We take the hassle out of implementing the crucial cyber security measures, ensuring your business meets ACSC guidelines and enjoys enhanced protection.


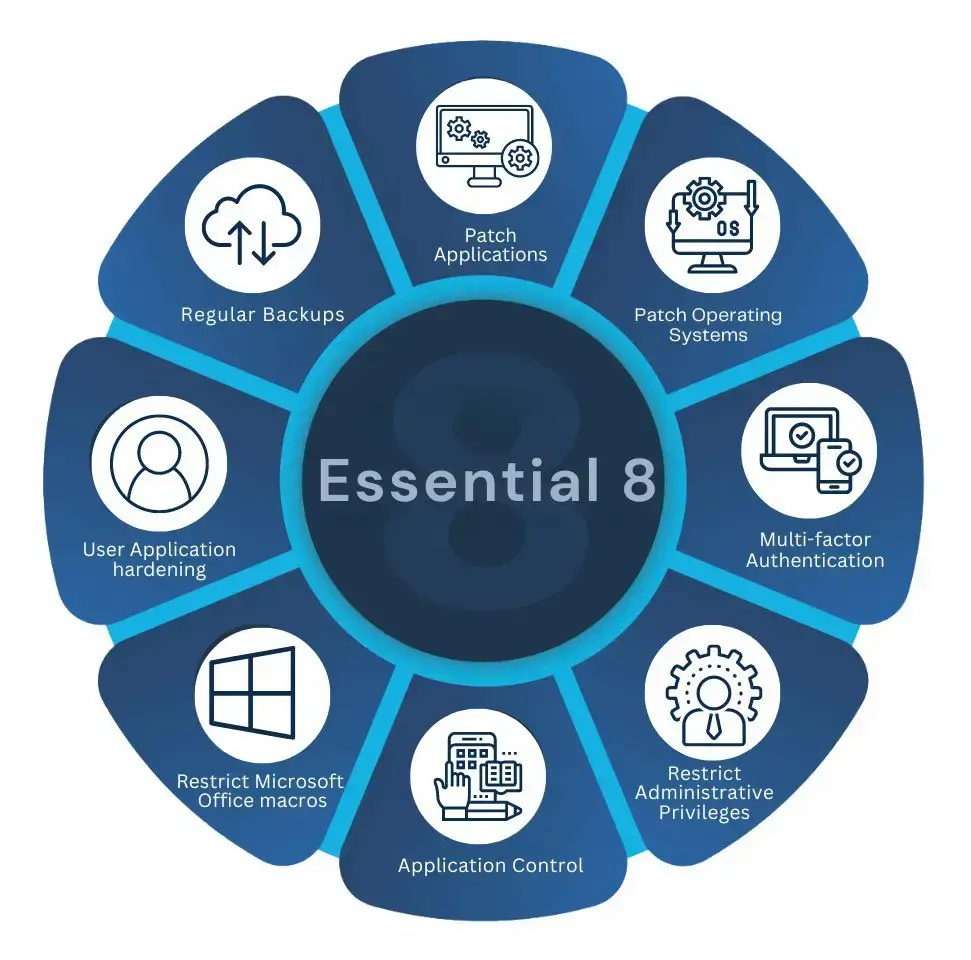
The Essential Eight are a set of cybersecurity strategies developed by the Australian Government to help organisations improve their cybersecurity posture. These eight strategies focus on key areas to mitigate risks from cyberattacks. They don’t involve complex solutions, but rather practical steps like:
For Australian businesses, the Essential 8 stands as a vital shield, protecting their data, assets, and reputation from cybercrime.
By implementing these measures, you make practically impossible for attackers to break in. This translates to real benefits:


Strategic Guidance: We start by nderstanding your unique needs and crafting a customised Essential 8 roadmap.
Expert Implementation: Our experts smoothly implement the necessary controls with minimal disruption.
Continuous Monitoring: We continuously monitor your systems, identifying and responding to threats quickly.
Clear Communication: We provide easy-to-understand reports that give you a clear picture of your security posture and progress.
Application Control: We manage authorised software, preventing unauthorised access and malware risks.
Third-Party Patching: We ensure even external applications are up-to-date and secure.
The Essential Eight Maturity Model is a free tool developed by the Australian Cyber Security Centre (ACSC). It helps businesses assess their implementation of the eight essential mitigation strategies. It rates your business on a scale of 0 to 3, with 3 being the most secure:
Level 0: No controls implemented.
Level 1: Basic controls in place, but may not be fully implemented or documented.
Level 2: Controls systematically implemented and monitored.
Level 3: Controls optimised and continually improved based on risk assessments and threat intelligence.
There are two main ways to determine your Essential Eight maturity level:
Self-assessment: Use the ACSC’s online Essential Eight Maturity Model Tool to answer questions about your implementation of each control across the various maturity levels.
Professional audit: Engage a cybersecurity expert to conduct a comprehensive assessment, identifying strengths, weaknesses, and areas for improvement.
While not strictly mandatory for all businesses, the E8 has significant weight in Australia. The Australian Signals Directorate (ASD) strongly recommends its adoption for all organisations, especially those handling sensitive data or government information. Non-compliance could lead to reputational damage, financial losses, and potential legal repercussions.
Both deal with cybersecurity, but with distinct focuses.
Essential 8: A set of eight foundational mitigation strategies specifically designed to combat common cyber threats. Think of it as a “must-have” security checklist.
SOC 2 (Service Organization Control Type 2): An independent audit report on a company’s security controls related to specific trust principles like security, availability, processing integrity, confidentiality, and privacy. It’s more comprehensive and tailored to an organisation’s unique needs.
ISM (Information Security Management): A broader framework encompassing overall data and information security management within an organisation. The Essential Eight falls under this umbrella, focusing on specific technical controls.
Essential 8: Emphasises implementation of specific mitigation strategies against cyber threats, providing a practical roadmap for improving security posture.
There is no specific “Essential 8 legislation.” The Essential Eight are recommended strategies by the ACSC to help organisations mitigate cyber security incidents. While not legally binding, following these guidelines can significantly enhance an organisation’s cybersecurity stance.
An Essential Eight assessment helps you.
Evaluate your current cybersecurity posture: Understand your strengths and weaknesses against common cyber threats.
Identify areas for improvement: Prioritise which controls need more attention to enhance your security.
Demonstrate compliance: Show stakeholders and potential clients your commitment to data protection.
Mitigate cyber risks: Proactively reduce the likelihood and impact of cyberattacks.
A cybersecurity framework is a set of guidelines and best practices designed to help businesses manage and reduce cybersecurity risk. It provides a structured approach for identifying, assessing, and responding to cyber threats, ensuring the protection of information systems and sensitive data. The E8 is one such framework, specifically tailored to the Australian context.
