In Australia, cyberattacks are on the rise, with small and medium businesses suffering the most financial damage. Did you know that according to the ASD Cyber Threat report 2022-2023, the average self-reported cost of cybercrime for small businesses is $46,000, while for medium businesses this number reaches a shocking $97,000? Moreover, this figure continues to rise every year.
So, how can businesses protect themselves from these growing threats? The answer lies in a set of cybersecurity best practices known as the Essential Eight. In this article, we’ll provide a clear and concise explanation of what is Essential 8, along with practical tips on how to implement these strategies to protect your business from cyberattacks.

What is Essential 8?
The Essential Eight is a set of cybersecurity strategies developed by the Australian Signals Directorate (ASD). These strategies help businesses of all sizes protect themselves from cyberattacks. Although they are not legally required, using these strategies is highly recommended because they provide a strong framework for protecting sensitive data and lowering the risk of data breaches.
Basically, the ASD chose the Essential Eight strategies based on their analysis of common cyberattack methods. Therefore, these strategies aim to address the most frequent weaknesses exploited by cybercriminals.
To better understand what is Essential 8, it’s important to know that these guidelines are designed specifically for businesses. However, individuals can also use these principles to protect their online activities.
Implementing the Essential Eight
Implementing the Essential Eight certainly involves a combination of technical measures, administrative controls, and awareness training. For this reason, businesses can work with cybersecurity experts or managed service providers to help with implementation and ongoing management.
The Essential Eight offers numerous benefits, including:
- Reduced risk of data breaches: By following these strategies, businesses can greatly reduce the chance of unauthorised access to their sensitive information.
- Improved cybersecurity posture: In addition, the Essential Eight offers a clear approach to strengthening overall cybersecurity defenses.
- Enhanced customer trust: Consequently, businesses that show a strong commitment to data security can build trust with their customers.
- Compliance with industry regulations: Finally, the Essential Eight often aligns with various industry-specific regulations and standards, such as the General Data Protection Regulation (GDPR).
Essential Eight vs other Tools to protect your business
While antivirus software, multi-factor authentication (MFA), and spam filters are crucial tools in a business’s cybersecurity arsenal, they alone are not enough to guarantee complete protection. In contrast, the Essential Eight, a set of best practices from the Australian Signals Directorate (ASD), offers a more complete way to protect your business from cyber threats.
Besides basic tools like antivirus and MFA, the Essential Eight includes other strategies, such as:
- Patch management: This ensures your software and operating systems are always updated with the latest security patches.
- Application whitelisting: This approach limits the use of only approved applications to prevent malware and unauthorised access.
- Regular backups: By creating and storing backups of your critical data, you can recover quickly from a data breach or other incidents.
By adding these strategies, you can greatly improve your business’s cybersecurity posture. Furthermore, you will reduce the risk of falling victim to advanced cyberattacks.
A Brief History of What is Essential 8

Let’s explore what is essential 8. Introduced by the Australian Signals Directorate (ASD) in 2017, the Essential Eight was developed to help Australian businesses combat cyber threats. While the framework may draw inspiration from international models, it is uniquely tailored to address the specific needs and challenges of Australian businesses. Factors influencing its development include:
- Unique threat landscape: Firstly, Australia faces distinct cyber threats, which may differ from those in other countries.
- Regulatory and compliance requirements: Secondly, the Essential Eight may align with specific Australian laws and regulations related to cybersecurity.
- Cultural and business practices: Thirdly, the framework may be customised to fit the unique cultural and business practices of Australian organisations.
Undoubtedly, the Essential Eight emerged in response to increasing cyberattacks, especially targeting small and medium-sized enterprises (SMEs). These attacks often exploit common vulnerabilities, causing financial loss, data breaches, and reputational damage. The ASD aimed to provide a practical, understandable framework that businesses of all sizes could implement to protect against cyber threats.
Updates to the Essential Eight model
While the core principles and strategies remain the same, the ASD has periodically revised the framework to address new cyber threats and best practices.
Key updates and changes include:
- Clarification of specific controls: The ASD has given more detailed guidance on certain controls, such as patch management and application whitelisting.
- Alignment with international standards: The Essential Eight has been aligned with global cybersecurity standards, like the NIST Cybersecurity Framework and ISO 27001.
- Incorporation of new technologies: The ASD has added new technologies and trends, such as cloud computing and artificial intelligence, to keep the Essential Eight relevant in today’s changing threat landscape.
These updates show the ASD’s ongoing commitment to offering businesses a practical and current framework for protection against cyber threats. Thus, by staying informed about the latest revisions to the Essential Eight, businesses can ensure that their cybersecurity measures follow current best practices.
Global Cybersecurity Models
While the Essential Eight is a powerful tool, it is not the only cybersecurity framework available. Let’s compare it to some other well-known models:
- NIST Cybersecurity Framework (USA): This voluntary framework offers a broader, risk-based approach to cybersecurity. So tt outlines five core functions — Identify, Protect, Detect, Respond, and Recover — and provides a catalog of security controls that can be tailored to an organisation’s specific needs.

Contrast with Essential Eight: Overall, the NIST framework is more flexible but requires a deeper understanding of risk assessment and implementation. Meanwhile, the Essential Eight provides a clear set of actions, making it easier for smaller businesses to understand and use.

Cyber Essentials (UK): Similar to the Essential Eight, Cyber Essentials focuses on a set of basic technical controls for cyber defense. However, it requires certification, which can be expensive and time-consuming for some businesses.
Contrast with Essential Eight: To summarise, cyber Essentials is primarily focused on basic technical controls. While the Essential Eight covers both technical and administrative controls for a more comprehensive approach.
Uniqueness of Essential Eight
Here’s why the Essential Eight is particularly relevant to Australian businesses:
- Tailored to local threats: The ASD regularly analyses local cyber threats and updates the Essential Eight strategies based on these insights.
- Aligns with regulations: The Essential Eight fits with Australian laws and compliance requirements related to data protection and cybersecurity.
- Free and easy to implement: Unlike Cyber Essentials certification, implementing the Essential Eight is free and does not require complex assessments.
By focusing on these factors, the Essential Eight offers a practical and relevant framework for Australian businesses to protect themselves from cyber threats.
Is Essential Eight Mandatory?
The Essential Eight is a voluntary guideline, not a legal requirement for Australian businesses. However, it is highly recommended as a best practice to help reduce the risk of data breaches, financial losses, and reputational damage.
Understanding of what is Essential 8
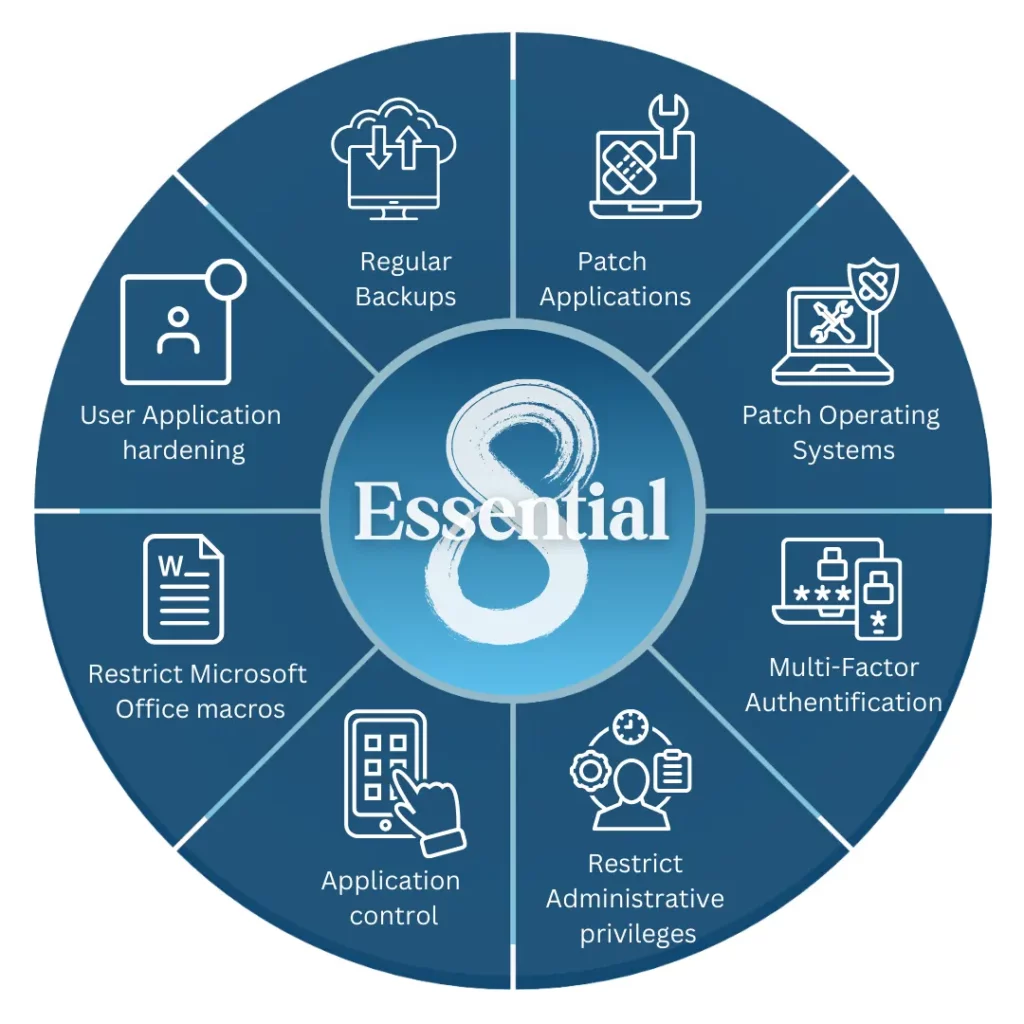
The Eight Strategies
- Patch application: Ensuring that software and operating systems are always up-to-date with the latest security patches.
- Restricting administrative rights: Limiting the number of users with administrative privileges.
- User application hardening: Configuring applications to minimize security risks.
- Regular backups: Creating and storing regular backups of critical data.
- Patching of third-party software: Ensuring that third-party applications are also up-to-date.
- Application whitelisting: Restricting the execution of only authorized applications.
- Web browsing controls: Implementing controls to protect users from malicious websites and phishing attacks.
- Multi-factor authentication: Requiring users to provide multiple forms of identification to access systems.
Explanation of Each Strategy
- Patch Application:
- Purpose: To fix vulnerabilities in software and operating systems that cybercriminals might exploit.
- How it contributes: By applying security patches, businesses can close known weaknesses and prevent attackers from gaining unauthorized access.
- Example: A company that doesn’t update its web server software may be vulnerable to new exploits, allowing attackers to control the server.
- Restricting Administrative Rights:
- Purpose: To limit the number of users with administrative privileges, reducing the risk of unauthorized access and control.
- How it contributes: By granting administrative rights only to authorized users, businesses can minimize potential damage from compromised accounts.
- Example: A company that gives administrative rights to all employees may risk unauthorized access from malicious insiders or compromised accounts.
- User Application Hardening:
- Purpose: TTo configure applications to reduce security risks by disabling unnecessary features or restricting access to sensitive data.
- How it contributes: By hardening applications, businesses can lower the chances of vulnerabilities being exploited.
- Example: A company that allows remote access to its accounting software without strong authentication may be vulnerable to unauthorized access.
- Regular Backups:
- Purpose: To create and store regular backups of critical data, enabling recovery in the event of a data breach or other incident.
- How it contributes: By having regular backups, businesses can recover their data and minimize the impact of a cyberattack.
- Example: A company that loses primary data storage due to a ransomware attack can restore its data from backups and resume operations.
Further explanation of each strategy
- Patching of Third-Party Software:
- Purpose: To ensure that third-party applications are also updated with security patches.
- How it contributes: Third-party applications can introduce vulnerabilities, so keeping them patched is essential.
- Example: A company that doesn’t update third-party accounting software may be vulnerable to known exploits, allowing attackers to access sensitive financial data.
- Application Whitelisting:
- Purpose: To allow only authorized applications to run, preventing malware and unauthorized access.
- How it contributes: By limiting which applications can run on a system, businesses can reduce the risk of malware infections and unauthorized access.
- Example: A company that uses application whitelisting can block unauthorized software, lowering the risk of malware attacks and data breaches.
- Web Browsing Controls:
- Purpose: To protect users from malicious websites and phishing attacks through web browsing controls.
- How it contributes: By implementing web browsing controls, businesses can prevent users from clicking on malicious links or downloading malware.
- Example: A company that uses web filtering can block access to malicious websites and phishing attempts.
- Multi-Factor Authentication:
- Purpose: To require users to provide multiple forms of identification, making it harder for unauthorized individuals to access systems.
- How it contributes: By using multi-factor authentication, businesses add an extra security layer and reduce the risk of account compromise.
- Example: A company that requires users to enter a password and a code from a time-based one-time password (TOTP) generator is using multi-factor authentication.
To explain each of these strategies in more detail, please refer to our article, “Defend Your Business with the Essential Eight.”
Implementing the Essential 8
Key Requirements
To effectively implement the Essential Eight, businesses should follow these steps:
- Conduct a cybersecurity assessment: First, evaluate your current cybersecurity posture to find vulnerabilities and gaps.
- Develop a comprehensive cybersecurity plan: Next, create a plan that outlines the specific actions needed to implement each Essential Eight strategy.
- Allocate resources: Additionally, assign dedicated staff or hire external experts to oversee cybersecurity tasks.
- Provide training and awareness: Furthermore, educate employees about cybersecurity best practices and the importance of following the Essential Eight.
- Implement technical controls: Moreover, deploy necessary tools and technologies to enforce the Essential Eight strategies.
- Monitor and review: Finally, regularly assess the effectiveness of your cybersecurity measures and make adjustments as needed.
Challenges and Solutions
Understanding what is essential 8 and implementing it, may present challenges. However, with proper planning, these obstacles can be overcome. Common challenges include:
- Resource constraints: Firstly, smaller businesses may face budget and staffing limits. To address this issue, consider outsourcing cybersecurity tasks or using cost-effective solutions.
- Complexity: Secondly, implementing all eight strategies can be complex, especially for businesses with limited cybersecurity expertise. Thus, seeking guidance from cybersecurity consultants or managed service providers can help simplify the process.
- Employee resistance: Thirdlt, some employees may resist changes to their routines or be reluctant to follow cybersecurity best practices. Therefore, address this by providing clear communication, training, and incentives.
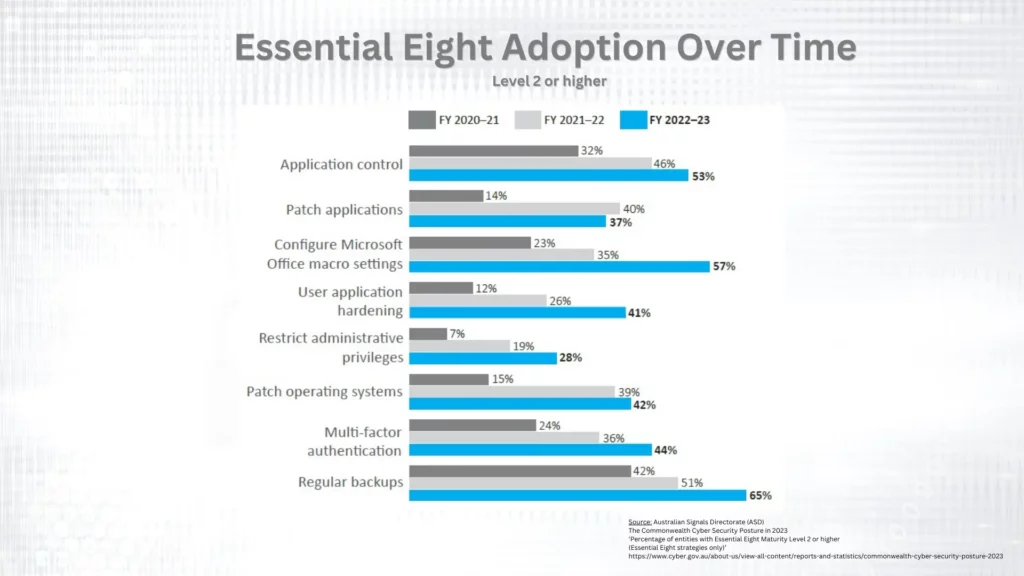
Benefits of Implementing the Essential Eight
Successfully implementing the Essential Eight can offer significant benefits. For instance:
- Reduced risk of cyberattacks: By following these strategies, businesses can significantly lower the likelihood of cybercriminal attacks.
- Improved data security: Additionally, the Essential Eight helps protect sensitive data from unauthorized access, theft, or loss.
- Enhanced customer trust: Furthermore, businesses that show a strong commitment to data security can build trust with their customers and clients.
- Compliance with regulations: Moreover, the Essential Eight often aligns with industry regulations and standards, like the General Data Protection Regulation (GDPR).
- Improved business resilience: By preparing for cyber threats, businesses can better withstand disruptions and maintain operational continuity.
By investing in cybersecurity and implementing the Essential Eight, businesses can protect their assets, enhance their reputation, and build a more resilient organisation.
Essential Eight Maturity Levels
The Essential Eight framework is divided into different maturity levels, representing various degrees of implementation. These levels provide a roadmap for businesses to progressively enhance their cybersecurity posture.
Describing Each Level
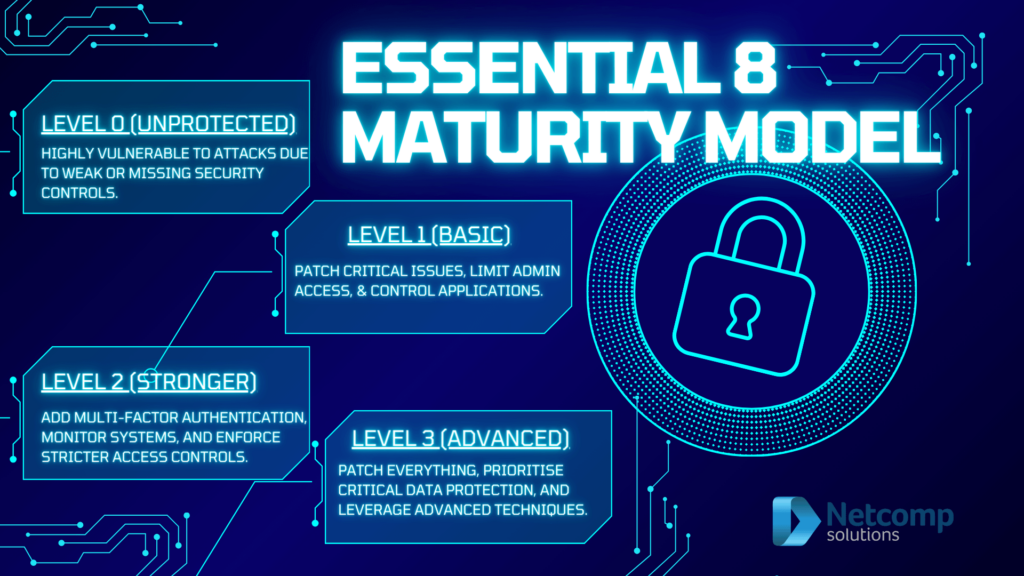
The Essential Eight maturity levels are generally categorized as follows:
1.Basic: At this level, businesses have implemented the fundamental cybersecurity controls. However, they may still have significant vulnerabilities.
2. Intermediate: Businesses at this level have made considerable progress in implementing the Essential Eight strategies. Nonetheless, they may still need improvements in some areas.
3.Advanced: Businesses at this level have fully implemented the Essential Eight strategies. Thus, they have robust cybersecurity measures in place.
Why Businesses Should Aim for Higher Maturity Levels
Businesses should aim to achieve higher Essential Eight maturity levels for several reasons:
- Evolving threat landscape: Since cyber threats are constantly evolving, businesses need to adapt their cybersecurity measures accordingly.
- Regulatory requirements: Industry regulations may require businesses to maintain a certain level of cybersecurity maturity.
- Risk mitigation: Higher maturity levels can help mitigate the risks associated with cyberattacks and data breaches.
- Business continuity: Moreover, a strong cybersecurity posture is essential for ensuring business continuity and resilience.
For a more detailed explanation of the Essential Eight maturity model, please refer to our comprehensive article, “Essential Eight Maturity Model Explained.”
Tools and Technologies for the Essential Eight
Once you grasp what is Essential 8, let’s explore how to implement it effectively. Implementing the Essential Eight requires a combination of technical controls and administrative measures. Here’s how various tools and technologies can support your efforts:
Essential Eight Strategy | Tools and Technologies |
Patch application | * Patch management software * Automated deployment tools |
Restricting administrative rights | * User account management tools * Role-based access control (RBAC) |
User application hardening | * Application whitelisting * Group Policy settings |
Regular backups | * Backup software * Cloud storage solutions |
Patching of third-party software | * Automated patch management tools * Vendor updates |
Application whitelisting | * Application whitelisting software * Endpoint security solutions |
Web browsing controls | * Secure web gateways * Content filtering solutions |
Multi-factor authentication (MFA) | * MFA software * Multi-factor authentication apps |
Here are some examples of popular tools and technologies used in Australia to implement the Essential 8 strategies:
Patch Application
- Patch Management Software:
- Microsoft Intune: This cloud-based solution manages Windows devices, including patch management.
- Ivanti Patch Management: A comprehensive solution for managing patches across various operating systems and applications.
- Automated Deployment Tools:
- Ansible: An open-source tool that automates patch deployment.
- Chef: Another popular tool for automating IT tasks, including patch deployment.
Restricting Administrative Rights
- User Account Management Tools:
- Active Directory: A Microsoft service used for managing user accounts and permissions.
- Azure Active Directory: A cloud-based service offering advanced user management features.
- Role-Based Access Control (RBAC):
- IAM Solutions: Identity and access management solutions like Okta, SailPoint, and CyberArk provide RBAC capabilities.
User Application Hardening
- Application Whitelisting:
- AppLocker (Windows): A built-in tool that controls which applications can run on Windows devices.
- Whitelisting Solutions: Dedicated solutions like Deep Instinct and Carbon Black offer granular control over application execution.
- Group Policy Settings:
- Microsoft Group Policy: Used to configure Windows settings, including application restrictions and security policies.
Regular Backups
- Backup Software:
- Cloud Storage Solutions:
- Amazon S3: A scalable cloud storage service from Amazon Web Services.
- Microsoft Azure Blob Storage: A similar cloud storage service from Microsoft.
Patching of Third-Party Software
- Automated Patch Management Tools:
- Ivanti Patch Management: Manages patches for third-party applications as well.
- Tanium: A platform for endpoint management and security, including patch management.
- Vendor Updates:
- Also regularly check vendor websites for updates and patches for third-party software.

Application Whitelisting
- Application Whitelisting Software:
- Deep Instinct: A machine learning-based platform that includes application whitelisting.
- Carbon Black: An endpoint security platform with application control features.
- Endpoint Security Solutions:
- CrowdStrike: A cloud-native endpoint protection platform offering application control.
- SentinelOne: Another endpoint security solution with application whitelisting capabilities.
Web Browsing Controls
- Secure Web Gateways:
- Zscaler: A cloud-based gateway that filters and inspects web traffic.
- Palo Alto Networks: A network security vendor offering secure web gateways.
- Content Filtering Solutions:
- Symantec Web Security: A solution that blocks malicious websites and content.
Multi-Factor Authentication (MFA)
- MFA Software:
- Okta: An identity and access management platform providing MFA capabilities.
- Duo Security: A cloud-based MFA provider.
- Multi-Factor Authentication Apps:
- Google Authenticator: A popular app available for smartphones and tablets.
- Microsoft Authenticator: Another widely used MFA app from Microsoft.
So these are just a few examples of the many tools and technologies available in Australia to implement the Essential Eight strategies. Without doubt, the best choice for a business will depend on factors such as size, budget, and specific requirements.
Choosing the Right Tools
Selecting the right tools depends on several factors, including:
- Business size and needs: Smaller businesses may benefit from cost-effective, user-friendly solutions. On the other hand, larger businesses with complex IT environments may need more comprehensive tools.
- Budget: Tools vary in cost. Some options are free or open-source. Therefore, evaluate which tools fit your budget.
- Technical expertise: Consider your in-house IT capabilities. Additionally, assess if you need extra technical support.
Best Practices:
- Start with a Gap Analysis: Firstly, identify gaps in your current cybersecurity posture. Consequently, choose tools that address these specific needs.
- Interoperability: Secondly, ensure that selected tools work seamlessly together. This approach will lead to more efficient management of your systems.
- Scalability: Thirdly, consider future growth and choose tools that can scale with your business needs. Thus, you will be prepared for expansion.
- Ongoing monitoring and updates: Lastly, continuously monitor your tools. Also, keep them up-to-date with the latest threats and vulnerabilities.
Additional Resources:
Provides a range of resources on their website. This includes tools and technologies for implementing the Essential 8.
By prioritising cybersecurity, you can protect your business’s future and build a more resilient organisation.
Conclusion
The Essential Eight provides a comprehensive framework for businesses to improve their cybersecurity setup and protect themselves from the growing threat of cyberattacks. By clear understanding what is essential 8, and implementing these strategies, businesses can reduce the risk of data breaches, financial losses, and reputational damage.
So don’t wait for a cyberattack to happen. Take proactive steps indeed to protect your business by adopting the Essential 8. Netcomp, with over 20 years of experience in IT and cybersecurity, can help you successfully implement these strategies. We offer tailored solutions that align with your unique business needs and budget.
Contact us today to discuss your options and learn how we can help you achieve a higher level of cybersecurity maturity.



