Imagine this: a small accounting company on the Gold Coast, diligently serving its local clients, suddenly finds its computer systems locked down by ransomware. Consequently, access to crucial financial data is denied, and a hefty ransom demand appears on the screen. This nightmare scenario, unfortunately, is becoming increasingly common for Australian small businesses. Because of this growing threat, understanding and implementing robust cybersecurity measures is no longer optional; indeed, it’s essential for survival.
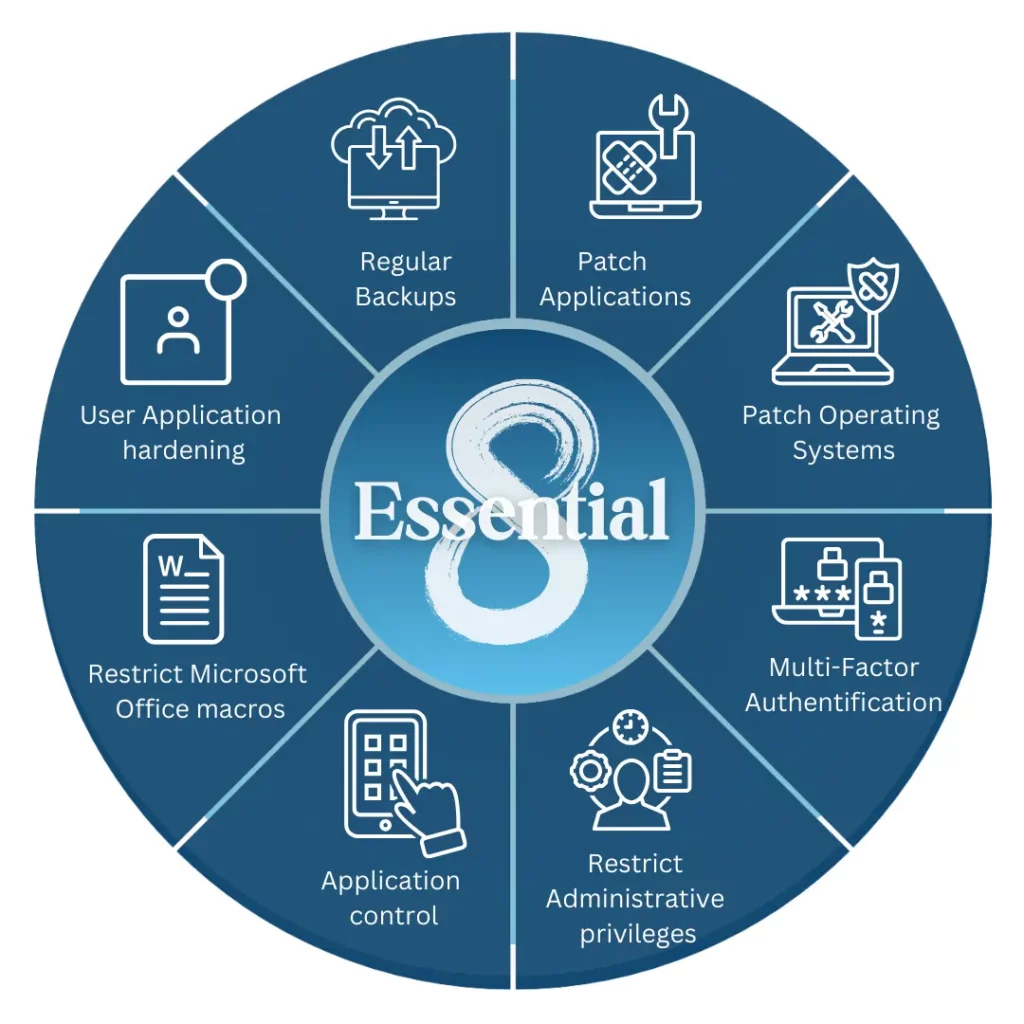
Therefore, the Australian Cyber Security Centre (ACSC) has developed the Essential Eight framework, – a set of practical strategies designed to help businesses defend against cyber threats. Among these, User Application Hardening stands out as a critical yet often overlooked tactic. In fact, it’s one of the most effective ways to protect systems from being compromised by malicious content delivered through everyday applications.
As we previously explored in our article, ‘Defend Your Business With The Essential Eight’, having multiple layers of security is no longer optional — it’s essential. Consequently, application hardening adds a strong layer to that defense by directly reducing the ways attackers can infiltrate systems through software. In other words, application hardening involves tightening the security of the software your team already uses. Specifically, it means disabling features that cybercriminals often exploit — such as browser plugins, macros, or scripts — thereby reducing the “attack surface” of your systems.
In the remainder of this article, we will delve deeper into what application hardening entails, explore practical steps Australian businesses can take to implement it effectively, and provide real-world examples.
Fortifying Your Defenses: The Application Hardening Process
What is Application Hardening?
To put it simply, application hardening is the process of making your software applications more secure and resilient against cyberattacks. For instance, think of it this way:
- Your Business Applications as Entry Points. Imagine your business applications – such as your web browser, email client, and accounting software – as doors and windows to your digital assets.
- Reinforcing Against Intruders. Application hardening is like reinforcing those entry points with stronger locks, security screens, and fewer openings. As a result it makes it significantly harder for cyber intruders to gain access or cause damage.
The Critical "Why": Benefits for Australian Small Businesses
Implementing application hardening is a fundamental security practice that offers several critical benefits for Australian small businesses:
- Reduced Risk of Malware Infections. Firstly, by strengthening your applications, you significantly decrease the likelihood of falling victim to:
- Ransomware
- Viruses
- Spyware
- Prevention of Unauthorised Access. Secondly, hardened applications are less vulnerable to breaches, thereby protecting:
- Sensitive customer data
- Financial records
- Intellectual property
- Mitigation of Exploitable Vulnerabilities. Thirdly,his process actively addresses weaknesses within the software itself, which are often targeted by cybercriminals.
- Improved System Stability and Performance. Moreover, by disabling unnecessary features, you can:
- Reduce the application’s attack surface.
- Minimise potential points of failure.
- Potentially improve application performance.
- Contribution to Regulatory Compliance. Finally, depending on your industry and the data, application hardening can help meet requirements under Australian data protection regulations.
Fortifying Your Defenses: The User Application Hardening Process
Now that you understand the why, let’s explore the how — the essential steps your business can follow to successfully harden applications and reduce risk. Although it may seem technical at first, each step is actionable and well within reach for Australian small businesses. In fact, even small changes can lead to major security improvements.
1. Identify and Inventory Applications
First and foremost, you need to know exactly what software is installed on your systems. Without visibility, you can’t secure what you don’t know exists. Therefore, create a list of all applications used across the business — from web browsers and email clients to PDF readers and accounting tools.
Moreover, be sure to include software installed on all workstations, laptops, and even mobile devices used for work. This helps you spot potentially risky or unauthorised programs that may have slipped under the radar.
2. Remove Unnecessary Applications
Next, look closely at the list and remove any applications that are unused, outdated, or no longer needed. Every unnecessary app is another potential entry point for attackers.
For example, legacy software that’s no longer updated is a common weak spot. Furthermore, even well-known tools can pose risks if they’re not patched — removing them altogether eliminates the threat completely.
3. Disable Unnecessary Features and Components
Afterwards, focus on disabling features within applications that your team doesn’t need. These features, while convenient, are often exploited by cybercriminals to run malicious code.
For instance, disable:
- Macros in Microsoft Office (unless absolutely necessary and properly managed).
- Browser extensions that aren’t essential to work.
- Flash, Java, or ActiveX — older technologies known for security issues.
Because attackers often exploit these features, turning them off significantly reduces your attack surface.
4. Configure Security Settings
Then, take time to review and configure the built-in security settings within each application. Often, the default settings prioritise convenience over security, which isn’t ideal for a business environment.
Therefore, you should:
- Enable automatic updates to ensure vulnerabilities are patched quickly.
- Restrict users from changing security configurations unless they’re authorised.
- Use built-in password controls (where applicable) to enforce complexity and expiry policies.
Additionally, this step can often be automated using tools built into your operating system or via your IT provider.
5. Implement Application Control
Finally, consider pairing application hardening with application control — a strategy that ensures only approved applications can run on your systems.
As we explained in ‘The Power of Application Control: Securing Your Systems’, this measure further reduces risk by blocking unknown or untrusted software entirely. Whereas hardening focuses on securing what you allow, application control decides what you allow in the first place.
Keep in mind, the level of application hardening your business needs may vary depending on where you sit in the Essential 8 Maturity Model. While some small businesses may only need basic hardening, others with higher risk profiles should aim for more advanced controls.
Real-World Reinforcement: User Application Hardening Examples & Specific Configurations
Although the concept of application hardening may sound abstract, applying it to everyday business software can make a major difference. Therefore, let’s walk through practical, real-world examples that show exactly how user application hardening works for Australian small businesses. These examples not only reflect current best practices from the ACSC and Essential Eight framework but also offer configurations you can implement today.
1.Web Browser Hardening
Since web browsers are frequently used for accessing online resources and handling sensitive information, securing them is paramount. 1 For example, you can implement the following measures:
- Disable unnecessary browser extensions. Firstly, many browser extensions can introduce security vulnerabilities or track user activity. Therefore, review installed extensions and remove any that are not strictly required.
- Configure stricter privacy and security settings. Secondly, most modern browsers offer enhanced privacy and security options. For instance, you can adjust settings to block third-party cookies, enable “Do Not Track” requests, and enhance phishing and malware protection.
- Enable automatic updates. Thirdly, outdated browsers are a prime target for attackers. Consequently, ensure that automatic updates are enabled to receive the latest security patches promptly.
- Use a secure search engine by default. Lastly, some search engines prioritise privacy and security. Therefore, consider setting a privacy-focused search engine as the default.
Specific Configurations
- Disable Java and Flash (or ensure you are using versions that do not support Java). Firstly, these older technologies are often riddled with security vulnerabilities. Because of this, it’s best to disable them entirely if they are not essential for your business operations.
- Implement web filtering to block traffic to advertising servers and known malicious sites. Secondly, web filtering tools can prevent users from accessing potentially harmful websites. Furthermore, blocking advertising servers can reduce exposure to malvertising (malicious advertisements).
- Control internet zone settings centrally and prevent user changes. Thirdly, Group Policy (in Windows environments) can be used to manage internet zone security settings consistently across your organisation, preventing users from weakening these controls.
- Consider using Attack Surface Reduction (ASR) rules (if applicable to your operating system). Finally, ASR rules can block certain behaviors that are commonly used by malware. For example blocking executable content from email or webmail clients.

2. Email Client Hardening
Email remains a primary vector for cyberattacks like phishing and malware distribution. Thus, hardening your email clients is crucial:
- Disable automatic downloading of attachments.Firstly, malicious attachments are a common way to spread malware. Therefore, train users to manually download attachments only when they are expected and from trusted senders.
- Treat all external emails with caution. Secondlty, encourage a culture of skepticism towards emails from unknown senders or those containing suspicious links or requests.
- Use strong email security features (e.g., anti-phishing). Thirdly, ensure that your email client or email security solution has robust anti-phishing and spam filtering capabilities enabled.
Moreover, train staff to verify email senders, avoid clicking suspicious links, and report anything unusual immediately.
3. Office Suite Hardening (e.g., Microsoft Office)
Office applications are widely used but can also be exploited through malicious documents:
- Disable macros by default (unless absolutely necessary and properly managed). Macros can contain malicious code. Consequently, disable them by default and only enable them for trusted documents when absolutely required, with appropriate security controls in place.
- Be cautious with external documents. Moreover, exercise caution when opening documents from external sources, even if they appear to be from legitimate contacts.
- Enable Protected View for downloaded files. Additionally, this feature opens documents in a sandboxed environment, limiting the potential damage if the file contains malware.
Specific Configurations
- Block Office from creating child processes and executable content. Firstly, this ASR rule can prevent Office applications from launching other potentially malicious programs.
- Disable the activation of OLE packages. Secondly, object Linking and Embedding (OLE) can be abused to embed malicious content within documents. Disabling its automatic activation can reduce this risk.
- Implement ASR rules to block Office from injecting code into other processes. Finally, this can prevent attackers from using Office applications to compromise other running software.
4. PDF Reader Hardening
PDF readers are another common target for attackers:
- Disable JavaScript execution by default. Firstly, malicious PDFs often use JavaScript to execute harmful code. So disabling it by default significantly reduces this risk.
- Keep the software updated. Also ensure your PDF reader is always up to date with the latest security patches.
5. PowerShell Hardening
PowerShell is a powerful scripting language that can be misused by attackers:
- Disable or remove PowerShell 2.0. Firstly, older versions of PowerShell have known security vulnerabilities. Therefore, ensure you are using a more recent version or disable older versions if they are not required.
- Configure PowerShell to use Constrained Language Mode. Secondly, this mode limits the capabilities of PowerShell, making it more difficult for attackers to use it for malicious purposes.
- Log blocked PowerShell script executions and monitor for signs of compromise. Thirdly, monitoring PowerShell activity can help detect and respond to potential attacks.
Additionally, consider integrating PowerShell hardening into your broader endpoint security policy to align with Essential Eight maturity guidelines.
The Human Element: User Awareness and Training
Although technical controls are powerful, they’re not foolproof. That’s why user awareness is just as important. Even the most hardened application can be bypassed by a careless click or poor decision.
Therefore, provide ongoing cyber security training to help your team:
- Recognise phishing attempts.
- Handle downloads and attachments safely.
- Avoid unauthorised app installations.
Ultimately, hardening is most effective when paired with informed, security-conscious behaviour from every user in your business.
Implementing User Application Hardening: Practical Steps for Your Business
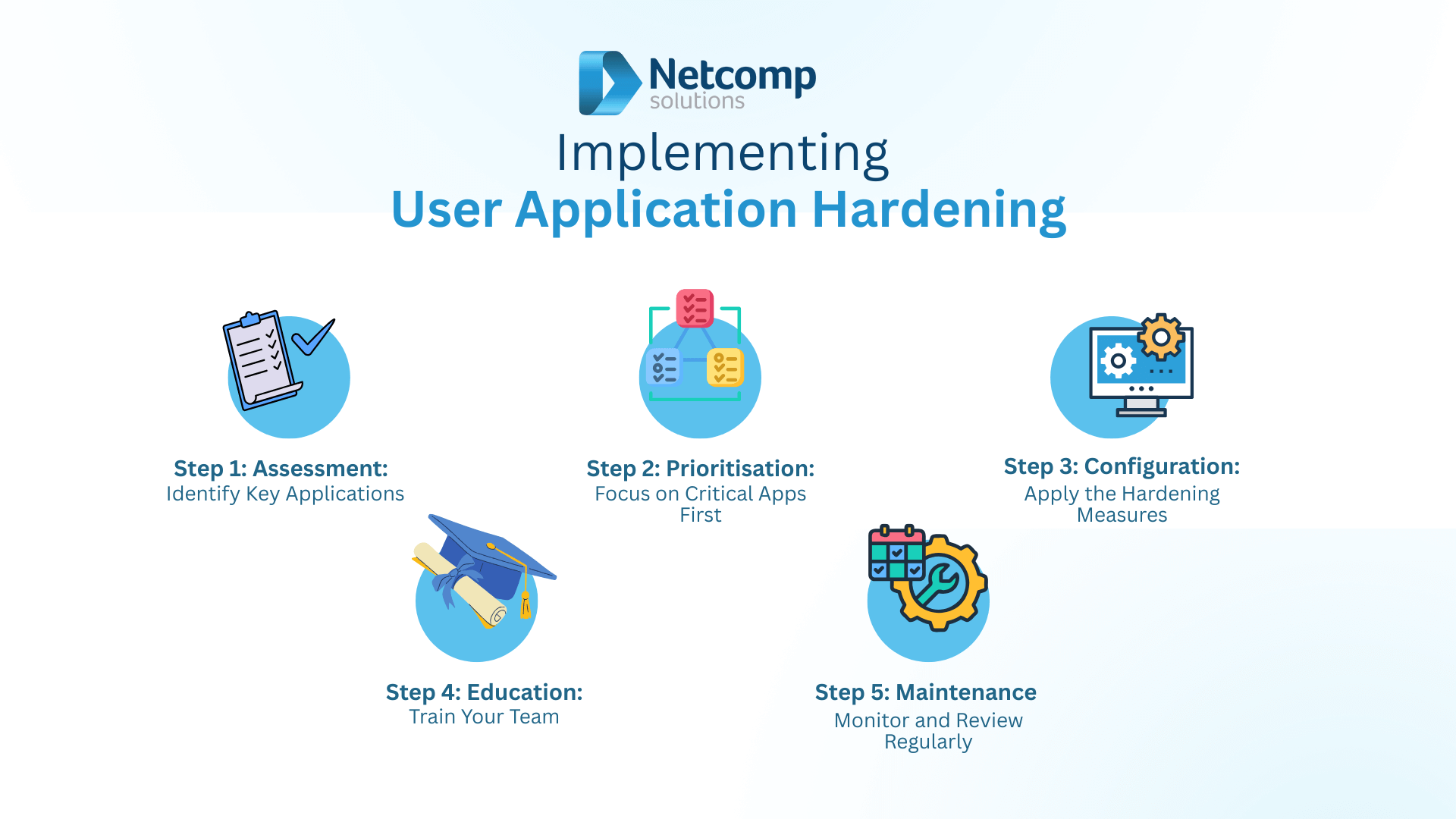
Now that you understand the importance of user application hardening, the next step is putting it into action. Fortunately, even small Australian businesses with limited IT resources can begin this process methodically. Therefore, let’s break down a practical five-step approach that will help you secure your business systems efficiently and effectively.
Step 1: Assessment — Identify Key Applications
Firstly, take stock of all applications used in your business. Although this might sound basic, many organisations don’t have a complete inventory of what software is running on their systems. For example, check your operating systems, productivity tools, browsers, email clients, PDF readers, and any third-party tools your business relies on.
Moreover, make sure to include both installed desktop software and browser-based or cloud-hosted applications in this review.
Step 2: Prioritisation — Focus on Critical Apps First
Once you’ve compiled your list, you’ll need to prioritise. Specifically, start by hardening applications that:
- Are used most frequently.
- Handle sensitive data (e.g., payroll, CRM, accounting).
- Are internet-facing or regularly interact with external content.
Additionally, you may want to review recent cyber threat intelligence from the ACSC to identify high-risk applications that are being actively targeted.
Step 3: Configuration — Apply the Hardening Measures
Now comes the core of the work: adjusting your application settings. As outlined in the previous section, this includes actions like:
- Disabling unnecessary features.
- Blocking unsafe scripts and macros.
- Enforcing secure configurations.
- Applying group policies or registry tweaks if needed.
Because many of these settings are already documented by vendors and the Australian Signals Directorate (ASD), you don’t have to start from scratch. Instead, follow their security baselines and customise them to your environment.
Step 4: Education — Train Your Team
While technical measures are critical, user awareness is equally important. Therefore, run regular training sessions to help your team:
- Recognise suspicious behaviour in applications.
- Use secure browsing and email habits.
- Avoid installing unauthorised software.
Furthermore, even a simple poster or monthly security tip can help build a culture of cybersecurity awareness.
Step 5: Maintenance — Monitor and Review Regularly
Finally, security isn’t a set-and-forget task. Because applications are updated, new features appear, and threats evolve, your hardening configurations need regular reviews.
So, schedule periodic audits—perhaps quarterly—to:
- Reassess application usage.
- Reconfirm configuration settings.
- Uninstall unused or outdated applications.
Additionally, you should keep logs of changes and updates to maintain a consistent security posture over time.
Monitoring and Maintaining Your Hardened Environment
Implementing application hardening is a significant step forward in securing your Australian small business. However, it’s not a set-and-forget solution. Indeed, to ensure the ongoing effectiveness of your efforts, continuous monitoring and proactive maintenance are absolutely essential.
Continuous Monitoring: Stay Alert, Stay Protected
To begin with, it’s crucial to continuously monitor your systems and applications to ensure that your hardening measures remain effective. For example, this involves keeping an eye on application behavior, looking for any anomalies or suspicious activity that might indicate a breach or a weakening of your security controls. Furthermore, regular testing of your security posture can help identify any gaps or misconfigurations in your application hardening.
Logging and Auditing: Your Silent Watchdogs
Moreover, robust logging and auditing of security-related events are vital for both monitoring and incident response. Consequently, ensure that your systems are configured to log relevant activities, such as application usage, security setting changes, and any blocked attempts. Subsequently, regularly review these logs for any unusual patterns or potential security incidents.
Incident Response: Being Prepared for the Unexpected
Even with hardened applications, incidents can still occur. That’s why you need an incident response plan. If a breach happens, how quickly and effectively you react can significantly reduce the damage.
So, document clear steps: who to notify, how to isolate the issue, and what tools or resources you’ll need. Furthermore, rehearse your plan with your team through simulated exercises or tabletop scenarios.
Regular Review and Updates: Security is Not Static
Finally, regular review is crucial. Because vendors often release updates to fix newly discovered vulnerabilities, failing to apply them can reopen doors you’ve already locked.
Thus, schedule time—ideally every quarter—to:
- Reassess which applications are still in use.
- Confirm that security configurations remain intact.
- Apply necessary patches and upgrades.
- Review ASD and ACSC advisories for new threats or recommendations.
Additionally, review your own logs and incident reports to identify trends or weak spots that need attention.
Conclusion
In conclusion, user application hardening stands as a cornerstone of a robust cybersecurity posture for Australian small businesses. By proactively securing the software your employees use every day, you significantly reduce your attack surface and make it considerably more challenging for cybercriminals to compromise your systems and data. Indeed, this proactive approach can save you from the potentially devastating consequences of a cyberattack.
Moreover, application hardening is a vital pillar of the Essential Eight framework from the Australian Cyber Security Centre (ACSC). While it works best alongside other strategies like multi-factor authentication, regular patching, and application control, it delivers significant protection on its own by reducing the attack surface available to threat actors.
Therefore, now is the perfect time to take action. Start by reviewing the applications your business uses daily. Next, assess their security settings, disable unnecessary features, and ensure they are properly configured and maintained. Although the process may seem daunting, each step significantly boosts your overall cyber resilience.
If you’re unsure where to start, or if you need professional guidance tailored to your specific needs, contact Netcomp. Our Brisbane-based team specialises in IT and cybersecurity solutions for small businesses across Queensland. Whether you need help assessing your current environment or want expert advice on building a long-term security plan, we’re here to help.
Because when it comes to cybersecurity, doing nothing is the greatest risk—and doing something today could save your business tomorrow.



