In today’s digital age, Australian businesses of all sizes face a constant barrage of cyber threats. Malicious actors are constantly developing new techniques to exploit vulnerabilities and gain access to sensitive data. This can have devastating consequences, leading to financial losses, reputational damage, and operational disruption.
Fortunately, there are steps businesses can take to mitigate these risks. The Australian Signals Directorate (ASD) has developed the Essential 8 Maturity Model, a framework that outlines eight key mitigation strategies to bolster your organisation’s cyber defences. This article delves into the Essential Eight, explores the Maturity Model, and provides guidance for Australian businesses looking to enhance their cyber security posture.

What is Essential 8 all about?
The Essential 8 is a set of eight essential mitigation strategies designed to help Australian businesses strengthen their cyber defences and protect themselves from common cyber attacks. It’s like a checklist for basic cyber hygiene practices. Let’s break down each strategy in detail:
- Application Control: This strategy focuses on regulating the software applications that run within your network. By implementing application control measures, you can restrict users from installing or running unauthorized applications. This significantly reduces the attack surface and minimizes the risk of malware infections. There are two primary approaches to application control: whitelisting and blacklisting. Whitelisting allows only authorized applications to run, while blacklisting explicitly prohibits specific applications deemed risky.
- Patch Applications: Keeping your applications up-to-date with the latest patches is crucial for maintaining a robust cyber security posture. Software vendors regularly release patches to address vulnerabilities in their applications. These vulnerabilities attackers can exploit to gain unauthorised access to systems or steal data. By implementing a comprehensive patch management program, you can ensure that your applications are patched promptly, minimising the window of opportunity for attackers.
- Microsoft Office Macro Control: Microsoft Office applications, such as Word and Excel, have a feature called macros that allows users to automate repetitive tasks. However, attackers can also use macros to deliver malware. The Essential Eight recommends restricting the use of macros to essential and trusted instances only. This can be achieved through Group Policy settings or by disabling macros entirely for users with a lower risk profile.
- User Application Hardening: This strategy involves configuring settings within web browsers, email clients, and other applications to minimize their attack surface. Techniques include disabling unnecessary features and functionalities, such as Java or ActiveX scripting, which can attackers exploit. Additionally, configuring security-focused browser settings, such as blocking pop-ups and automatically updating plugins, can further enhance your security posture.
- Restrict Administrative Privileges: The principle of least privilege dictates that users should only get the minimum level of access required to perform their jobs. This applies especially to administrative privileges, which grant users extensive control over systems and data. By restricting the number of users with administrative access and implementing controls for granting, reviewing, and revoking such privileges, you can significantly reduce the potential for insider threats and privilege escalation attacks.
- Patch Operating Systems: Similar to patching applications, keeping your operating systems up-to-date with the latest security patches is essential. Operating system vulnerabilities can be exploited by attackers to gain a foothold on your systems and launch further attacks. A comprehensive patch management program for operating systems should include timely deployment of vendor-released patches, regular vulnerability scanning, and prioritizing critical vulnerabilities that require immediate attention.
- Multi-Factor Authentication (MFA): Multi-factor authentication (MFA) adds an extra layer of security to the login process. In addition to a username and password, MFA requires users to provide a second factor, such as a code from a mobile authenticator app or a fingerprint scan. This significantly increases the difficulty for attackers to gain unauthorized access to your systems, even if they manage to steal a user’s password. The Essential Eight emphasizes the importance of implementing phishing-resistant MFA options, especially for online services that store sensitive data.
- Regular Backups: Regularly backing up your data is vital for ensuring information resilience in the event of a cyber attack. Backups create copies of data that you can restore in case of data loss or corruption. The Essential Eight emphasizes the importance of prioritizing backups based on business criticality. Data that is essential for daily operations should be backed up more frequently and stored securely offsite to prevent them from being compromised alongside the primary data source.
What is Essential 8 Maturity Model all about?
The Essential 8 Maturity Model is a Australian-developed framework designed to help businesses of all sizes improve their cyber security posture. It outlines eight key strategies (the Essential Eight) and defines four maturity levels that represent progressive stages of implementation.
Here’s a breakdown of the key aspects:
- Essential Eight Strategies: These eight strategies address common cyber attack vectors and vulnerabilities, making it harder for attackers to gain access to your systems and data. They include actions like patching applications and operating systems, using multi-factor authentication, restricting administrative privileges, and implementing application control.
- Maturity Levels: The model defines four maturity levels, each representing a different level of cyber security implementation
Benefits of Implementing the Essential 8 Strategies
By implementing the Essential Eight strategies and achieving a higher maturity level in the Essential 8 Maturity Model, Australian businesses can reap numerous benefits:
- Reduced Risk of Cyber Attacks: The Essential Eight strategies address common attack vectors, making it more difficult for attackers to gain access to your systems and data.
- Improved Protection of Sensitive Data: By implementing strong security controls, you can safeguard sensitive data, such as customer information, financial records, and intellectual property.
- Enhanced Compliance with Regulations: Many Australian regulations, such as the Privacy Act 1988 and the Australian Cyber Security Measures Act 2018 (ACSC Act), mandate organizations to implement appropriate security controls to protect personal information. The Essential Eight aligns with these regulations, and demonstrably implementing these strategies can help organizations achieve compliance.
- Increased Business Continuity and Resilience: Cyber attacks can disrupt business operations and lead to significant downtime. By implementing the Essential Eight and having robust cyber security measures in place, businesses can minimize the impact of cyber incidents and recover more quickly.
- Improved Brand Reputation: Data breaches and other cyber security incidents can severely damage an organization’s reputation. By demonstrating a commitment to cyber security through the Essential Eight, businesses can build trust with customers and partners.
- Reduced Insurance Premiums: Many cyber insurance providers offer discounts to businesses that implement strong cyber security controls. Implementing the Essential Eight can demonstrate a proactive approach to cyber security and potentially lower your insurance premiums.
The Essential 8 Maturity Model: A Roadmap to Improvement
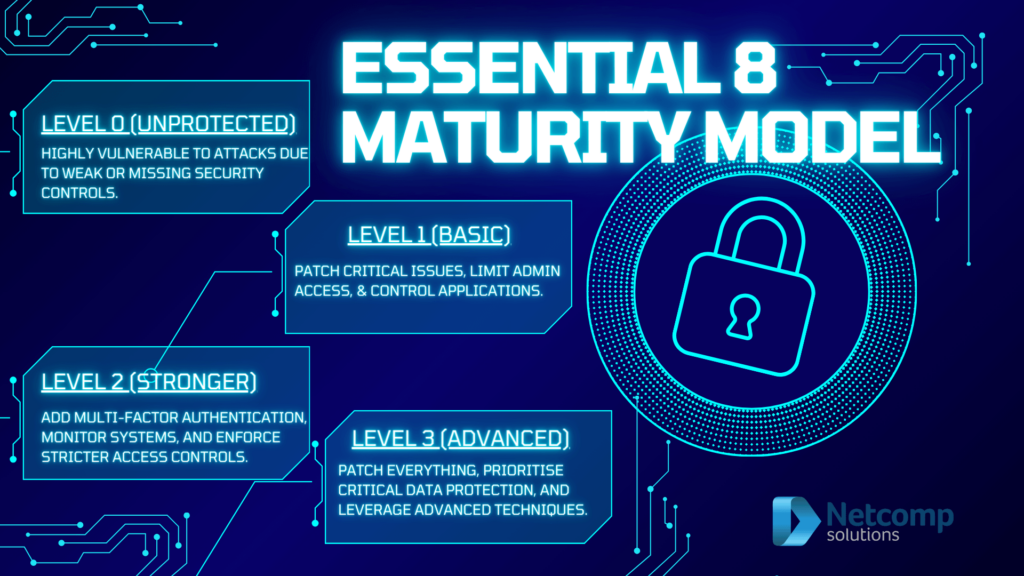
The Essential Eight Maturity Model goes beyond simply listing the eight mitigation strategies. It provides a framework for organisations to assess their current cyber security posture and identify areas for improvement. The model defines four distinct maturity levels:
- Maturity Level Zero (Ad-hoc): This level indicates significant weaknesses in cyber security defences. Organisations at this level may have no formal cyber security policies or procedures in place. And their systems and data are highly vulnerable to cyber attacks.
- Maturity Level One (Reactive): This level signifies that basic cyber security practices are implemented. But they may be reactive rather than proactive. Businesses at this level may have documented policies. But implementation may be inconsistent, and there may be a lack of awareness and training among employees.
- Maturity Level Two (Repeatable): This level reflects a more proactive approach to cyber security. Companies at this level have documented policies and procedures that they implement consistently. And they conduct regular security assessments and training programs for employees.
- Maturity Level Three (Proactive): This level represents the highest level of cyber security maturity. Organisations at this level continuously monitor their security posture. Moreover they proactively identify and address vulnerabilities, and have a well-defined incident response plan in place.
How to start with the Essential 8 Maturity Model
For Australian businesses looking to improve their cyber security posture, the Essential Eight Maturity Model provides a valuable roadmap. Here are some key steps to start:
- Conduct a Cyber Security Assessment: The first step is to gain a comprehensive understanding of your current cyber security posture. You can achieve this through an internal assessment or by engaging a qualified cyber security professional. The assessment should evaluate your existing controls against the eight Essential Eight strategies. It should also identify vulnerabilities and gaps, and determine your current maturity level.
- Develop a Cyber Security Strategy: Based on the findings of the assessment, develop a comprehensive cyber security strategy that outlines your goals and objectives for improvement. This strategy should prioritise which Essential Eight strategies to focus on first, taking into account your risk profile and resources.
- Implement Controls and Processes: Develop and implement the necessary controls and processes to address the identified gaps. And achieve a higher maturity level in the Essential Eight. This may involve acquiring new security tools, updating existing policies and procedures, and providing training for employees.
- Monitor and Continuously Improve: Cyber security is an ongoing process. It’s crucial to continuously monitor your cyber security posture. Also identify new threats and vulnerabilities, and update your controls and processes accordingly. Regularly review your cyber security strategy and conduct periodic assessments to measure your progress and identify areas for further improvement.
Conclusion
Ultimately, achieving a high level of cyber security maturity is an ongoing process that requires continuous effort and commitment. However, the benefits of a robust cyber security posture are undeniable. For example, it reduces risk of cyber attacks, improves compliance with regulations, and enhances business continuity. By leveraging the Essential Eight Maturity Model and partnering with a qualified cyber security services provider, Australian businesses can confidently navigate the ever-evolving cyber threat landscape and build a more secure future.



