Maximise your digital defence with our advanced Endpoint Security solutions, offering comprehensive protection, detection, and response capabilities for all devices


Endpoint protection involves securing various devices (like computers, mobile phones, and IoT devices) that connect to your network. It is crucial for businesses to protect these ‘endpoints’ because they often serve as entry points for security threats.
Advanced solutions go beyond traditional antivirus measures by using strategies like machine learning and behaviour analysis to detect and respond to threats proactively, ensuring your business’s digital safety.
With the proliferation of devices and the rise of sophisticated cyber threats, endpoint security is no longer optional. It is an essential part of a comprehensive security strategy that includes Endpoint Detection and Response (EDR) and Endpoint Management.
Effective endpoint protection safeguards your business from malware, ransomware, and helps to manage the security of devices that form part of the Internet of Things (IoT). By investing in a robust endpoint security solution, you are not only protecting your network but also ensuring the integrity and confidentiality of your sensitive data.
Choose Netcomp for unparalleled expertise in protecting your digital assets. With over 20 years of dedicated service, we have successfully shielded more than 100 businesses, earning more than 35 five-star reviews in Google. Our tailored endpoint services blend proven strategies with cutting-edge technology, including behaviour tracking and anomaly detection, to combat the most advanced cyber threats. Your business deserves the best defence, and we offer just that with our comprehensive endpoint device security solutions.
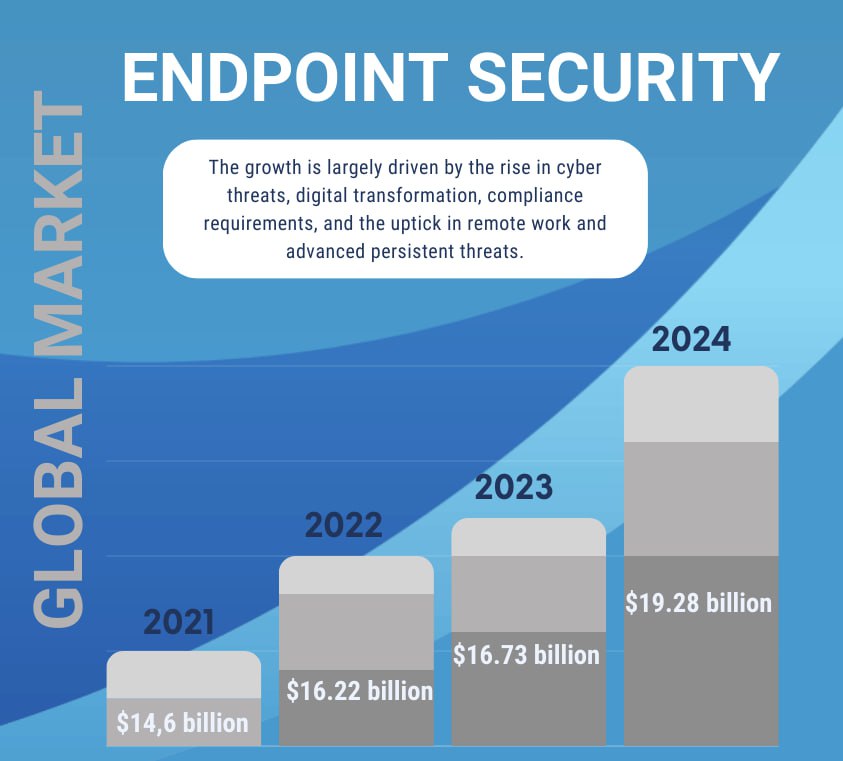


Endpoint protection is fundamental for business security. It acts as a shield for all devices that connect to your network, guarding against the myriad of cyber threats that evolve daily. With most breaches stemming from endpoint vulnerabilities, robust endpoint security ensures your business data remains uncompromised, maintaining trust and continuity.
Embrace endpoint protection; it’s not just a safeguard, it’s an investment in your business’s resilience and future.
Our services span a broad spectrum, aimed at enhancing your network’s endpoint management. Recognising the unique nature of cybersecurity challenges, we engage in comprehensive research to offer consultative, custom-fit security strategies.
Collaborating with leading tech providers, we ensure optimal protection for your digital assets, specialising in Data Loss Prevention, Endpoint Encryption, Endpoint Detection and Response (EDR) , Endpoint Forensics, and Mobile Security among others.
Your business needs a security strategy that’s as dynamic as the cyber threats it faces. Our ad-hoc approach includes:
Experience peace of mind with a managed security approach that offers:
Endpoint management involves overseeing and controlling devices (like laptops, smartphones, and IoT devices) that connect to an organisation’s network. It ensures that these devices comply with security policies and have the necessary access permissions. This process is crucial for maintaining network security and managing the devices efficiently, allowing for device authentication, security policy enforcement, and network access control from a centralised platform
A Host Intrusion Prevention System (HIPS) is a security feature that monitors a single host for suspicious activity by analysing events occurring within that host. It aims to prevent malicious activities such as exploits and malware infections by taking immediate action based on security policies, such as blocking potentially harmful programs or activities before they can cause damage.
Our IT support and services are comprehensive and tailored to meet the diverse needs of businesses. This includes Onsite and Remote IT Support to ensure immediate assistance, Data Backups and Disaster Recovery plans for business continuity, IT Security Audits to protect your digital assets, and IT Consulting for strategic technology planning. We also provide Administration services, Server & Network Support to maintain your IT infrastructure, Antivirus solutions to protect against malware, and a Service Desk for rapid response to IT issues. Cybersecurity solutions are also integral to our offerings, providing robust defence against online threats.
Endpoint Forensics is the process of investigating and analysing data on endpoints, such as computers and mobile devices, to uncover the sequence of activities or breaches that have occurred. This practice is vital for understanding the scope of a security incident, identifying the methods used by attackers, and taking steps to prevent future breaches. It involves collecting digital evidence and using forensic techniques to analyse file systems, memory, and logs.
EDR (Endpoint Detection and Response) is a cybersecurity solution that continuously monitors endpoint devices to detect and respond to cyber threats. EDR platforms provide real-time visibility into endpoint activities, offering tools for threat detection, investigation, and response to identified security incidents. They play a crucial role in identifying sophisticated threats that bypass traditional security measures and helping organizations quickly mitigate these threats.
Endpoint Encryption is a security measure that encrypts data on devices to protect it from unauthorised access. It ensures that even if a device is lost or stolen, the data it contains remains inaccessible without the correct encryption key. This is an essential aspect of data protection strategies, safeguarding sensitive information against breaches and ensuring compliance with data protection regulations.
