The Urgent Truth: How Quickly Can Hackers Crack Your Password?
For years, we were all told the same thing. You needed a password with uppercase letters, lowercase letters, a number, and a special character. As a result, many of us created short, complicated passwords like “P@ssword1!” thinking they were unbreakable fortresses. However, this is a dangerous myth that could leave your business exposed. In fact, the rules of password security have completely changed, and what was once a strong password is now shockingly easy to crack.
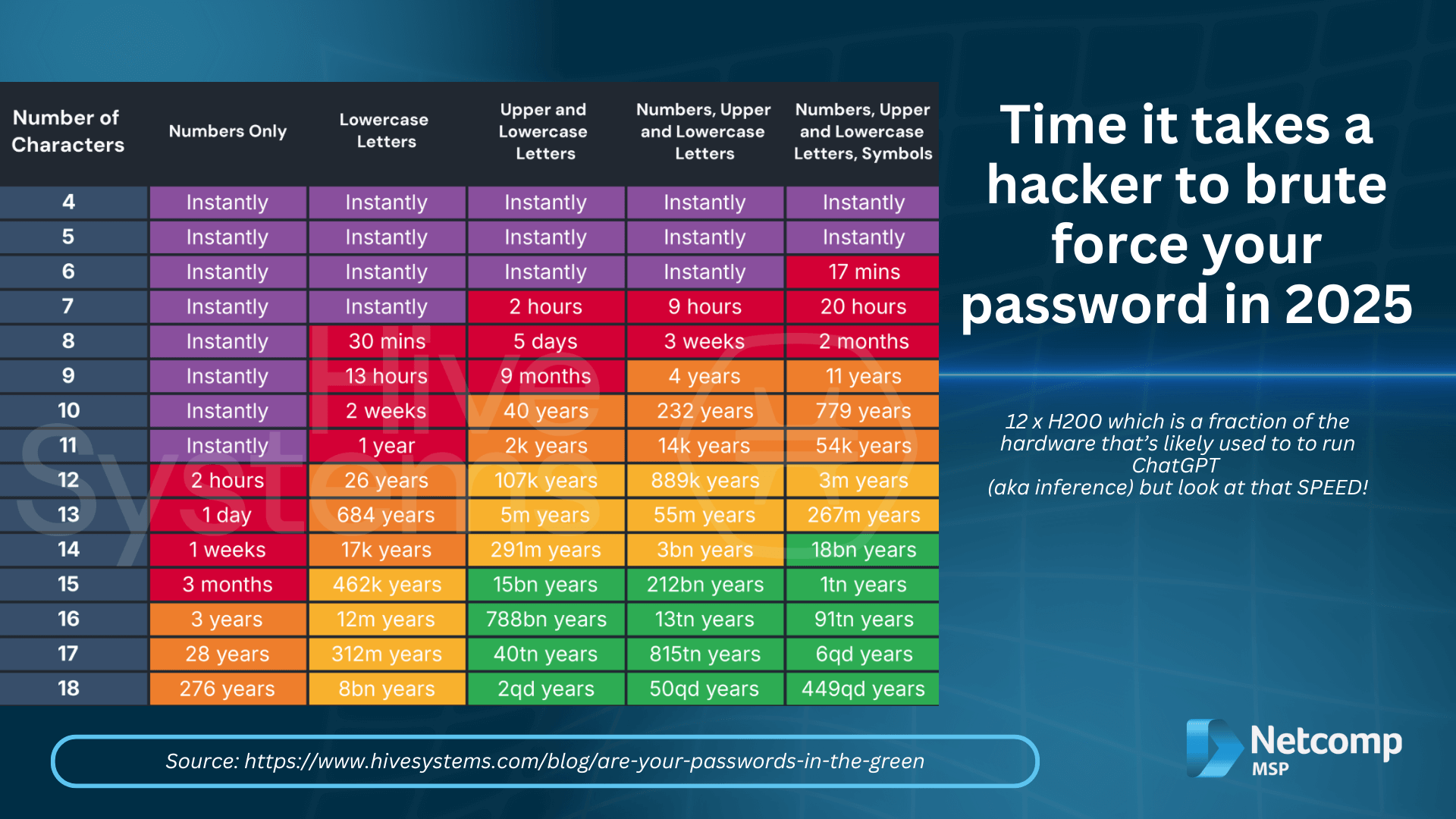
For example, consider the dramatic impact of AI. Back in 2020, an eight-character password with a mix of all character types could take weeks—or even months—for a hacker to crack. However, fast forward to 2025, and thanks to powerful new AI models and cloud computing, that very same password can now be cracked in just a few hours. In other words, the protection you once relied on has already expired.
In addition, this isn’t just a problem for big global companies. It’s a very real threat for Australian small businesses. Indeed, local experts at the Australian Cyber Security Centre (ACSC) regularly warn that cyberattacks are a significant risk, and a weak password is the most common entry point for a criminal. Essentially, your business’s digital security is only as strong as its weakest password. Therefore, it’s more important than ever to understand the new rules of password protection.
Why Passphrases Are the New Standard
Firstly, short and complicated passwords like T!m3@2020 no longer cut it in today’s cyber threat landscape.
Instead, the Australian Cyber Security Centre (ACSC) recommends using a passphrase—a string of four or more random, unrelated words.
Australian Cyber Security Centre (ACSC) recommends using something like “purple duck potato boat”.
So, why are passphrases so much better?
- Length beats complexity. Firstly, each extra word makes it exponentially harder to crack.
- Easy to remember. Secondly, a string of words is far simpler to recall than random characters.
- Less temptation to reuse. Thirdly, you’re less likely to recycle the same password across accounts.
Consequently, while a hacker might break a short password in hours or days, a strong passphrase could take centuries to crack with current computing power.
How to create a strong password: According to 2025 password-cracking data, anything under 12 characters—no matter how complex—can be broken in hours, days, or a few years at best. In contrast, a passphrase of 15+ characters with mixed letters, numbers, and symbols could take millions to trillions of years to crack. The safest approach for businesses is to aim for at least 16 characters, combine different character types, and avoid common phrases or predictable patterns.Moreover, according to 2025 password-cracking data, anything under 12 characters—no matter how complex—can be broken in hours, days, or a few years at best. In contrast, a passphrase of 15+ characters with mixed letters, numbers, and symbols could take millions to trillions of years to crack. The safest approach for businesses is to aim for at least 16 characters, combine different character types, and avoid common phrases or predictable patterns.
The Ultimate Password Hack: A Password Manager
However, even the strongest passphrase won’t protect you if you reuse it across multiple logins. This is where a password manager becomes your most valuable tool.
In fact, organisations like Google, Microsoft, CISA, and the ACSC all recommend them for one simple reason—they work.
Key benefits of a password manager:
- Generates strong passwords automatically. Firstly, each account gets a unique, ultra-strong password.
- Stores them securely. Secondly, you don’t have to memorise dozens of logins.
- Simplifies your life. Finally, you only need to remember one strong passphrase for the manager itself.
Meanwhile, by letting the manager do the heavy lifting, you dramatically reduce the risk of a data breach from stolen or reused passwords.
The Unbreakable Layer: Why Multi-Factor Authentication (MFA) is Non-Negotiable
MFA: Your Digital Deadbolt
Firstly, think of multi-factor authentication (MFA) as a digital deadbolt on your accounts.
Even if a hacker somehow gets your password, they still can’t get in without the second “key.”
Usually, that second factor is a one-time code sent to your phone, a prompt in an authenticator app, or even a physical security key.
Moreover, this extra step makes stealing your account dramatically harder because hackers would need both your password and your second factor.
Consequently, MFA is one of the simplest yet most powerful tools for protecting your business from costly breaches.
Why MFA Stops Hackers in Their Tracks
Because most cyberattacks rely on stolen passwords, adding MFA immediately shuts down the easiest path in.
Additionally, even in cases where large companies have been breached, accounts with MFA enabled have often stayed safe.
Therefore, MFA is no longer optional—it’s a must-have layer of protection for every Australian business.
Where to Turn It On First
However, knowing MFA is important isn’t enough—you need to enable it right away.
Start with your most critical accounts:
- Email accounts – Because they can be used to reset passwords for almost everything else.
- Banking and payment platforms – Since these hold direct access to your finances.
- Social media accounts – Because losing control here can damage your brand reputation.
Meanwhile, as you set up MFA on each account, choose an authenticator app over SMS where possible for stronger protection.

Your 10-Minute Security Checklist
Now that you understand the new rules, it’s time to take action. Indeed, securing your business doesn’t need to be complicated or time-consuming. Therefore, here is a simple checklist you can run through in under 10 minutes to dramatically improve your cybersecurity.
- Ditch the Old Habits: First, stop creating short, complex passwords and don’t try to remember them all.
- Go Long with a Passphrase: Instead, create one memorable, long passphrase that you can easily recall.
- Get a Password Manager: Then, sign up for a reputable password manager. For example, this tool will generate and store all your other unique passwords for you, so you never have to think about them again.
- Lock Down with MFA: After that, turn on multi-factor authentication on every single account that offers it. Consequently, you add an essential second layer of protection.
- Tell Your Team: Finally, share this simple, updated advice with your employees and make it a new standard for your entire business.
Ultimately, by following these simple steps, you are protecting your business, your data, and your peace of mind.
Best Practices for Creating and Managing Strong Passwords in 2025 – 2026
While passphrases and password managers are your foundation, a truly secure business needs a layered, modern approach. Therefore, here are the key practices that industry experts and cybersecurity agencies, including the ACSC, recommend for businesses today.
- Adopt a Reputable Password Manager. Firstly, you shouldn’t just use any password manager. Instead, choose a trusted, independently audited one (like 1Password or Bitwarden) that offers secure sharing and breach monitoring for your team. In this way, you can centralise credentials in an encrypted vault, making them easier to manage and control.
- Enforce Smart Password Policies. Secondly, gone are the days of forcing employees to change their passwords every 90 days. Instead, the new rule is to prioritise length over complexity. For this reason, you should require passwords of at least 14-16 characters and only mandate changes if a compromise is suspected.
- Centralise and Control Management. Thirdly, don’t let employees store work credentials in their browsers. Because they often lack the necessary security features. Instead, use enterprise password management tools with access controls and auditing features. Additionally, you should screen new passwords against breach databases to prevent employees from reusing compromised credentials.
- Elevate Security with Advanced Measures. Moreover, you can begin transitioning high-value systems to passwordless authentication using biometrics or FIDO2 keys. This further reduces the risk of password-related breaches. For your most critical accounts, like those with administrative access, consider Privileged Access Management (PAM) solutions. After all, these solutions offer an extra layer of protection by granting users just-in-time access only when it’s needed.
We hope these best practices are helpful and assist you in keeping your business safe. If you require professional assistance with any of your IT-related needs, please don’t hesitate to reach out to Netcomp Solutions.



