As we continue to make advancements in technology and become ever more connected, cybersecurity incidents have increased dramatically. Cyberattacks can result in data breaches, destruction of company information or intellectual property, sabotage of operational networks, and financial losses. Despite the security precautions taken by businesses today, cyber-incidents remain a serious threat. Even though it’s difficult to anticipate when an incident will take place, organisations must still prepare for one. As an Australian company, safeguarding your organisation against such attacks is not just a best practice but also a requirement under the government’s Essential Eight risk management regulations.
In this article, we will delve into the crucial topic of cyber incident response, exploring the necessary steps and best practices to effectively manage and recover from security breaches. Additionally, we will provide you with the brief understanding of various types of cyber attacks will be vital in formulating an efficient incident response plan.
Types of Cyber Attacks
Cyber attacks come in various forms, each with its own unique objectives and methods.
Distributed Denial of Service (DDoS) attacks
One common attack is the Distributed Denial of Service (DDoS) attack, which overwhelms a target’s servers with an excessive amount of traffic, causing disruptions and downtime.
Phishing attacks
Phishing attacks involve deceptive emails or messages designed to trick recipients into revealing sensitive information, such as login credentials or financial details.
Ransomware
Another prevalent threat is ransomware, where attackers encrypt critical data and demand a ransom for its release, causing severe disruptions to operations.
Malware
Malware, including viruses, worms, and trojans, infects systems to steal data, disrupt services, or gain unauthorised access. Insider threats involve malicious actions taken by employees or individuals with access to the company’s network, while social engineering exploits human psychology to manipulate individuals into divulging sensitive information.
Incident Response Planning
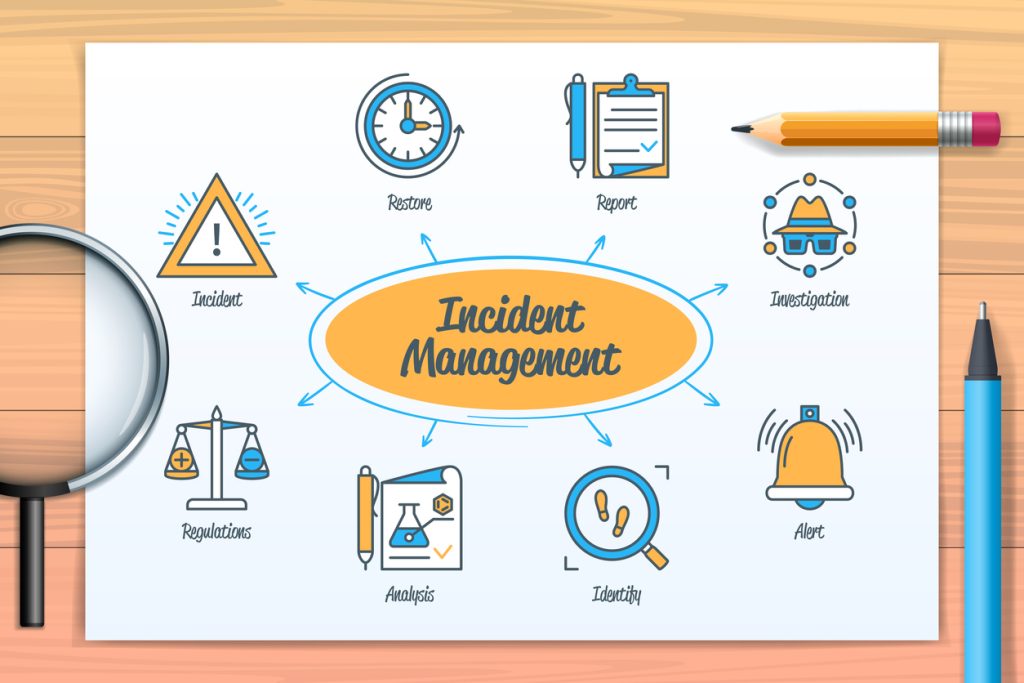
Preparation is key to mitigating the impact of a cyber incident. Develop a comprehensive incident response plan tailored to your organisation’s specific needs. This plan should outline the roles and responsibilities of each team member during a breach, establish communication channels, and define escalation procedures.
Threat Containment:
When an incident occurs, swift containment is essential to prevent further damage. Identify the source and scope of the breach and take immediate action to isolate affected systems. This can involve disabling compromised accounts, closing security gaps, and quarantining infected devices.
Digital Forensics:
Engaging in digital forensics can provide valuable insights into the nature of the cyberattack. Work with experienced cybersecurity professionals to analyse the breach thoroughly. Collect and preserve digital evidence to aid in understanding the attack and identifying potential weaknesses in your defense.
Communication Strategies:
Effective communication is crucial during a cyber incident. Inform all stakeholders, including employees, customers, and partners, about the situation promptly and transparently. Maintaining clear and open lines of communication can help build trust and prevent misinformation from spreading.
Engage Expert Support:
Certainly, recovering from a cyber incident requires specialised expertise. Partner with reputable IT security firms or consultants to guide your organisation through the recovery process. Their experience and knowledge can be invaluable in restoring normalcy and enhancing your cybersecurity measures.
Employee Education and Training:
Undoubtedly, human error is a leading cause of security breaches. Regularly educate your employees about the latest cybersecurity threats and best practices. Encourage them to adopt strong password policies, avoid phishing attempts, and report any suspicious activities promptly.
Regular Testing and Improvement:
Analyse and improve your cybersecurity defenses continually. Conduct simulated cyber incident response drills to evaluate the effectiveness of your plan and identify areas for improvement. Stay up-to-date with the latest security technologies and threat intelligence to adapt your defense strategy accordingly.
Through effective cyber incident response planning, your organisation can be more agile and resilient in the face of a security breach. Surely, the active implementation of the Essential Eight risk management regulations, combined with a reliable IT provider, is the surest way to reinforce your cybersecurity measures and protect your assets and data. With Netcomp Solutions as your partner in cyber defence, you can have the confidence that your business is equipped with the best solutions to tackle emerging threats through state-of-the-art security systems and proactive incident response plans. So take action now to secure the future of your organisation — contact us now to protect your business from potential cyber attacks.