Cybersecurity with all the “have tos” can easily overwhelm business owners with numerous daily demands. It’s hard for them know what is absolutely necessary and which layers may provide extra benefits. To help make this decision easier, we created an executive guide that outlines common cyber threats. Obviously the guide explains how different cybersecurity measures can protect your business! Our e-book is short and simple – because who has time to read a novel? Check it out today so you can get back on track quickly in knowing where your cyber safety stands!
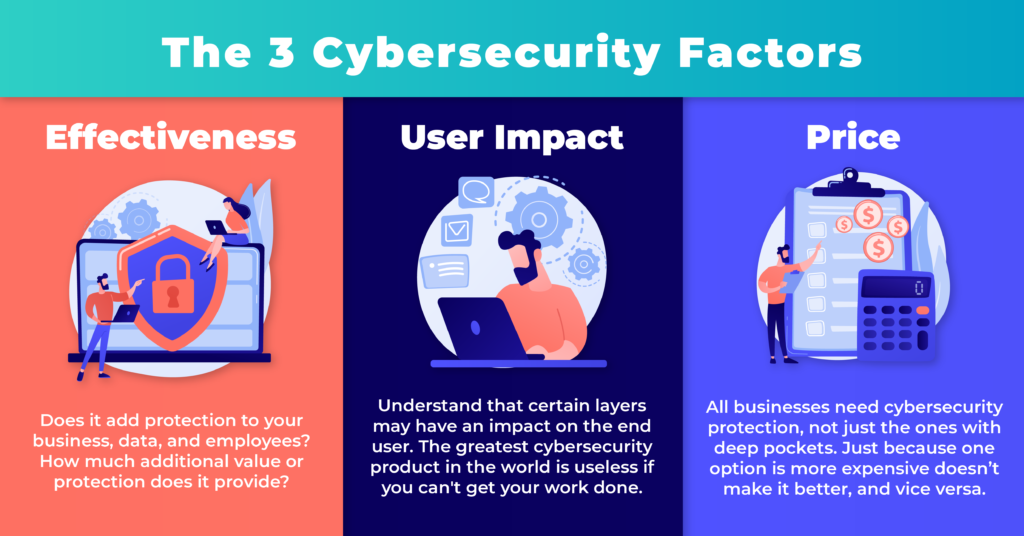
Your IT company should consider effectiveness, user impact and price. These key elements will help you make the best decision for each layer. With this information at hand you can evaluate how these layers affect employees or not, why pricing may be higher or lower and if they are truly effective in use. Use these factors as a guide when making decisions on which tools work best for your team!
Effectiveness
Key factors to consider for spam filtering services are effectiveness and protection. Microsoft 365 comes with a built-in version, but it may not be adequate. IT providers often suggest adding an additional service to protect against malicious emails. They prioritize the safety of their clients over making a sale.
We employ a rigorous review and assessment process for all recommended layers. With these layers, you don’t have to worry about staying up-to-date with security trends.
User Productivity
Security is undeniably important, but it shouldn’t impede progress and cost an arm and a leg. Striking the right balance between security measures and user impact is crucial for an effective IT provider. Our clients benefit from the same level of protection as those with less mindful MSPs.
Multi-factor authentication is a crucial safeguard for protecting accounts and personal information. Although it may seem onerous for users, it can be invaluable in the long run.
Struggling with cumbersome passwords and security codes? We’ve got the solution:
*Authenticator app. You can get a quick push notification to your mobile phone so all that’s required is one simple click.
*Safe devices. – If you use certain devices repeatedly for logging in, we set them as safe devices. This saves time and hassle for users.
Don’t suffer unnecessarily; contact us today and start enjoying convenient and fast secure access.
Price
As IT providers, we understand the need for secure digital protection – and that cost can be a barrier. Our focus is on providing comprehensive cybersecurity packages for small and medium-sized businesses. So our clients can expect to receive an all-inclusive package at an appropriate rate. Accordingly, our team evaluates every option to ensure nothing is missed or too costly.
Many people think that a hefty price tag is the only way to get quality protection. However, it doesn’t have to be this way! By taking advantage of economies of scales we can provide all the features associated with enterprise level security – such as customizability and reporting capabilities – at much lower costs.

If you prioritize cybersecurity for your business, we invite you to explore our Executives’ Guide to Cybersecurity and avail yourself of a free evaluation from our team. We ensure that all the important components are covered so as to give your venture complete coverage when it comes protecting its assets online. Don’t hesitate – contact us today for more information on keeping cyber threats at bay!