Did you know that the Australian critical infrastructure sector experienced 11% of all cyber incidents in 2023-2024, according to the Australian Signals Directorate (ASD) report? Moreover, the report also revealed that electricity, gas, water, and waste services accounted for 30% of reported critical infrastructure incidents. Additionally, education and training followed with 17%, and transport, postal, and warehousing came in third with 15%. Consequently, the Australian Cyber Security Hotline received over 36,700 calls, a 12% increase from the previous year. Therefore, protecting critical infrastructure is more important than ever.
In this article, we’re going to describe an interesting and vital topic – critical infrastructure sectors resilience in Australia. So let’s break down the cyber threats facing Australia’s essential services.
What is Critical Infrastructure?
Critical infrastructure refers to the collection of systems, facilities, and assets that are vital for the functioning of society and the economy. These infrastructures are considered essential because their disruption would impact public safety, security, health, or economic stability. However, these systems are increasingly vulnerable to cyberattacks. For example, cybercriminals and state-sponsored actors constantly developing new tactics to exploit these weaknesses.
What are the Critical Infrastructure Sectors in Australia?
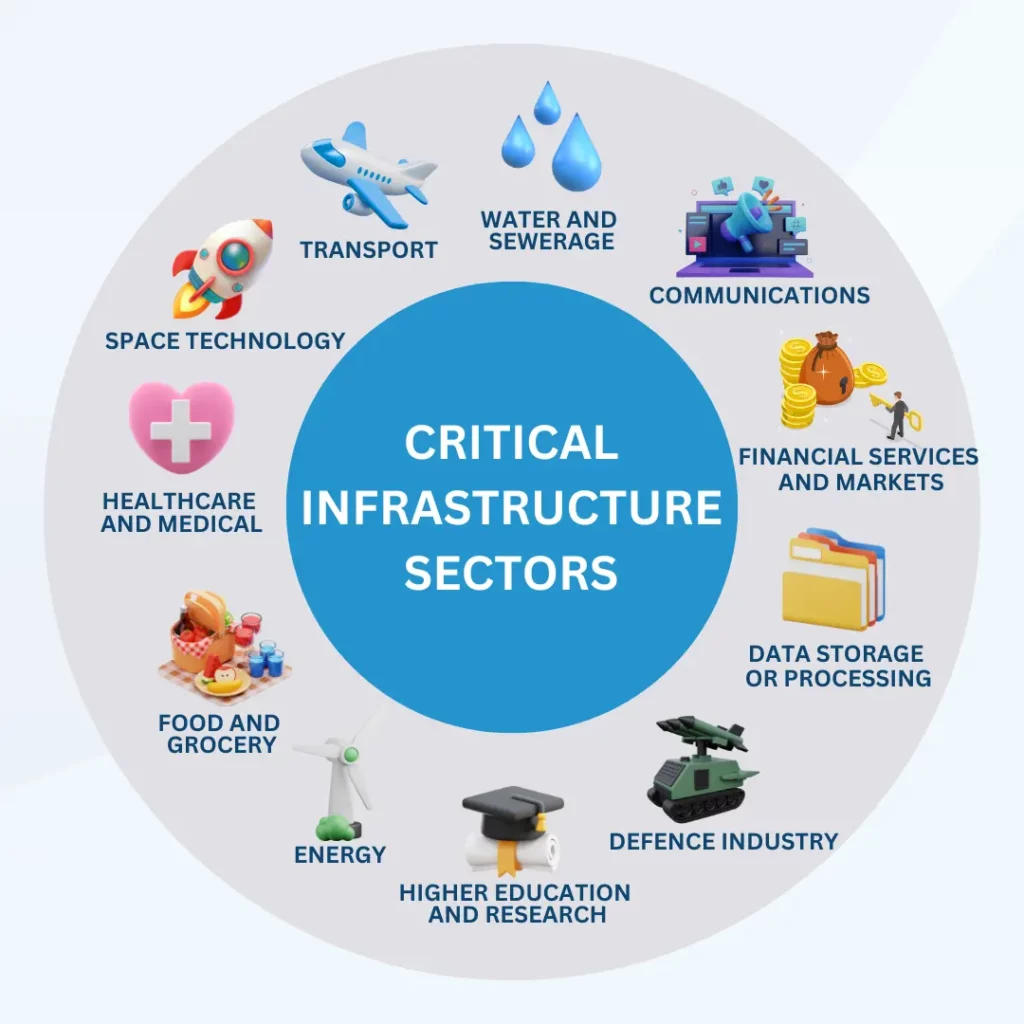
The 11 critical infrastructure sectors in Australia are:
Communications. This includes telecommunications networks, internet infrastructure, and satellite communications.
Financial services and markets. This includes banks, insurance companies, stock exchanges, and payment systems.
Data storage or processing. This includes data centers, cloud computing services, and other data storage facilities.
Defence industry. This includes military facilities, defense contractors, and related supply chains.
Higher education and research. This includes universities, research institutions, and academic networks.
Energy. This includes electricity generation, transmission, and distribution, as well as oil and gas production and transportation.
Food and grocery. This includes food production, processing, distribution, and retail.
Healthcare and medical. This includes hospitals, clinics, medical devices, and pharmaceutical manufacturing.
Space technology. This includes satellite technology, space launch facilities, and space research.
Transport. This includes roads, railways, airports, ports, and public transport systems.
Water and sewerage. This includes water treatment, distribution, and wastewater treatment.
What is critical infrastructure protection?
In Australia, critical infrastructure protection involves measures to safeguard essential services and systems crucial for the nation. These services are especially important for the country’s security, economy, and overall well-being.
For example, critical services include energy, water, transportation, communications, healthcare, and finance. Furthermore, the government and relevant agencies collaborate to strengthen the resilience of these essential systems.
At the same time, they work together to defend against potential threats, such as cyberattacks, natural disasters, and intentional disruptions. As a result, these efforts ensure the continuous delivery of vital services.
What is resilience in critical infrastructure?
Generally, resilience in Critical Infrastructure refers to the ability of systems to withstand, recover from, and adapt to disruptions. In other words, it is the capacity to bounce back from shocks and stresses, such as:
- Cyberattacks: Malicious digital attacks that can compromise systems and data.
- Natural Disasters: Events like floods, fires, earthquakes, and storms that can damage infrastructure.
- Human-made Disasters: Incidents like terrorism, accidents, and sabotage.
As a result, resilient critical infrastructure system can:

- Minimise Disruptions. By implementing robust security measures to prevent attacks and reduce the impact of incidents.
- Recover Quickly. Additionally, with effective contingency plans and recovery procedures in place to restore services as soon as possible.
- Adapt to Change. Moreover, by continuously assessing risks and updating security measures to stay ahead of emerging threats.
Understanding the Risks
In recent years, critical infrastructure has faced increasing risks from both cyberattacks and physical disruptions.
Cyberattacks
Generally hackers target essential infrastructure with advanced cyber threats, like:
- Malware: Disruptive software, such as viruses or spyware, that compromises systems.
- Ransomware: Malware that locks systems until a ransom is paid.
- Phishing: Scams that trick individuals into revealing sensitive information.
- Denial of Service (DOS): Attacks that overload systems to make them unavailable.
- Man-in-the-Middle: Interception and modification of communications.
- Brute Force: Unauthorised attempts to gain access by guessing passwords.
Eventually, these attacks disrupt critical services and cause severe economic and social problems. For example, the Colonial Pipeline Ransomware Attack, when in 2021, the Colonial Pipeline, a major fuel pipeline in the United States, was hit by a ransomware attack. As a result this led to fuel shortages on the East Coast, highlighting the vulnerability of critical infrastructure to cyber threats.
Physical Disruptions
Similarly, natural disasters, such as bushfires, floods, and cyclones, can damage infrastructure, leading to power outages and water shortages. Moreover, these events disrupt transportation networks, affecting daily life and businesses. In addition, threats from terrorism and sabotage create further risks to critical infrastructure.
How to Conduct Risk Assessments for Critical Infrastructure?
A strong risk assessment is a key part of protecting critical infrastructure. By carefully identifying, assessing, and prioritising potential threats and weaknesses, businesses can create effective strategies to protect their operations.
1. Identifying Potential Threats and Vulnerabilities
The first step in a risk assessment is to identify potential threats and vulnerabilities that could impact critical infrastructure. These may include:
- Cyber Threats:
- Ransomware attacks
- Phishing attacks
- Denial-of-service (DoS) attacks
- Data breaches
- Physical Threats:
- Natural disasters (e.g., bushfires, floods, cyclones)
- Human-made disasters (e.g., terrorism, sabotage)
- Supply chain disruptions
- Operational Threats:
- Human error
- Equipment failure
- Inadequate security procedures
To identify vulnerabilities, organisations should conduct thorough security audits and assessments of their systems, networks, and physical infrastructure.
2.Assessing the Likelihood and Impact of Risks
Once potential threats and vulnerabilities have been identified, the next step is to assess the likelihood and impact of each risk. This can be done using a risk matrix, which plots risks based on their likelihood and potential impact.
- Likelihood: The probability of a risk occurring.
- Impact: The potential consequences of a risk, such as financial loss, operational disruption, or reputational damage.
By assessing the likelihood and impact of each risk, businesses can prioritise their mitigation efforts and allocate resources accordingly.
3.Prioritising Risks for Mitigation Efforts
Undoubtedly, not all risks are created equal. To effectively allocate resources and prioritise mitigation efforts, businesses should prioritise risks based on their likelihood and impact.
A common approach is to use a risk matrix to identify high-priority risks. High-priority risks are those with a high likelihood of occurrence and a high potential impact.
Once high-priority risks have been identified, organisations can develop and implement mitigation strategies to reduce their likelihood and impact. These strategies may include:
- Technical Controls:
- Implementing strong access controls
- Deploying intrusion detection and prevention systems
- Using encryption to protect sensitive data
- Administrative Controls:
- Developing and enforcing security policies and procedures
- Conducting regular security awareness training
- Implementing incident response plans
- Physical Controls:
- Installing security cameras and alarms
- Controlling access to facilities
- Conducting regular security patrols
Building Resilience

The Australian government understands the importance of critical infrastructure and has implemented various programs and initiatives to enhance its resilience. For example, these programs offer funding, support, and guidance to organisations operating critical infrastructure.
Government Programms and Initiatives
Australian Government run different programms aiming to protect critical infrastructure sector, there are some of them:
- Critical Infrastructure Resilience Strategy. This overarching strategy outlines the government’s approach to improving the security and resilience of critical infrastructure.
- Security of Critical Infrastructure Act 2018 (SOCI 2018): This legislation provides a framework for regulating critical infrastructure and imposing obligations on critical infrastructure owners and operators.
- Cyber and Infrastructure Security Centre (CISC). This government agency leads the coordination of critical infrastructure protection efforts, providing guidance, support, and resources to industry.
- Australian Cyber Security Centre (ACSC). The ACSC provides cybersecurity advice and assistance to government and industry, including critical infrastructure sectors.
- Industry-specific initiatives. Many critical infrastructure sectors have their own specific initiatives and programs to enhance security and resilience. For example, the energy sector has the Australian Energy Market Operator (AEMO) which oversees the security and reliability of the electricity grid.
Funding Opportunities and Incentives:
Also the government offers various funding opportunities and tax incentives to encourage critical infrastructure organisations to invest in resilience measures. These include:
- Cyber Security Grants. As mentioned earlier, these grants can be used to fund a range of cyber security initiatives.
- Research and Development Tax Incentives. These incentives can be used to fund research and development projects that improve critical infrastructure resilience.
- State-Based Initiatives. Moreover, some states and territories have their own programs and incentives to support critical infrastructure resilience.
Critical Infrastructure Resilience Strategy
What is the Critical infrastructure Resilience Strategy?
The Critical Infrastructure Resilience Strategy is a document by the Australian Government that outlines how they plan to protect critical infrastructure. For example, this strategy includes working with businesses and organisations that run critical infrastructure to make sure it is secure and can withstand disruptions.
What is the critical infrastructure resilience plan Australia?
The Critical Infrastructure Resilience Plan is a living document that is reviewed annually and outlines national activities. Specifically, these activities are ones that the Cyber and Infrastructure Security Centre (CISC) and the Australian Government will pursue to achieve the objectives outlined in the 2023 Critical Infrastructure Resilience Strategy.
CyberSecurity Frameworks
The Essential Eight Maturity Model
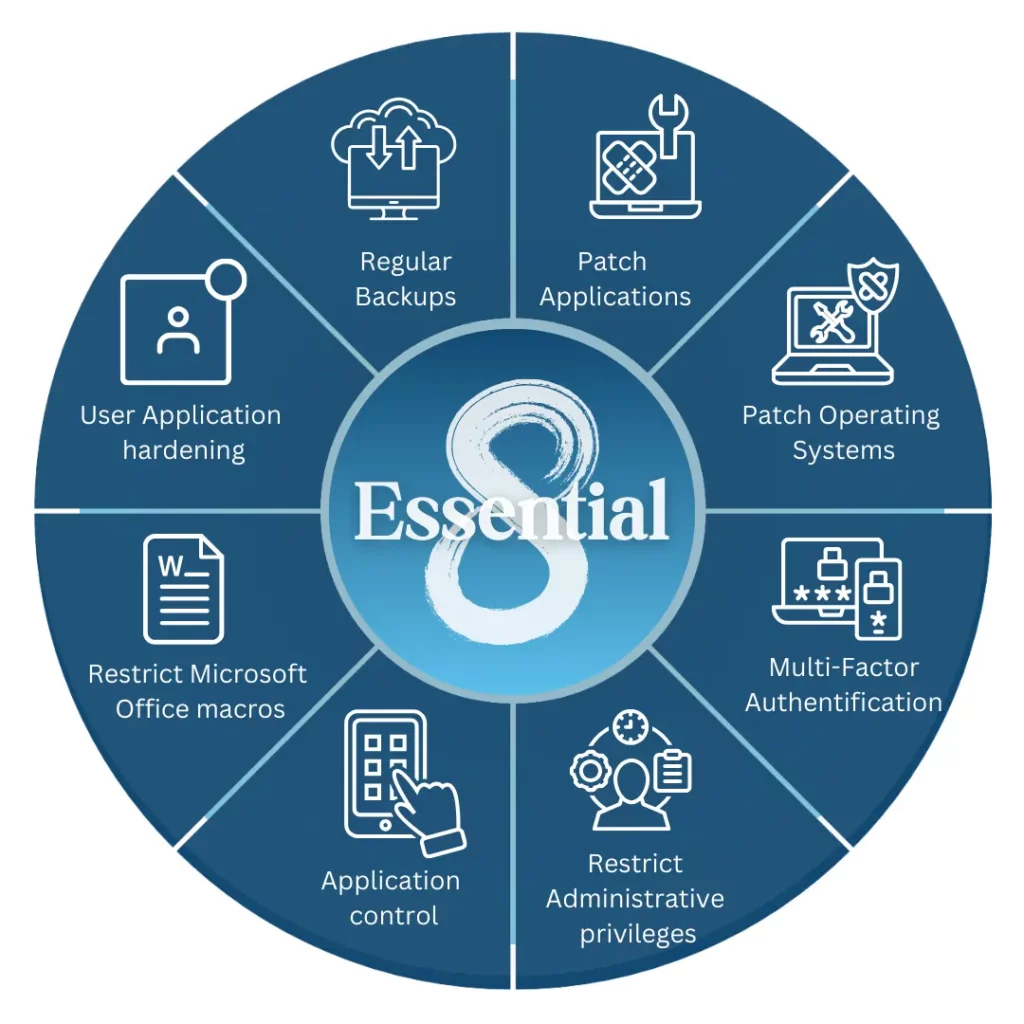
The Essential Eight Maturity Model is a cybersecurity framework developed by the Australian Cyber Security Centre (ACSC). It outlines eight essential cybersecurity controls that organisations, particularly critical infrastructure providers, should implement to protect themselves from cyber threats. Additionally, you could find more about Essential 8, Strategies and implementation tips in our article ‘Defend Your Business With The Essential Eight’.
The NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) is a set of voluntary guidelines developed by the National Institute of Standards and Technology (NIST), a U.S. government agency.
While it originated from a government agency, the CSF is widely adopted by both government and industry organisations worldwide. Generally, it provides a flexible and adaptable framework for managing and reducing cybersecurity risk. The NIST CSF aligns well with other Australian cybersecurity frameworks and standards, such as the Essential Eight, making it a valuable tool for businesses to implement effective cybersecurity measures.
Applying the NIST Framework to Critical Infrastructure
To apply the NIST Framework to critical infrastructure, organisations should:
- Tailor the framework. Firstly, tailor the framework to the specific needs and requirements of the critical infrastructure sector.
- Identify critical assets. Secondly, identify critical assets and systems that are essential to the organisation’s operations.
- Assess risks. Thirdly, assess the risks to critical assets and systems.
- Implement safeguards. Additionally, implement appropriate safeguards to protect critical assets and systems.
- Test and evaluate. Moreover, regularly test and evaluate the effectiveness of safeguards.
- Continuously improve. Finally,continuously improve cybersecurity practices.
Sector-Specific Security Plans
What are SCSSPs?
Sectoral Control System Security Plans (SCSSPs) are essentially safety manuals for critical infrastructure systems. Typically, they provide a structured framework to manage cybersecurity risks tailored to the specific needs of each sector.
Why are SCSSPs Important?
SCSSPs are crucial for safeguarding critical infrastructure, such as power grids, water treatment plants, and transportation networks. By following the guidelines outlined in an SCSSP, organisations can:
- Identify vulnerabilities. Firstly, pinpoint potential weaknesses in their systems.
- Prioritise risks. Secondly, assess the severity of potential threats.
- Implement security measures. Thirdly, develop and implement strategies to protect against cyberattacks.
- Respond to incidents. Lastly, have a plan in place to respond effectively to cyber incidents.
Where to Seek More Information
- Consult with industry associations. Engage with relevant industry groups for sector-specific insights.
- Work with cyber security experts. Moreover, seek advice from cybersecurity professionals specialising in critical infrastructure.
- Refer to government guidelines. Furthermore, use government-issued guidelines and standards for best practices.
Legislative Requirements for Critical Infrastructure Protection in Australia
Critical infrastructure sectors in Australia, including Queensland, are subject to specific legislative requirements designed to enhance their security and resilience.
The primary legislation governing critical infrastructure protection in Australia is the Security of Critical Infrastructure Act 2018 (SOCI Act).
What is the SOCI Act 2018 About?
The Security of Critical Infrastructure Act 2018 empowers the government to work collaboratively with the private sector. Specifically, it aims to identify and mitigate risks to critical infrastructure. In turn, it seeks to protect critical infrastructure from both cyber and physical threats by:
- Firstly, by establishing a framework for identifying and assessing critical infrastructure risks
- Secondly, by imposing a number of obligations on critical infrastructure owners and operators
- Thirdly, by providing a number of powers for the Australian government to respond to cyber and physical security incidents
Therefore, this act imposes various obligations on critical infrastructure owners and operators, including:
- Risk Management. Responsible entities must, therefore, implement robust risk management programs. These programs help identify, assess, and mitigate risks to their critical infrastructure assets.
- Cybersecurity Measures. While specific cybersecurity measures are not directly mandated, the SOCI Act indirectly requires organisations to implement appropriate security measures. For example, this often includes measures like the Essential Eight.
- Incident Reporting. Additionally, responsible entities are obligated to report significant cyber incidents to the Australian Cyber Security Centre (ACSC).
Key points to remember:
- Mandatory Reporting. Cyber incidents that have a significant impact on the delivery of essential services must be reported to the ACSC.
- Voluntary Adoption of Best Practices. While the SOCI Act doesn’t explicitly mandate specific security measures, it encourages organisations to adopt industry best practices, such as the Essential Eight.
- Collaboration with Government Agencies. Critical infrastructure owners and operators are expected to collaborate with government agencies like the CISC and ACSC to share information and coordinate responses to threats.
It’s important to note that the specific requirements and obligations may vary depending on the nature of the critical infrastructure asset and its level of significance.
To ensure compliance with the SOCI Act and other relevant regulations, critical infrastructure organisations in Queensland should:
- Stay Informed. Keep up-to-date with the latest cybersecurity threats and best practices.
- Seek Expert Advice. Consult with Brisbane cybersecurity expert to assess security posture and identify areas for improvement.
- Implement Strong Cybersecurity Measures. Implement robust cybersecurity measures, such as the Essential Eight, to protect their systems and data.
Balancing Government Programs and Third-Party Cybersecurity

The decision of whether to solely rely on government programs or engage a specialised IT security provider is a complex one, and often the optimal approach involves a combination of both.
Leveraging Government Programs
Government programs like the Essential Eight and the guidance provided by the CISC offer valuable frameworks and best practices. By adhering to these guidelines, critical infrastructure businesses can significantly enhance their security posture. However, relying solely on government programs may not be sufficient, particularly for organisations with complex IT environments and unique security challenges.
Benefits of Engaging a Specialised IT Security Provider
A skilled IT security provider can offer several advantages:
- In-depth Expertise: Firstly, these providers have specialised knowledge and experience in cybersecurity, enabling them to identify and address specific vulnerabilities.
- Proactive Monitoring. Secondly,they can implement advanced threat detection and response systems to proactively identify and mitigate potential threats.
- Customised Solutions. Thirdly, IT security providers can tailor their services to the specific needs of your organisation, ensuring optimal protection.
- Compliance Assistance. Additionally, they can help you navigate complex regulatory requirements and ensure compliance with industry standards.
- Incident Response Planning. Finally, they can develop and test incident response plans to minimise the impact of cyberattacks.
A Hybrid Approach: The Best of Both Worlds
A hybrid approach that combines government guidance with the expertise of a specialised IT security provider can offer the most effective protection. This approach involves:
- Adhering to Government Guidelines. Firstly, implement the Essential Eight and other relevant government recommendations.
- Partnering with a Reputable IT Provider. Secondly, engage a provider with a strong track record in securing critical infrastructure.
- Regular Security Assessments. Thirdly, conduct regular assessments to identify and address vulnerabilities.
- Employee Training. Moreover, train employees on cybersecurity best practices to minimise human error.
- Incident Response Planning and Testing. Furthermore, develop and test comprehensive incident response plans.
- Continuous Monitoring and Threat Intelligence. Lastly, stay informed about the latest threats and vulnerabilities.
At Netcomp, we provide a full suite of cybersecurity solutions tailored to meet your unique needs. Our services cover every aspect of protection, including Risk Assessment and Management; Essential Eight Implementation; Ongoing Support and Training.
When you partner with Netcomp Solutions, you’re doing more than meeting regulatory requirements—you’re building a secure future for your business. Get in touch with us today and take the first step toward stronger cybersecurity.



