Do you ever get random email from unidentified email addresses claiming you’ve won something, encouraging you to do a survey to win a prize, consisting of links to unverified websites? If the answer is “yes” then these emails are created in order to gain vital information of the user. The user who doesn’t have an understanding about the difference between a legitimate and non-legitimate email address will lean towards becoming a victim easily. However, the user cannot be blamed completely since these emails and the content involved look genuinely trustworthy due to factors which will be discussed below.
Installing a malware to threaten user’s information
Malware consists of software variants which include viruses, ransomware and spyware. This can cause extensive damage to data and gain access to user’s private information. The image below shows how a phishing email looks like.
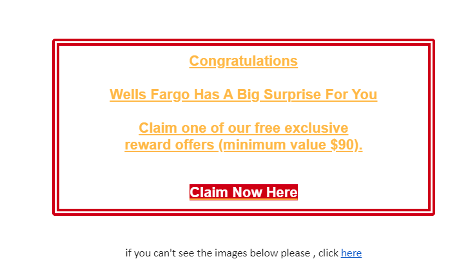
What will a phishing email contain?
A phishing email will contain a suspicious link attached to it, will be conveying a congratulatory message or content that will attract the user which will mostly be claiming a “reward”, will look legitimate and persuasive with words such as “free”, “offer”. Phishing emails are compiled to attract vulnerable users and these keywords are some ways of identifying phishing emails. The email will arouse urgency and might push you to complete a task and the user should be concerned at that point because it’s one element of a phishing email. If the email seems suspicious the first thing the user should do is to check the domain name carefully and do an internet search or compare it with emails you find legitimate and use on a daily basis. The below given image shows a suspicious domain name but appears to be legitimate.
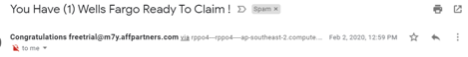
However, to be on the safe side, the user should do one of the actions mentioned above. Another way to identify a phishing email is spelling mistakes and incorrect grammar but this rarely happens in the present world since phishing attacks are much more advanced. The scammers will pretend from mimicking the branding, email formatting to logos which makes it more valid.
In conclusion, phishing emails are scammers pretending to be a legitimate organisation which holds confidential information of a user to gain the real data from the user. It varies from gaining personal details, bank account details or other useful information. It’s always best to do a background check of the email you receive starting from the domain name to the content to find out the legitimacy. Installing web services which identifies malicious services will help in decreasing the amount of phishing emails entering your inbox and the user will get to know if the content is safe or unsafe.