In recent years, Australian businesses have faced a significant rise in cyberattacks, with ransomware incidents and data breaches becoming alarmingly common. According to the Australian Cyber Security Centre (ACSC), small businesses are particularly vulnerable with the average cost of cybercrime incidents rising to $49,600. Consequently, protecting digital systems has never been more critical. Moreover, one of the most effective ways to safeguard systems is through application control. This security measure prevents unauthorised applications from executing on a system, significantly reducing the risk of malicious software infiltrating the network. As a result, application control plays a vital role in strengthening an organisation’s overall cybersecurity posture.
Furthermore, the cyber threat landscape in Australia continues to evolve, making it essential for businesses to adopt proactive security measures. Notably, application control aligns with the Australian Signals Directorate’s (ASD) Essential Eight – a set of cybersecurity strategies designed to help organisations mitigate cyber risks. These strategies are widely regarded as best practices for improving cybersecurity resilience across Australian businesses. If you’d like to learn more about the Essential Eight framework, please read our comprehensive article: ‘Defend Your Business With The Essential Eight’. Throughout this article, we will explore the power of application control, its critical role within the Essential Eight, and practical steps to successfully implement it in your business.

What is Application Control?
Application control is a security practice that manages which applications are permitted to run on a system. Specifically, it ensures that only pre-approved software can execute, while automatically blocking any unauthorised or potentially harmful applications. As a result, businesses can significantly reduce their exposure to cyber risks.
The core function of app control is to create a list of approved applications, often referred to as a whitelist or allowlist. Because of this, any software not on the list is automatically denied access, preventing malicious programs from infiltrating the system. Furthermore, this proactive approach strengthens the organisation’s overall security posture.
There are several benefits to implementing.
- First of all, it helps to reduce the risk of malware infections, as unauthorised applications are not allowed to run.
- In addition, it prevents employees from installing unapproved software, which could introduce vulnerabilities.
- Moreover, it improves system stability and performance by limiting resource usage to essential applications.
- Lastly, it enhances compliance with security regulations, making it easier for businesses to meet industry standards.
For example, without application control, an employee might accidentally download and install a seemingly harmless program that contains malware. However, with app control in place, the software would be automatically blocked, eliminating the risk. Additionally, businesses can use it to restrict access to entertainment applications or other non-business-related software, helping to maintain productivity.
Essential Eight Application Control
The Australian Cyber Security Centre (ACSC) has developed the Essential Eight mitigation strategies to help organisations protect themselves against cyber threats. These strategies provide a prioritised list of security controls that significantly enhance an organisation’s cyber resilience.
Among the Essential Eight, application control is a foundational strategy. It designed to prevent the execution of unapproved or malicious applications. Thereby reducing the risk of malware infections and unauthorised software installations. Consequently, app control plays a vital role in protecting sensitive data and maintaining system integrity.
The Essential Eight framework outlines maturity levels for application control, ranging from Level One to Level Three.
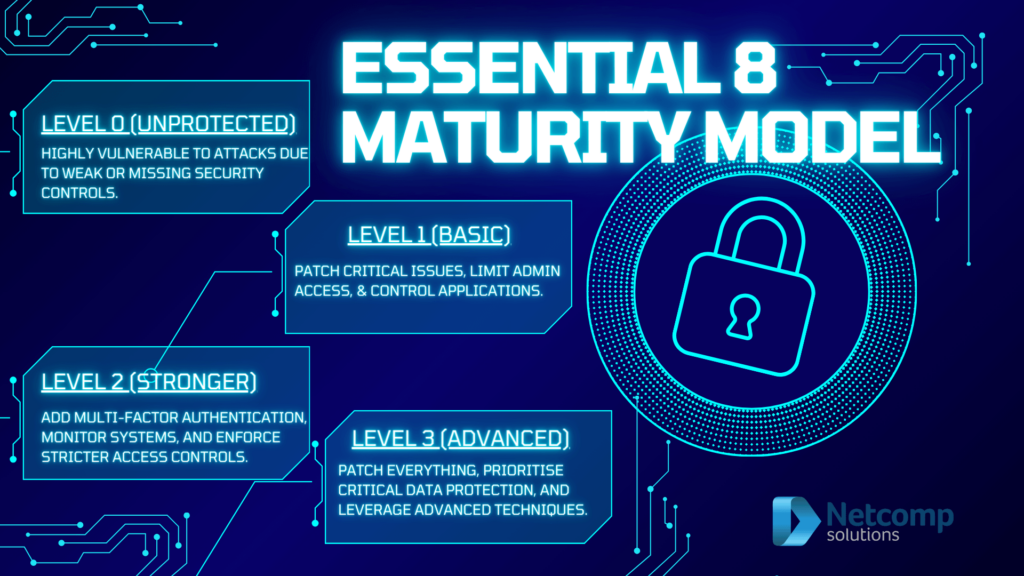
At Maturity Level One, organisations implement basic application whitelisting on a limited number of systems.
At Maturity Level Two, the scope of application control expands to include more critical systems and applications.
Finally, at Maturity Level Three, comprehensive application control is enforced across the entire organisation, with continuous monitoring and updates.
Australian businesses must also comply with various cyber security regulations that emphasise application control. For example, the Information Security Manual (ISM) issued by the Australian Signals Directorate (ASD) highlights the importance of application control as part of a robust security strategy. Additionally, the Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme require organisations to implement security measures that protect personal information from unauthorised access.
Application Control vs. Application Whitelisting
Application whitelisting is a specific form of application control that allows only explicitly approved applications to run on a system. While application whitelisting is a critical aspect of application control, the two terms are not interchangeable. Rather, application control encompasses a broader range of security measures, including whitelisting, blacklisting, and greylisting.
Both application control and whitelisting share the common goal of preventing unauthorised applications from executing. However, application control offers more comprehensive functionality by including additional techniques like blacklisting, which blocks known malicious applications. And greylisting, which temporarily restricts unknown applications until they are verified as safe.
Modern application control solutions go beyond simple whitelisting by incorporating dynamic policies and contextual awareness. For instance, certain applications might be permitted only during specific time frames or for particular user groups, enhancing security without disrupting productivity.
In some scenarios, whitelisting is preferred when security is the top priority, such as in highly sensitive environments like financial institutions.
Conversely, blacklisting may be more suitable in environments where flexibility and usability are essential, such as in small businesses with diverse software needs. Greylisting provides a balanced approach, offering temporary restrictions until applications are properly assessed.
How Do I Implement Application Control? (Practical Implementation)
Firstly, here’s a simple breakdown of how to put application control into action:
- Choose your method:
- For Windows: Use built-in tools like Windows Defender Application Control (WDAC) or AppLocker. You can control these settings through Group Policy.
- For Macs: macOS has Gatekeeper and XProtect.
- For Linux: Use AppArmor or SELinux.
- Or: Use a third-party app control program
- Plan your rules:
Basically, decide which apps your team needs. Then, make a list of those apps.
Next, create rules that say, “Only these apps can run.”
- Test before you go live:
Initially, try your rules on a few computers first. This way, you can find any problems early.
- Tell your team:
Clearly, explain why you’re using application control. Also, show them how to ask for access to new apps. Then, train them on the new process.
- Use Group Policy (for Windows):
In short, use Group Policy to set up your AppLocker rules.For example, you can allow apps based on where they’re saved, who made them, or their file details.
- Consider third-party tools:
Also, if you need more advanced control, look into programs from companies like CrowdStrike, Trend Micro, Sophos or Carbon Black.
Application Control Audit (Ensuring Effectiveness)
Importance of Auditing:
- Firstly, regular audits are essential for maintaining the effectiveness of application control.
- Indeed, without consistent monitoring, security policies can become outdated or ineffective against evolving threats.
- Moreover, audits provide a crucial opportunity to identify gaps, refine policies, and ensure compliance with relevant regulations like the Australian Privacy Principles or industry-specific standards.
- Additionally, audits help to demonstrate due diligence and accountability, which are vital for building trust with customers and stakeholders.
Audit Process:
Next, the audit process itself should follow a structured approach.
Specifically:
- Review existing application control policies.
- Conduct a thorough analysis of application logs and event data.
- Perform vulnerability scans and penetration testing.
- Subsequently, interview key personnel.
- Finally, compare the current state with industry best practices.
Log Analysis:
Furthermore, log analysis is a critical component of the audit process. For instance, by examining application control logs, you can identify patterns of unauthorised application usage, failed execution attempts, and attempts to bypass security controls. In particular, pay close attention to logs that indicate the execution of unknown or untrusted applications. Also, look for anomalies in user behaviour, such as unusual spikes in application usage or attempts to access restricted resources. Additionally, utilise log aggregation and analysis tools to automate the process and identify potential security issues more efficiently.
Reporting:
Moreover, generating comprehensive reports is essential for demonstrating compliance and tracking performance. Consequently, these reports should include information on the scope of the audit, the findings, and the recommendations for improvement. Specifically, include metrics such as the number of blocked applications, the frequency of policy violations, and the time taken to respond to security incidents. Then, present these reports to management and relevant stakeholders to communicate the effectiveness of the application control system and highlight any areas that require attention. Likewise, these reports can be used to demonstrate compliance with regulatory requirements during audits.
Continuous Improvement:
Finally, continuous improvement is crucial for maintaining the long-term effectiveness of application control. Therefore, establish a process for ongoing monitoring and regular reviews of application control policies. In addition, stay informed about emerging threats and vulnerabilities, and update your policies accordingly. Afterwards, encourage feedback from users and your business IT support to identify areas for improvement. Ultimately, by adopting a proactive and iterative approach, Australian businesses can ensure that their application control systems remain effective in protecting their critical assets.
Application Control Software (Tools and Solutions)

When it comes to application control, businesses have many solutions to choose from. These range from built-in operating system features to dedicated third-party software:
- Built-in solutions: For example, Microsoft AppLocker, integrated into Windows, provides a basic foundation for application control through Group Policy.
- Third-party solutions: Vendors like Carbon Black, Trend Micro, CrowdStrike, and Sophos offer more advanced capabilities, including:
- Centralised managementDetailed reporting
- Integration with other security tools
Therefore, these features make third-party solutions ideal for larger or more complex environments.
Key Features and Capabilities
Key features and capabilities vary significantly between different application control solutions. Specifically, some of the most important features include:
- Granular policy management: Allows businesses to control exactly which applications are allowed to run based on criteria like:
- File hash
- Publisher certificate
- File path
- Real-time monitoring and threat intelligence: Enable proactive detection and blocking of malicious applications.
- Behavioral analysis: Moreover, this identifies and blocks suspicious application activity, even if the application isn’t explicitly blocked by policy.
- Reporting and analytics: Dashboards provide valuable insights into application usage and potential security risks.
- Integration with SIEM systems: This further correlates application control events with other security data.
Choosing the Right Application Control Software
Choosing the right solution requires careful consideration of a business’s specific needs and requirements:
- Assess your IT infrastructure. Firstly, start by evaluating the size and complexity of your infrastructure.
- Define your security objectives and compliance requirements. Secondly, determine what you need to protect and any legal or regulatory standards you must meet.
- Evaluate features and capabilities. Thirdly, ensure the solution aligns with your security goals and needs.
- Consider deployment and management. Tfinally, think about the ease of deploying and managing the software, as well as the level of support the vendor provides.
Important Considerations
Several important factors should be factored into your decision:
- Cost. Evaluate the total cost of ownership, including:
- Licensing fees
- Implementation costs
- Ongoing maintenance
- Scalability. Furthermore, ensure the solution can handle future growth and an increasing number of users and devices.
- Ease of use. Moreover, look for solutions that simplify management and reduce the burden on IT staff.
- Integration. Finally, ensure compatibility with existing security infrastructure, such as:
- Antivirus
- Endpoint Detection and Response (EDR)
- SIEM systems
Local Cybersecurity Providers for Australian Businesses
Australian businesses may also want to consider local cyber security providers.
Benefits of local cyber security specialists:
- Localised support
- Better understanding of the Australian threat landscape
- Tailored solutions to meet Australian regulatory and compliance standards.
Application Control Examples (Practical Use Cases)
Below are practical use cases illustrating how application control helps protect businesses in different sectors.
- Firstly, application control helps to protect systems. For instance, in the healthcare sector, where patient data is paramount, application control can restrict access to sensitive systems, allowing only approved medical software to run. Similarly, in the finance industry, where regulatory compliance is crucial, application control can prevent the execution of unauthorised financial tools, mitigating the risk of data breaches and non-compliance. Furthermore, within government agencies, application control ensures that only vetted applications operate on critical infrastructure, protecting essential services from potential cyberattacks.
- Secondly, application control plays a vital role in preventing ransomware. In particular, ransomware often relies on exploiting vulnerabilities in unpatched or unauthorised applications. Therefore, by implementing application control, businesses can create a whitelist of trusted applications, effectively blocking the execution of malicious software, including ransomware payloads. Additionally, this proactive approach significantly reduces the attack surface, making it much harder for cybercriminals to infiltrate systems.
- Thirdly, blocking unauthorised applications is another key benefit. Indeed, employees sometimes install software without IT approval, which can introduce security risks and compliance issues. Consequently, application control allows businesses to define a clear policy on approved software, preventing the installation and execution of unauthorised applications. Specifically, this helps to maintain a consistent and secure software environment across the organisation, reducing the risk of malware infections and data leaks.
- Finally, protecting critical systems and infrastructure is paramount. Above all, critical systems, such as those controlling industrial processes or essential services, require the highest level of security.
Advanced Application Control Techniques: A Deeper Dive
Implementing advanced application control techniques can further strengthen cyber security measures. So below are key advanced techniques that enhance application control effectiveness.
Cryptographic Hash Rules
Firstly, cryptographic hash rules allow businesses to create unique digital fingerprints for applications. Consequently, only applications with verified hash values are allowed to execute. This method ensures that even if the file name or path changes, the application will not run without the correct hash.
Publisher Certificate Rules
Secondly, publisher certificate rules verify the digital signatures of software publishers. Therefore, only applications signed by trusted publishers are permitted to run. This technique helps businesses block malware disguised as legitimate software while ensuring that trusted applications can operate without disruption.
Path Rules
Thirdly, path rules allow businesses to control applications based on their file path locations. Although this method is simple to implement, it is often combined with other techniques to improve security. Moreover, businesses can use path rules to block software from unauthorised directories and prevent the execution of potentially harmful applications.
Preventing Bypass Techniques
Malicious actors often attempt to bypass application control systems using various methods. However, businesses can mitigate this risk by using Microsoft’s recommended application blocklist, which identifies and blocks vulnerable applications commonly exploited by attackers. Additionally, implementing a vulnerable driver blocklist prevents attackers from loading malicious drivers onto systems, further enhancing security.
Implementing Application Control in Different Environments
Application control can be tailored to different operating environments, providing comprehensive protection across various platforms. Consequently, businesses must follow platform-specific guidance to maximise effectiveness.
Windows Environments
In Windows environments, application control can be implemented using Windows Defender Application Control (WDAC) and AppLocker. Firstly, businesses should configure WDAC policies to define which applications are allowed to run based on publisher certificates, file hashes, or paths. Moreover, AppLocker can be used alongside Group Policy settings to enforce rules across endpoints. As a result, these tools provide a flexible approach to managing application execution in Windows systems.
Linux Environments
Linux environments can leverage tools like fapolicyd to implement application control. Specifically, fapolicyd is a userspace daemon that prevents unauthorised applications from executing based on file path rules, hashes, or trust levels. Additionally, businesses can create custom rules to restrict execution permissions, thereby enhancing security in Linux-based systems. Consequently, this method ensures that only trusted applications can operate.
Application Control and Cybersecurity Compliance
Application control not only improves security but also helps businesses comply with cyber security regulations and mandates. Therefore, adopting application control solutions enables organisations to meet various compliance requirements effectively.
Essential Eight Framework
The Australian Cyber Security Centre (ACSC) developed the Essential Eight framework to help businesses improve their cybersecurity resilience. Importantly, application control is one of the key mitigation strategies outlined in the framework. By preventing unauthorised applications from executing, businesses can reduce the risk of malware infections and comply with the Essential Eight guidelines.
Other Compliance Frameworks
In addition to the Essential Eight, application control supports compliance with other frameworks such as ISO 27001, GDPR, and PCI DSS. Furthermore, these frameworks emphasise the importance of controlling software execution to safeguard sensitive data. Consequently, implementing application control helps businesses align with global cybersecurity standards.
How Application Control Can Help Reduce Shadow IT
Shadow IT refers to the use of unauthorised applications or devices without the knowledge or approval of the IT department. Unfortunately, this practice introduces significant security risks, including data breaches and non-compliance. However, application control mitigates these risks by preventing unauthorised applications from running on business systems. Moreover, by enforcing strict policies, businesses can ensure that only approved applications are used. Consequently, this approach reduces the likelihood of data leaks and improves overall security.
Beyond Application Control for Risk Management
While application control provides robust protection, implementing allow and deny lists can be challenging. Consequently, businesses should consider integrating privilege management to enhance security. Privilege management solutions enable businesses to limit user access to specific applications based on job roles. Additionally, modern Privileged Access Management (PAM) solutions offer granular control over application execution, ensuring that only authorised users can access sensitive applications. Therefore, combining application control with privilege management creates a comprehensive security framework.
Conclusion
Application control plays a critical role in protecting Australian businesses against cyber threats. By preventing unauthorised applications from executing, businesses can reduce the risk of malware infections, ransomware attacks, and data breaches. Moreover, application control aligns with the Essential 8 framework and other cybersecurity regulations, helping businesses achieve compliance.
Taking a proactive approach to cyber security is essential for safeguarding sensitive data and maintaining business continuity. Therefore, Australian businesses should consider implementing application control as part of their overall cyber security strategy.
If you have any questions or need professional assistance, please contact Netcomp — a trusted cyber security provider covering Brisbane and Gold Coast regions.
For more information, visit the Australian Cyber Security Centre (ACSC) website and explore the latest cybersecurity guidelines.



