybersecurity now protects your future operations.
How Cybercriminals Execute These Attacks
Understanding attack methodologies helps you recognise and prevent them effectively. Additionally, criminals constantly evolve their techniques to bypass security measures. Consequently, staying informed about current tactics is essential.
Common attack vectors include:
- Email spoofing to impersonate legitimate senders
- Malicious links directing to fake login pages
- Infected attachments containing malware
- Social engineering to manipulate human behaviour
- Phone calls following up on fraudulent emails
Furthermore, attackers often combine multiple techniques in sophisticated campaigns. Therefore, your defence strategy must address all potential entry points.
Warning Signs Every Employee Should Know
Training your team to recognise phishing attempts is crucial for business protection. Moreover, human awareness remains your strongest security layer. Consequently, regular education significantly reduces successful attack rates.
Red flags to watch for:
- Unexpected emails requesting sensitive information
- Unusual sender addresses with slight misspellings
- Generic greetings instead of personalised messages
- Urgent language creating artificial time pressure
- Suspicious links or unexpected attachments
- Requests for password resets you didn’t initiate
- Grammatical errors and awkward phrasing
Additionally, legitimate organisations never request passwords via email. Therefore, any such request should trigger immediate suspicion.
Real Examples Affecting Australian Businesses
Australian companies across all industries have fallen victim to these attacks. Furthermore, understanding real incidents helps prevent similar situations. Consequently, learning from others’ experiences is invaluable.
The Australian Competition and Consumer Commission (ACCC) reported that Australians lost over $2 billion to scams in 2023. Moreover, attackers impersonated CEOs requesting urgent wire transfers. Subsequently, employees transferred thousands before discovering the fraud.
Business Email Compromise (BEC) attacks cost Australian businesses $227 million in 2023 alone according to ACSC. Furthermore, these emails appear legitimate with correct company details. Consequently, accounts payable staff unknowingly pay fraudulent invoices.
Essential Protection Strategies

Implementing comprehensive security measures significantly reduces your vulnerability to attacks. Additionally, multiple layers of defence create robust protection. Therefore, combining technical solutions with human awareness provides optimal security.
Critical security measures include:
- Multi-factor authentication (MFA) on all accounts
- Advanced email filtering and anti-phishing software
- Regular security awareness training for staff
- Strict verification procedures for financial requests
- Regular software updates and security patches
- Encrypted email communications for sensitive data
- Clear incident response procedures
Moreover, Brisbane and Gold Coast businesses can access local cybersecurity support. Therefore, partnering with experienced IT providers enhances your security posture.
Email Security Best Practices
Proper email security forms the foundation of phishing prevention. Furthermore, implementing these practices significantly reduces attack success rates. Consequently, every business should adopt these standards immediately.
Essential email security steps:
- Verify sender addresses carefully before responding
- Hover over links to check actual destinations
- Never open unexpected attachments without verification
- Use separate email accounts for banking and finances
- Enable spam filters and security warnings
- Report suspicious emails to your IT team
- Delete phishing emails immediately after reporting
Additionally, implementing SPF, DKIM, and DMARC email authentication protocols protects your domain. Therefore, consult with IT professionals to configure these properly.
Creating a Verification Culture
Establishing clear verification procedures prevents costly mistakes within your organisation. Moreover, creating a culture where questioning is encouraged improves security. Consequently, employees feel empowered to verify suspicious requests.
Verification procedures should include:
- Mandatory callbacks for unusual financial requests
- Secondary approval for large transactions
- Face-to-face confirmation for sensitive information requests
- Standardised processes for password reset requests
- Regular communication about current threat campaigns
Furthermore, executives must support and model these verification behaviours. Therefore, leadership commitment is essential for cultural change.
Advanced Threat Detection Technologies
Modern technology provides powerful tools for detecting and blocking phishing attempts. Additionally, artificial intelligence and machine learning enhance threat detection capabilities. Consequently, investing in these technologies provides significant protection.
Effective security technologies include:
- Advanced threat protection platforms
- Email gateway security solutions
- Endpoint detection and response (EDR) systems
- Security information and event management (SIEM)
- User behaviour analytics
- Sandboxing for suspicious attachments
Moreover, these solutions work together to create comprehensive security ecosystems. Therefore, integrated security approaches provide the best protection.
Training Your Team Effectively
Regular security awareness training is crucial for maintaining strong defences. Furthermore, training must be engaging and relevant to be effective. Consequently, interactive training produces better retention and behaviour change.
Effective training elements include:
- Simulated phishing campaigns to test awareness
- Real-world examples relevant to your industry
- Regular updates on emerging threats
- Interactive workshops and discussions
- Clear reporting procedures
- Recognition for employees who identify threats
Additionally, training should occur quarterly at minimum. Therefore, schedule regular sessions throughout the year.
Mobile Device Security Considerations
Smartphones and tablets present additional phishing attack vectors for Australian businesses. Moreover, mobile devices often have weaker security than desktop computers. Consequently, mobile security requires specific attention.
Mobile security best practices:
- Install mobile device management (MDM) solutions
- Require strong passwords or biometric authentication
- Keep mobile operating systems updated
- Use only approved business applications
- Enable remote wipe capabilities
- Educate staff about mobile phishing threats
Furthermore, SMS phishing (smishing) is increasing rapidly across Australia. Therefore, train staff to recognise text message threats.
Incident Response Planning
Despite best efforts, breaches can still occur within any organisation. Additionally, how you respond determines the ultimate impact. Consequently, having a clear incident response plan is essential.
Your incident response plan should include:
- Immediate containment procedures
- Clear escalation pathways
- Communication protocols for stakeholders
- Evidence preservation methods
- Recovery procedures
- Post-incident review processes
Moreover, regularly test and update your incident response plan. Therefore, conduct tabletop exercises to ensure readiness.
Regulatory Compliance Requirements
Australian businesses must comply with various privacy and security regulations. Furthermore, non-compliance can result in significant penalties. Consequently, understanding your obligations is crucial.
The Privacy Act 1988 requires businesses to protect personal information adequately. Additionally, the Notifiable Data Breaches (NDB) scheme mandates reporting certain incidents. Therefore, compliance with these regulations is mandatory.
Key compliance considerations:
- Mandatory breach notification within 30 days
- Appropriate security measures for personal information
- Regular privacy impact assessments
- Staff training on privacy obligations
- Documentation of security policies and procedures
Moreover, industry-specific regulations may apply to your business. Therefore, consult with legal and IT professionals about your specific requirements.
Working with IT Security Professionals
Partnering with experienced cybersecurity providers enhances your protection significantly. Additionally, local Brisbane and Gold Coast expertise provides tailored support. Consequently, professional assistance is invaluable for small businesses.
Benefits of professional IT security support:
- Expert assessment of your current security posture
- Implementation of enterprise-grade security solutions
- 24/7 monitoring and threat detection
- Rapid incident response capabilities
- Regular security updates and maintenance
- Compliance guidance and documentation
Furthermore, managed security services provide cost-effective protection for growing businesses. Therefore, outsourcing security to experts makes financial sense.
Future Trends in Phishing Attacks
Cyber threats continue evolving rapidly with advancing technology and criminal sophistication. Moreover, understanding emerging trends helps you prepare for future threats. Consequently, staying informed about developments is essential.
Emerging phishing trends include:
- AI-generated deepfake voice and video phishing
- Cryptocurrency-related scam campaigns
- Supply chain compromise attacks
- Cloud service impersonation
- QR code phishing attempts
- Social media platform exploitation
Additionally, criminals are increasingly using legitimate services to bypass security filters. Therefore, defence strategies must continuously adapt.
Taking Action Today
Protecting your Australian business from phishing attacks requires immediate action and ongoing commitment. Moreover, cyber threats will only increase in sophistication and frequency. Consequently, delaying security improvements puts your business at serious risk.
Start protecting your business now by:
- Conducting a comprehensive security assessment
- Implementing multi-factor authentication across all systems
- Scheduling regular security awareness training
- Updating your email security configurations
- Creating clear verification procedures
- Partnering with experienced IT security professionals
Furthermore, cybersecurity is an ongoing process, not a one-time project. Therefore, commit to continuous improvement and vigilance.
Get Expert Help Today
Don’t let cybercriminals target your Brisbane or Gold Coast business. Additionally, professional support makes comprehensive security affordable and manageable. Consequently, contact Netcomp Solutions today for a free security consultation.
Our experienced team specialises in protecting Australian small businesses from phishing threats. Moreover, we provide tailored security solutions that fit your budget and needs. Therefore, let us help you build robust defences against evolving cyber threats.
Protect your business, employees, and customers with professional cybersecurity support from Netcomp Solutions.



