Your Business Can’t Afford Unpatched Systems
In 2025, unpatched operating systems remain the easiest way for cybercriminals to breach Australian businesses. Furthermore, a single unpatched vulnerability can cost your business thousands in recovery expenses.
However, there’s good news for small business owners. Patching operating systems—one of the Essential Eight strategies—effectively protects your business from most cyber threats. Additionally, it’s more straightforward than you might think.
This guide explains everything Australian small businesses need to know about patch operating system. Moreover, we’ll break it down in plain English with practical steps you can implement today.
What Are Patch Operating Systems in Essential Eight?
Operating system patching is one of eight essential mitigation strategies from the Australian Cyber Security Centre (ACSC). Specifically, it involves keeping your computers’ core software up to date with the latest security fixes.
Think of your operating system as your building’s foundation. Subsequently, patches are like repairing cracks before they become major structural problems. Without regular patching, cybercriminals can easily exploit known vulnerabilities to access your systems.
The Essential Eight framework recommends specific timeframes for applying patches. Consequently, this ensures your business maintains adequate protection against evolving cyber threats.
Want to understand the complete framework? Read our comprehensive guide on Essential Eight Explained.
What is a Patch? Real-World Examples That Matter
Simply put, a patch is a software update that fixes security holes in your operating system. Therefore, vendors release patches when they discover vulnerabilities that criminals could exploit.
Common Patch Examples:
Windows Security Updates
- Monthly “Patch Tuesday” releases fix critical Windows vulnerabilities
- Previously, these addressed issues like remote desktop access flaws
- Without patches, hackers can take control of unprotected computers
macOS Security Patches
- Apple releases patches for login bypass vulnerabilities
- Additionally, they fix issues in Safari and system components
- Recent patches addressed zero-day exploits actively used by criminals
Linux Kernel Updates
- Linux distributions patch remote access vulnerabilities
- Furthermore, they address privilege escalation risks
- These updates protect servers running your business applications
Understanding Different Update Types:
Importantly, patches differ from general updates and mitigations:
- Patches: Targeted fixes for specific security vulnerabilities
- Updates: Broader improvements including features and performance
- Mitigations: Temporary measures until permanent patches arrive
Once vendors discover vulnerabilities, they become public knowledge. Consequently, criminals rush to exploit unpatched systems before businesses apply fixes.
The OS Patching Process Simplified
Understanding the patching lifecycle helps you manage updates effectively. Here’s how it works:
1. Discovery Phase
First, vendors identify security vulnerabilities through research or incident reports. Then, they assess the severity and potential impact.
2. Release Stage
Next, vendors develop and test patches thoroughly. Subsequently, they release patches with documentation explaining the fixes.
3. Testing Period (Optional for Small Business)
Larger organisations test patches before widespread deployment. However, small businesses typically rely on vendor testing.
4. Deployment Time
Now, you install patches across your devices. Automation makes this process significantly easier.
5. Verification Step
After deployment, confirm patches installed successfully. Additionally, check that systems function normally.
6. Documentation Record
Finally, maintain records for compliance and audit purposes. This proves your Essential Eight adherence.
For application patching processes, see our guide on Essential Eight Patch Applications.
Essential Eight Maturity Levels: What They Mean
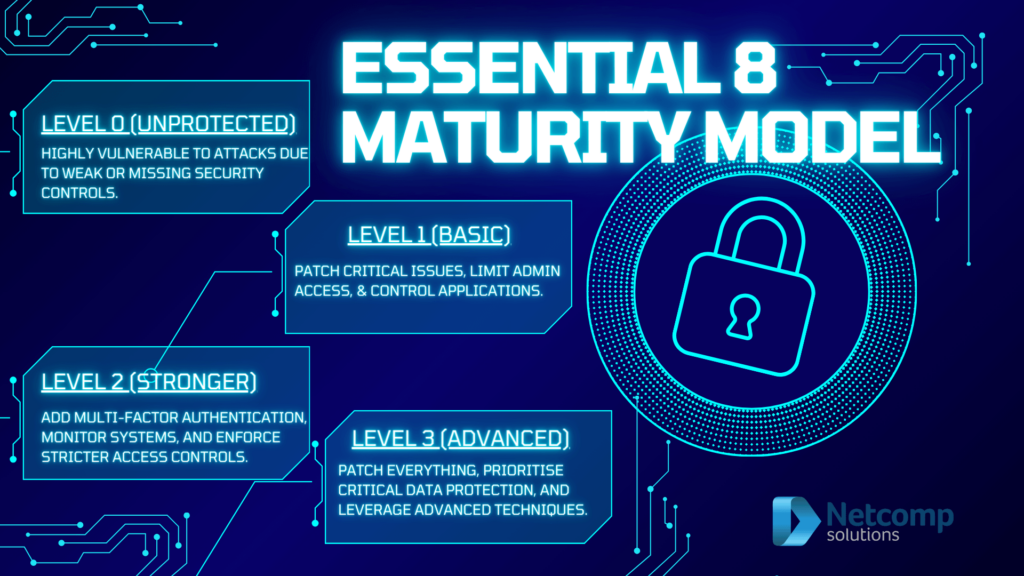
The ACSC defines three maturity levels with different patching requirements. Consequently, understanding these helps you choose appropriate targets.
Maturity Level Comparison:
| System Type | Level 1 | Level 2 | Level 3 |
| Internet-facing | 2 weeks (48 hrs if critical) | 2 weeks (48 hrs if critical) | 2 weeks (48 hrs if critical) |
| Internal systems | 1 month | 2 weeks | 48 hrs (critical), 1 month (non-critical) |
| Vulnerability scanning | Daily/fortnightly | Daily/weekly | Daily/weekly |
What Each Level Means:
1 Level: Foundation
- Suitable for most small businesses starting their journey
- Provides basic protection against common threats
- Achievable with standard tools and processes
2 Level: Increased Protection
- Faster response times for internal systems
- More frequent vulnerability scanning required
- Better suits businesses handling sensitive data
3 Level: Maximum Security
- Rapid response to all critical vulnerabilities
- Includes driver and firmware patching requirements
- Necessary for high-risk or regulated industries
Learn more about choosing your maturity level in our essential 8 maturity model guide.
Critical vs Non-Critical Patches Explained
Understanding patch severity helps you prioritise deployment effectively. Moreover, it ensures you meet Essential Eight timeframes.
Critical Patches:
- Active exploits exist in the wild currently
- Vendors specifically mark them as urgent priorities
- Can lead to complete system compromise
- Must be applied within 48 hours
Non-Critical Patches:
- Address potential vulnerabilities without active threats
- Provide security improvements and bug fixes
- Still important but allow longer deployment windows
- Can follow standard monthly schedules
Remember the WannaCry ransomware attack? It exploited an unpatched Windows vulnerability. Despite Microsoft releasing the patch months earlier, thousands of businesses suffered devastating consequences.
Three Types of Patch Management
Choosing the right approach depends on your business size and resources. Let’s explore each method.
1. Manual Patch Management
How It Works: IT staff manually download and install patches on each device. Then, they verify successful installation individually.
Advantages:
- Firstly, complete control over patching process
- Secondly, no additional software costs required
- Thirdly, works for very small businesses
Disadvantages:
- Extremely time-consuming for multiple devices
- Additionally, human error leads to missed patches
- Lastly, not scalable beyond 5-10 devices
Best For: Micro businesses with minimal devices and tight budgets.
2. Automated Patch Management
How It Works: Software automatically deploys patches according to your schedule. Additionally, it reports on deployment success rates.
Recommended Tools for Australian Businesses:
- Microsoft Intune (included with Microsoft 365 Business Premium)
- Windows Update for Business (built into Windows Pro)
- ManageEngine Patch Manager (third-party solution)
- PDQ Deploy (good for Windows environments)
Advantages:
- Saves significant time and resources
- Ensures consistent patching across devices
- Scales easily as business grows
- Provides compliance reporting automatically
Disadvantages:
- Requires initial setup and configuration
- Some tools involve ongoing costs
- May need IT support initially
Best For: Businesses with 5+ devices needing reliable, consistent patching.
3. Managed Service Provider (MSP) Approach
How It Works: Australian MSPs like Netcomp Solutions handle your entire patching process. Furthermore, they monitor systems 24/7 for vulnerabilities.
What MSPs Provide:
- Firstly, expert patch management and deployment
- Secondly, compliance reporting for Essential Eight
- Thirdly, proactive vulnerability monitoring
- Moreover, backup verification before major updates
- Finally, after-hours deployment to minimise disruption
Advantages:
- Professional expertise without hiring staff
- Peace of mind with 24/7 monitoring
- Comprehensive compliance documentation
- Frees you to focus on business
Disadvantages:
- Monthly service costs to consider
- Requires trusting external provider
Best For: Businesses without dedicated IT staff or those needing compliance certainty.
Netcomp Solutions specialises in Essential Eight implementation for Australian small businesses. Contact us for a free patch management assessment.
Implementing OS Patching: Your Step-by-Step Guide
Now, let’s get practical with implementation. Follow these steps systematically.
Step 1: Take Complete Inventory
First, document everything you need to protect:
- Firstly, list all computers (desktops, laptops, tablets)
- Secondly, include servers and network equipment
- Thirdly, document current operating system versions
- Lastly, identify unsupported or end-of-life systems
Critical: Windows 7, 8, and Server 2008 are no longer supported. Therefore, they require immediate replacement.
Step 2: Choose Your Patching Method
Consider these factors when deciding:
- Business size: How many devices need patching?
- IT resources: Do you have technical staff available?
- Budget: What can you invest monthly?
- Compliance needs: What maturity level suits your industry?
For most small businesses, automated patching offers the best balance. Alternatively, MSPs provide comprehensive coverage without internal resources.
Step 3: Configure Automated Updates
For Microsoft 365 Business Premium Users:
Fortunately, you already have powerful tools included. Here’s how to use them:
Enable Windows Update for Business:
- Access Microsoft Intune admin centre
- Navigate to Devices > Windows > Update rings
- Create your first update ring policy
- Set appropriate deferral periods (7-14 days)
- Assign to all Windows devices
Create Update Rings: Rather than updating everything simultaneously, use staged deployment:
- Test Ring (5% of devices): IT staff and volunteers
- Production Ring (95% of devices): Everyone else after 7 days
This approach catches problems before widespread deployment.
Step 4: Implement Vulnerability Scanning
Next, you need to identify missing patches proactively. Microsoft Defender Vulnerability Management comes with Microsoft 365 Business Premium.
Setup Process:
- Onboard devices to Microsoft Defender
- Enable vulnerability scanning features
- Configure scan frequency (daily for internet-facing, weekly for internal)
- Review vulnerability reports regularly
Additionally, this tool identifies missing patches automatically. Subsequently, it prioritises them by severity.
Step 5: Create Your Rollback Plan
Sometimes, patches cause unexpected issues. Therefore, always prepare for problems:
Before Major Updates:
- Verify recent backups exist and work
- Document current system state
- Schedule updates during low-activity periods
- Communicate planned downtime to staff
If Problems Occur:
- Rollback to previous system restore point
- Contact Microsoft support or your MSP
- Document the issue for future reference
Learn more about protecting your data with our Backups for Small Business guide.
Overcoming Common Patching Challenges

Australian small businesses face similar obstacles. Here’s how to address them effectively.
Challenge: “We Can’t Afford Downtime”
Solutions:
- Schedule updates outside business hours (evenings or weekends)
- Use grace periods allowing users to delay reboots
- Implement test rings to catch problems early
- Deploy critical patches immediately regardless of schedule
Challenge: “Limited IT Resources”
Solutions:
- Start with built-in Windows Update automation
- Consider Microsoft 365 Business Premium for Intune
- Partner with Australian MSPs like Netcomp Solutions
- Begin with Maturity Level 1, then progress gradually
Challenge: “Legacy Systems Won’t Update”
Unfortunately, unsupported systems pose significant risks. However, you have options:
Short-term Measures:
- Firstly, isolate legacy systems from your main network
- Secondly, implement additional security controls around them
- Thirdly, restrict internet access where possible
- Finally, monitor them more closely for threats
Long-term Solution:
- Budget for operating system upgrades
- Moreover, plan migration timeline (6-12 months)
- Additionally, consider cloud alternatives to reduce hardware costs
- Lastly, factor replacement into yearly IT budget
Integration With Other Essential Eight Controls
Generally operating system patching works best alongside other security measures. Together, they create layered protection.
Complementary Security Controls:
Application Control
Even with patched systems, application control prevents unauthorised software execution. Consequently, you block threats before they run. Read our guide: The Power of Application Control: Securing Your Systems.
Multi-Factor Authentication (MFA)
Furthermore, MFA adds protection beyond operating system security. Even if attackers exploit vulnerabilities, they still need authentication credentials. Learn more: Fortress Your Business: Multi-Factor Authentication.
User Application Hardening
Additionally, hardening reduces your attack surface alongside OS patching. This includes disabling unnecessary features and macros. See: User Application Hardening Essential 8.
Regular Backups
Finally, backups provide your safety net if patching fails or ransomware strikes. Moreover, they enable quick recovery from any incident. Explore: Backups for Small Business.
This layered approach ensures multiple barriers protect your business. If one control fails, others maintain security.
Monitoring Your Patch Management Success
Tracking performance ensures ongoing compliance and identifies issues quickly. Therefore, monitor these key metrics:
Essential Metrics:
Patch Deployment Rate
- Percentage of devices with latest patches
- Time from patch release to installation
- Failed deployment attempts requiring attention
Vulnerability Status
- Number of unpatched vulnerabilities identified
- Average time to remediate critical issues
- Devices with unsupported operating systems
Compliance Tracking
- Devices meeting Essential Eight timeframes
- Documentation for audit purposes
- Maturity level achievement progress
Recommended Reporting Tools:
Microsoft Intune Reports: Built into Microsoft 365 Business Premium, these reports show:
- Update deployment status across devices
- Compliance with your policies
- Devices requiring attention immediately
Windows Update Reports: Standard Windows includes basic reporting showing:
- Recently installed patches
- Pending updates requiring installation
- Failed update history and errors
Regular review of these reports helps maintain security. Additionally, they demonstrate compliance to clients and insurers.
Your 30-Day Action Plan
Ready to implement Essential Eight OS patching? Follow this practical timeline:
1 Week: Assessment Phase
- ☐ Inventory all devices and operating systems
- ☐ Identify unsupported systems needing replacement
- ☐ Determine current patch status across devices
- ☐ Document findings for baseline measurement
2 Week: Planning Phase
- ☐ Choose target maturity level (start with Level 1)
- ☐ Select patching method and tools
- ☐ Create update schedule for your business
- ☐ Communicate plans to staff members
3 Week: Implementation Phase
- ☐ Configure automated update system
- ☐ Set up update rings for staged deployment
- ☐ Enable vulnerability scanning tools
- ☐ Test process with small device group
4 Week: Monitoring Phase
- ☐ Verify patches deployed successfully
- ☐ Document your process thoroughly
- ☐ Train staff on reboot procedures
- ☐ Schedule regular review meetings
Take Action Today
Operating system patching protects your Australian business from preventable cyber incidents. Moreover, it’s achievable regardless of your business size or technical expertise.
Start with Maturity Level 1 requirements. Then, progress to higher levels as your capabilities grow. So automation makes ongoing compliance manageable and sustainable.
Remember, OS patching forms just one part of your Essential Eight strategy. However, it’s among the most critical for preventing breaches.
Need help implementing Essential Eight patching? Netcomp Solutions provides comprehensive patch management services for Australian small businesses. Our experts handle everything from assessment to ongoing monitoring.
Contact Netcomp today for your free Essential Eight assessment. We’ll evaluate your current security posture and create a practical implementation roadmap.
FAQ
Q: How often should small businesses patch operating systems?
A: At minimum, patch internet-facing systems within 2 weeks. Internal systems require patching within 1 month. However, apply critical patches within 48 hours regardless of system type.
Q: Do I need patching if I have antivirus software?
A: Yes, absolutely. Antivirus complements patching but doesn’t replace it. Unpatched vulnerabilities allow attackers to bypass antivirus protection entirely.
Q: What if a patch breaks something?
A: First, ensure you have recent backups ready. Then, test patches on non-critical devices first. Finally, maintain rollback capability using system restore points.
Q: Can I patch during business hours?
A: Ideally, plan patches for off-hours when possible. However, use grace periods allowing users to delay necessary reboots. Critical patches take priority over convenience.
Q: Are free patching tools enough for small business?
A: For many small businesses, yes. Windows Update for Business with Microsoft 365 Business Premium covers most needs effectively. However, MSPs provide additional expertise and peace of mind.
Netcomp Solutions is your trusted Australian IT support provider specialising in Essential Eight implementation. Consequently, we help small businesses achieve cyber security compliance without complexity. Contact us today for expert guidance.



