Your Business Is Under Attack—And Traditional Security Isn’t Enough
Alarmingly, cybercriminals stole over $152.6 million from Australian businesses through Business Email Compromise (BEC) in 2024. Moreover, that’s a staggering 66% increase from the previous year’s losses. Meanwhile, BEC now ranks among the top three self-reported cybercrimes affecting Australian businesses.
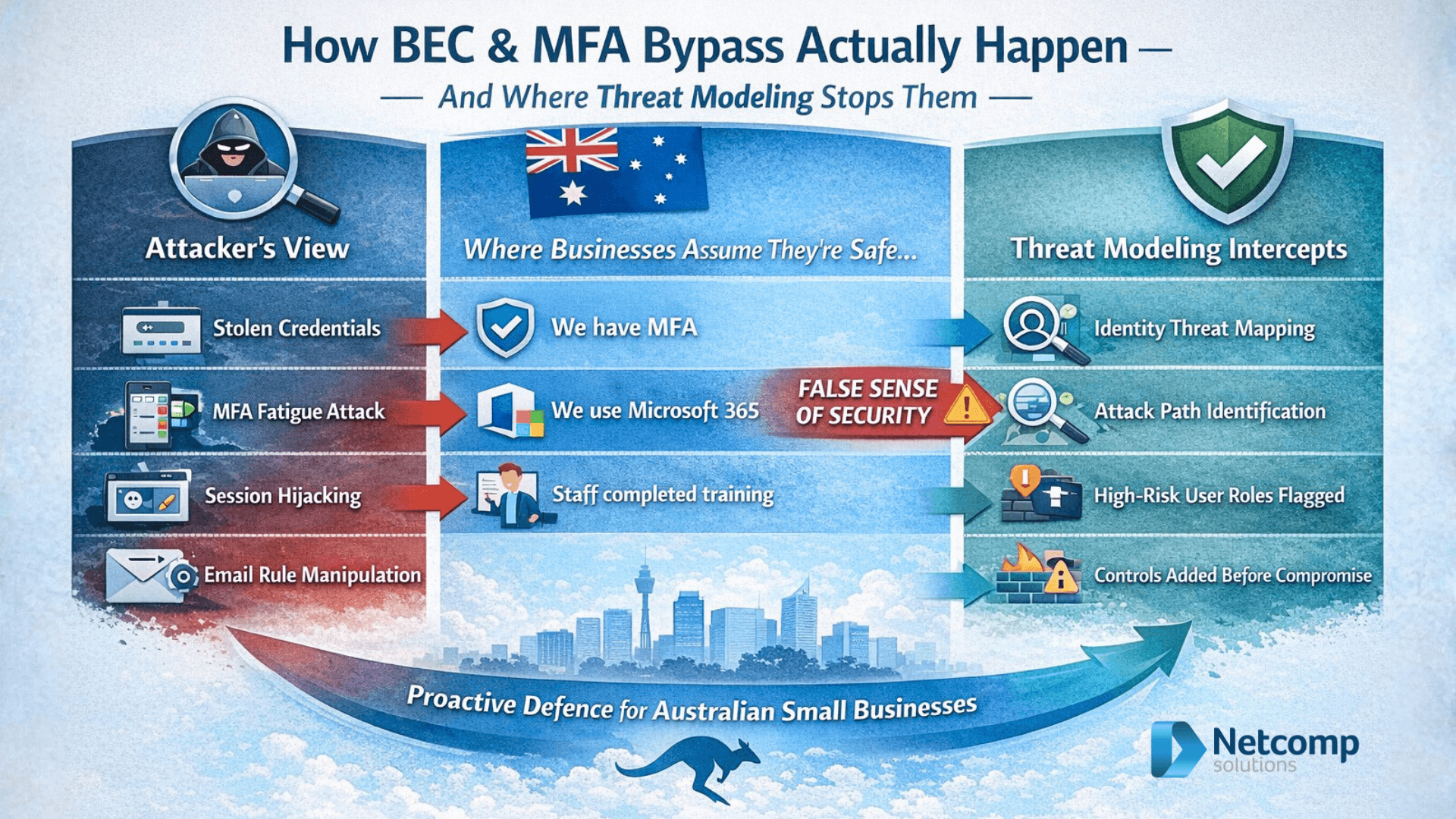
Additionally, here’s the truly alarming part that keeps IT professionals awake at night. Specifically, 50% of cybersecurity incident responses in early 2024 involved MFA bypass attacks. Therefore, even when businesses implement multi-factor authentication, attackers simply find new ways around it.
Consequently, small Australian businesses face average losses of $49,600 per cybercrime incident, according to the Australian Signals Directorate. Furthermore, these costs continue climbing year after year. Thus, traditional reactive security measures simply cannot keep pace with evolving threats.
Nevertheless, there’s a systematic approach that can help your business stay ahead. Importantly, threat modeling identifies weaknesses before attackers exploit them. Ultimately, this proactive defence strategy is becoming essential for Australian business survival.
Understanding the BEC Crisis Facing Australian Businesses
What Makes BEC So Devastating
Essentially, Business Email Compromise involves cybercriminals either impersonating trusted contacts or infiltrating email systems. Subsequently, they trick employees into transferring funds or revealing sensitive information. Meanwhile, the average BEC loss reached $55,000 per confirmed incident in Australia.
Moreover, BEC attacks specifically target the human vulnerability in your security chain. Consequently, no amount of traditional firewalls or antivirus software can fully protect against them. Additionally, these attacks have become increasingly sophisticated with AI-generated content.
Remarkably, 40% of BEC phishing emails in 2024 were flagged as AI-generated. Therefore, attackers now create highly convincing messages with perfect grammar and contextual awareness. Furthermore, they research your business relationships and communication patterns beforehand.
Why Small Businesses Are Prime Targets
Specifically, small businesses often lack dedicated IT security teams and comprehensive training programs. Meanwhile, 91% of Australian small business owners haven’t invested in tailored cybersecurity measures. Consequently, cybercriminals view them as easier targets with valuable assets.
Additionally, small businesses frequently conduct high-value transactions without robust verification processes. Therefore, a single successful BEC attack can devastate cash flow and operations. Moreover, recovery costs extend far beyond the initial financial loss.
The Multi-Factor Authentication Illusion
MFA Isn’t the Silver Bullet You Think It Is
Previously, implementing MFA seemed like the ultimate security solution for Australian businesses. However, research shows almost half of all account takeovers involved accounts with MFA configured. Nevertheless, 89% of security professionals still consider MFA complete protection against account takeover.
Furthermore, this dangerous overconfidence creates a false sense of security. Meanwhile, attackers have developed numerous sophisticated bypass techniques. Consequently, businesses relying solely on MFA face unexpected vulnerabilities.
Common MFA Bypass Techniques Targeting Australians
Specifically, MFA fatigue attacks involve bombarding users with repeated authentication notifications. Eventually, frustrated employees approve requests just to stop the interruptions. Moreover, 25% of incident responses involved fraudulent MFA push notifications.
Additionally, attackers use adversary-in-the-middle attacks through reverse proxy servers. Consequently, they intercept both login credentials and authentication cookies from legitimate sites. Meanwhile, victims believe they’re interacting with authentic websites.
Furthermore, session hijacking allows attackers to steal cookies that store authentication data. Subsequently, they bypass MFA checkpoints entirely by taking over active sessions. Moreover, these techniques become easier with readily available Phishing-as-a-Service toolkits.
Similarly, SIM swapping attacks target SMS-based MFA by tricking mobile carriers. Therefore, attackers receive your authentication codes directly on their devices. Additionally, social engineering tricks IT departments into resetting credentials or modifying authentication methods.
What Is Threat Modeling and Why Australian Businesses Need It
The Strategic Approach to Proactive Security
Essentially, threat modeling is a structured process for identifying potential security threats before they materialise. Moreover, it helps teams understand how attackers might exploit weaknesses in their systems. Therefore, businesses can prioritise defences based on actual risk.
Furthermore, threat modeling provides a clear line of sight across your entire security posture. Consequently, security decisions become rational and data-driven rather than reactive. Additionally, it produces an assurance argument that justifies security investments to stakeholders.
Importantly, threat modeling works by systematically answering four fundamental questions. Initially, teams identify what they’re building and protecting. Subsequently, they determine what could go wrong. Moreover, they develop strategies to defend against identified threats. Finally, they validate that preventive measures are actually working.
How Threat Modeling Differs from Traditional Security
Previously, traditional security approaches waited for incidents to occur before responding. However, threat modeling anticipates attacks during the design phase. Meanwhile, this proactive stance dramatically reduces both likelihood and impact of successful breaches.
Additionally, traditional security often focuses narrowly on technical controls like firewalls. Conversely, threat modeling examines entire business processes, workflows, and human factors. Therefore, it identifies systemic weaknesses that purely technical solutions miss.
Furthermore, threat modeling is continuous rather than one-time. Consequently, it evolves alongside your business systems and emerging attack methods. Moreover, this ongoing assessment keeps pace with rapidly changing threat landscapes.
The Simple 4-Step Threat Modeling Framework for Non-Technical Managers
Step 1: Map Your Business Processes and Data Flows
Initially, create a visual representation of how information moves through your organisation. Specifically, identify where customer data enters, gets processed, and exits your systems. Meanwhile, note who has access at each stage.
Furthermore, document your communication workflows, especially around financial transactions and sensitive data. Consequently, you’ll understand which processes cybercriminals might target. Additionally, this mapping reveals unexpected complexity in seemingly simple operations.
Moreover, focus on high-value transactions and privileged access points. Therefore, start with your accounts payable processes, customer database access, and executive email accounts. Subsequently, expand to other business-critical workflows.
Step 2: Identify Your Crown Jewels and Attack Surfaces
Specifically, determine which assets would cause maximum damage if compromised. Generally, this includes customer databases, financial systems, and intellectual property. Meanwhile, consider regulatory compliance requirements and reputational risks.
Additionally, identify all points where external parties interact with your systems. Therefore, examine email gateways, web applications, vendor portals, and remote access systems. Furthermore, employee devices and home networks represent significant attack surfaces for remote workers.
Moreover, consider human factors and social engineering vulnerabilities. Consequently, assess which employees handle sensitive transactions or have elevated privileges. Additionally, evaluate your training effectiveness and security awareness culture.
Step 3: Think Like an Attacker and Identify Realistic Threats
Subsequently, consider how a motivated attacker would exploit your identified weaknesses. Specifically, use the STRIDE framework to systematically evaluate threats. Meanwhile, STRIDE covers Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of privilege.
Furthermore, consider BEC-specific attack paths relevant to Australian businesses. Therefore, ask: How could someone impersonate your CEO via email? Additionally, what would happen if an attacker compromised your accounts payable email? Moreover, how could they bypass your MFA implementation?
Importantly, prioritise threats based on both likelihood and potential business impact. Consequently, focus on high-probability scenarios with severe consequences first. Additionally, consider attack chains where one compromise enables another.
Step 4: Develop and Test Practical Countermeasures
Finally, design specific controls to mitigate your highest-priority threats. Importantly, these should address systemic weaknesses rather than just symptoms. Meanwhile, ensure countermeasures are practical for your team to implement and maintain.
Specifically, implement multiple verification steps for financial transactions above certain thresholds. Therefore, require phone call confirmation using pre-established contact numbers—not those in suspicious emails. Additionally, create clear escalation procedures for unusual requests.
Furthermore, implement technical controls that complement human judgment rather than replacing it. Consequently, use email authentication protocols like DMARC, SPF, and DKIM. Moreover, deploy phishing-resistant MFA methods like hardware security keys for privileged accounts.
Additionally, regularly test your countermeasures through simulated attacks and social engineering exercises. Therefore, validate that employees actually follow established procedures under pressure. Moreover, refine processes based on testing outcomes.
Specific Threat Modeling Applications for BEC Prevention
Modelling Email Compromise Attack Paths
Initially, map all potential entry points where attackers could compromise email accounts. Specifically, consider weak passwords, phishing susceptibility, and malware infections. Meanwhile, identify which accounts would provide maximum value to attackers.
Subsequently, trace how an attacker could leverage one compromised account to access others. Therefore, examine shared credentials, password reuse patterns, and administrative privileges. Additionally, consider how attackers might maintain persistence undetected.
Furthermore, model scenarios where attackers impersonate executives or vendors without directly compromising accounts. Consequently, evaluate your verification processes for detecting spoofed email addresses. Moreover, assess whether employees can identify subtle impersonation indicators.
Addressing MFA Bypass Vulnerabilities Through Threat Modeling
Specifically, examine how your current MFA implementation could be circumvented. Therefore, identify whether you’re using SMS-based codes vulnerable to SIM swapping. Additionally, assess your susceptibility to MFA fatigue attacks.
Moreover, model adversary-in-the-middle scenarios where attackers intercept authentication. Consequently, determine whether your MFA method prevents session hijacking. Furthermore, evaluate fallback authentication methods that might bypass MFA entirely.
Additionally, consider social engineering attacks targeting your IT helpdesk or support team. Therefore, assess procedures for password resets and authentication method changes. Moreover, identify whether attackers could trick staff into modifying security settings.
Practical Implementation: Making Threat Modeling Work for Your Business
Starting Small: Quick Wins for Australian SMEs
Initially, begin with a focused pilot project rather than attempting comprehensive organisational coverage. Specifically, choose your most critical business process, such as payment authorisations. Meanwhile, assemble a small cross-functional team including finance, IT, and operations staff.
Furthermore, schedule just two hours for your first threat modeling session. Consequently, this manageable timeframe prevents overwhelming your team. Additionally, use this session to map the chosen process and identify obvious vulnerabilities.
Moreover, prioritise implementing three immediate countermeasures from your initial session. Therefore, focus on high-impact, low-cost controls that address specific threats. Subsequently, measure and communicate the effectiveness of these quick wins.
Building Internal Capability Without Expensive Consultants
Importantly, Australian businesses can develop threat modeling expertise internally through free resources. Specifically, OWASP provides comprehensive threat modeling guides and frameworks available at no cost. Meanwhile, these materials offer structured approaches suitable for beginners.
Additionally, leverage Australian government resources like the Australian Cyber Security Centre’s guidance. Therefore, access tailored advice specifically addressing threats facing Australian businesses. Moreover, these resources include practical implementation frameworks.
Furthermore, designate one team member as your internal threat modeling champion. Consequently, this person coordinates sessions, maintains documentation, and tracks countermeasure implementation. Additionally, they stay current on emerging threats relevant to your industry.
Integrating Threat Modeling into Existing Business Processes
Subsequently, incorporate threat modeling checkpoints into your existing workflows rather than creating separate processes. Specifically, include threat assessment when onboarding new systems or vendors. Meanwhile, this prevents introducing new vulnerabilities.
Moreover, conduct brief threat model reviews during regular team meetings. Therefore, dedicate 15 minutes monthly to discussing emerging threats and updating countermeasures. Additionally, this maintains security awareness without requiring separate sessions.
Furthermore, link threat modeling outcomes directly to your existing risk register. Consequently, security threats receive the same governance and tracking as other business risks. Moreover, this integration ensures executive visibility and accountability.
The Defence-in-Depth Advantage
Importantly, threat modeling naturally creates layered security that compensates for individual control failures. Specifically, when one defence mechanism fails, others provide backup protection. Meanwhile, this redundancy dramatically reduces successful attack likelihood.
Furthermore, threat modeling identifies dependencies between different security controls. Consequently, you understand which combinations provide strongest protection. Additionally, this reveals single points of failure requiring additional countermeasures.
Moreover, threat modeling helps prioritise limited security budgets based on actual risk reduction. Therefore, investments focus on controls providing maximum protection for critical assets. Subsequently, even small businesses achieve significant security improvements with modest resources.
Common Misconceptions About Threat Modeling in Australia
“Threat Modeling Is Too Technical for Small Business”
Actually, threat modeling focuses primarily on understanding business processes and risks. Specifically, non-technical managers possess essential knowledge about workflows and vulnerabilities. Meanwhile, technical details remain secondary to business context.
Furthermore, simplified frameworks make threat modeling accessible to everyone. Consequently, you don’t need cybersecurity certifications to identify how attackers might exploit your processes. Additionally, involving diverse team members provides valuable perspectives that security specialists miss.
Moreover, the four-question framework translates complex security concepts into practical business terms. Therefore, discussions centre on business impact rather than technical jargon. Subsequently, threat modeling becomes a business risk management activity, not purely technical exercise.
“We’re Too Small to Need Formal Threat Modeling”
Conversely, small businesses face disproportionate targeting precisely because attackers assume inadequate defences. Specifically, 43% of all cyberattacks specifically target small businesses. Meanwhile, small businesses often handle transactions and data as valuable as larger enterprises.
Additionally, informal threat consideration already happens naturally in well-run businesses. Therefore, threat modeling simply structures and documents existing thought processes. Furthermore, this documentation enables consistent decision-making and knowledge transfer.
Moreover, threat modeling prevents the costly reactive approach of implementing random security controls. Consequently, limited budgets focus on protections addressing your specific threats. Additionally, this targeted approach delivers better outcomes than expensive but mismatched security solutions.
“Compliance Frameworks Already Cover Our Security Needs”
However, compliance frameworks establish minimum baselines rather than addressing your specific vulnerabilities. Specifically, generic requirements don’t account for your unique business processes and attack surfaces. Meanwhile, compliance doesn’t guarantee protection against evolving threats like BEC.
Furthermore, threat modeling complements compliance by identifying gaps in standard frameworks. Consequently, you understand where additional controls are necessary beyond compliance minimums. Additionally, threat modeling provides evidence demonstrating due diligence to regulators and insurers.
Moreover, compliance frameworks rarely address sophisticated social engineering and BEC tactics. Therefore, businesses passing compliance audits still suffer devastating BEC losses. Subsequently, threat modeling fills critical gaps that compliance overlooks.
Tools and Resources for Australian Businesses
Free Threat Modeling Tools and Templates

Initially, start with simple spreadsheet-based threat modeling templates before investing in specialised tools. Specifically, Microsoft Excel or Google Sheets provide sufficient functionality for most small businesses. Meanwhile, these familiar tools eliminate learning curves.
Additionally, OWASP Threat Dragon offers free, open-source threat modeling software. Therefore, teams can create visual diagrams and track threats without licensing costs. Furthermore, it supports multiple frameworks including STRIDE and LINDDUN.
Moreover, the Australian Cyber Security Centre provides free resources specifically for Australian businesses. Consequently, access guidance addressing threats relevant to your regulatory environment. Additionally, these materials include practical checklists and assessment tools.
Connecting with Australian Cybersecurity Communities
Furthermore, join local industry associations offering cybersecurity working groups and information sharing. Specifically, organisations like AusCERT provide threat intelligence relevant to Australian businesses. Meanwhile, these communities share emerging attack patterns and effective countermeasures.
Additionally, participate in Australian Cyber Security Centre’s Cyber Threat Intelligence Sharing program. Therefore, benefit from collective threat intelligence across hundreds of organisations. Moreover, your own incident reports help other Australian businesses defend themselves.
Subsequently, attend local cybersecurity events and workshops in major Australian cities. Consequently, network with peers facing similar challenges and share practical solutions. Additionally, these connections provide ongoing support as threats evolve.
When to Engage Professional Threat Modeling Services
Importantly, consider professional assistance when addressing particularly complex or critical systems. Specifically, engage specialists for core financial systems, customer databases, or regulated infrastructure. Meanwhile, professionals bring experience from diverse threat scenarios.
Additionally, professional services prove valuable when establishing your initial threat modeling capability. Therefore, consultants can train your team while conducting actual threat assessments. Furthermore, this knowledge transfer builds internal capability for ongoing threat modeling.
Moreover, periodic professional reviews validate and improve your internal threat modeling efforts. Consequently, external perspectives identify blind spots your team might miss. Additionally, professionals stay current on emerging attack techniques and industry best practices.
Building a Sustainable Threat Modeling Practice
Creating Your Threat Modeling Roadmap
Initially, document your current security posture before beginning formal threat modeling. Specifically, inventory existing controls, known vulnerabilities, and recent security incidents. Meanwhile, this baseline enables measuring threat modeling effectiveness.
Subsequently, prioritise systems for threat modeling based on business criticality and threat exposure. Therefore, start with processes handling financial transactions, customer data, or regulatory compliance. Additionally, address systems with recent security concerns or upcoming changes.
Furthermore, establish a regular threat modeling schedule rather than one-time assessments. Consequently, conduct quarterly reviews of critical systems and annual reviews of standard systems. Moreover, perform threat modeling whenever significant system changes occur.
Measuring Threat Modeling Effectiveness
Specifically, track metrics demonstrating threat modeling value to business stakeholders. Therefore, measure identified threats, implemented countermeasures, and prevented incidents. Additionally, calculate potential financial losses avoided through proactive defences.
Moreover, monitor security incident trends before and after implementing threat modeling. Consequently, demonstrate whether your targeted countermeasures actually reduce successful attacks. Furthermore, these metrics justify continued investment and resource allocation.
Additionally, assess employee security awareness improvements resulting from threat modeling participation. Therefore, evaluate whether team members better recognise and report suspicious activities. Moreover, improved awareness represents a significant cultural security benefit.
Adapting to Emerging Threats
Importantly, maintain awareness of evolving attack techniques affecting Australian businesses. Specifically, subscribe to threat intelligence feeds from Australian Signals Directorate and security vendors. Meanwhile, these sources highlight new BEC tactics and MFA bypass methods.
Furthermore, regularly update your threat models as attack techniques evolve. Consequently, assess whether existing countermeasures still address current threat methods. Additionally, identify new vulnerabilities introduced by business changes or technology adoption.
Moreover, participate in industry information sharing about observed attack patterns. Therefore, your experiences help other Australian businesses while benefiting from their lessons. Subsequently, this collective defence strengthens the entire Australian business community.
Taking Action: Your Next Steps
Immediate Actions for This Week
Initially, schedule your first threat modeling session within the next seven days. Specifically, block two hours on calendars for key stakeholders. Meanwhile, choose one critical business process as your starting point.
Additionally, review one recent email requesting payment or sensitive information. Therefore, identify what verification steps could have detected a potential BEC attempt. Moreover, document these observations for discussion in your threat modeling session.
Furthermore, audit your current MFA implementation for bypass vulnerabilities. Consequently, identify accounts using SMS-based authentication requiring upgrades. Additionally, assess whether your IT helpdesk has procedures preventing social engineering attacks.
Building Long-Term Security Resilience
Subsequently, commit to quarterly threat modeling reviews as standard business practice. Therefore, integrate security assessment into your regular business planning cycles. Moreover, allocate specific budget for implementing priority countermeasures.
Additionally, invest in ongoing security awareness training for all employees. Consequently, transform your workforce into an active defence layer rather than vulnerability. Furthermore, regular training keeps BEC tactics and verification procedures fresh in minds.
Moreover, establish relationships with Australian cybersecurity resources and communities. Therefore, access ongoing support as threats evolve beyond your initial threat model. Additionally, these connections provide rapid assistance during actual security incidents.
Conclusion: Proactive Defence Is Your Competitive Advantage
Ultimately, Australian businesses face an escalating cyber threat landscape with sophisticated BEC attacks and MFA bypasses. Nevertheless, threat modeling provides a systematic, accessible approach for identifying vulnerabilities before exploitation. Moreover, this proactive strategy delivers significantly better outcomes than reactive security approaches.
Importantly, threat modeling doesn’t require large budgets or technical expertise to begin. Specifically, the simple four-step framework enables any business to start protecting critical assets immediately. Meanwhile, even modest threat modeling efforts substantially reduce BEC risk and financial losses.
Furthermore, businesses implementing threat modeling demonstrate due diligence to insurers, regulators, and customers. Consequently, this systematic approach to security management provides competitive advantages beyond technical protection. Additionally, the process builds organisational security awareness and resilience.
Therefore, the question isn’t whether you can afford threat modeling—it’s whether you can afford not implementing it. Specifically, with average BEC losses exceeding $55,000 and small business incident costs approaching $50,000, prevention dramatically outweighs implementation costs. Moreover, threat modeling provides ongoing value as your business and threats evolve.
Finally, start your threat modeling journey today rather than waiting for the inevitable security incident. Subsequently, protect your business, employees, and customers through systematic vulnerability identification. Furthermore, join the growing community of Australian businesses using threat modeling to stay ahead of increasingly sophisticated cyber threats.
About Netcomp Solutions
Netcomp Solutions provides comprehensive IT support services specifically designed for Australian small businesses. We help organisations implement practical cybersecurity measures including threat modeling, BEC prevention, and advanced authentication strategies. Contact us to discuss how we can strengthen your business security posture.
Ready to protect your business from BEC attacks? Contact Netcomp Solutions today for a complimentary threat modeling consultation and security assessment tailored to your Australian business needs.



