Every six minutes, another Australian business falls victim to a cyber attack. That’s not a scare tactic—it’s the stark reality facing business owners across the country right now. The Australian Signals Directorate received over 84,700 cybercrime reports in the past year, and the numbers keep climbing.
If you’re running a small to medium business in Australia, you might think cybercriminals aren’t interested in you. After all, you’re not a major bank or government department. However, here’s the uncomfortable truth: 43% of cyberattacks specifically target small businesses. Why? Because cybercriminals know that smaller businesses often have valuable customer data, limited security budgets, and fewer IT resources to defend themselves.
Moreover, the average cost of cybercrime for small businesses has risen to $49,600 per incident —and that’s just the financial hit. The real damage includes lost customer trust, operational downtime, and in worst cases, permanent closure. In fact, research shows that 60% of small businesses that suffer a significant cyber attack close their doors within six months.
At Netcomp Solutions, we’ve seen firsthand how devastating these attacks can be for Australian businesses. But here’s the good news: most cyber attacks are preventable with the right knowledge and basic security measures. In this guide, we’ll walk you through the most common cybersecurity threats targeting Australian businesses, show you real-world examples of how these attacks unfold, and give you practical steps to protect your business—without needing a degree in computer science or a Fortune 500 budget.

Understanding Cybersecurity Threats: What Australian Businesses Need to Know
What Are Cybersecurity Threats?
Before we dive into specific threats, let’s get clear on what we’re actually talking about. Simply put, cybersecurity threats are deliberate attempts by malicious actors to damage, steal, or disrupt your digital information and systems. Think of them as digital break-ins—except instead of smashing a window, attackers exploit weaknesses in your technology, your processes, or your people.
Why Cybersecurity Matters for Australian Businesses
For Australian businesses, these cyber threats aren’t just an IT problem—they’re a business survival issue. Specifically, the majority of cybercrime reports come from small businesses, and the impact goes far beyond the immediate financial loss. Consider the following consequences:
- Operational disruption: When your systems go down, you can’t serve customers
- Reputation damage: When customer data gets stolen, your reputation takes a hit that can take years to rebuild
- Financial losses: When ransomware locks up your files, every hour of downtime costs you money and market share
- Regulatory penalties: Non-compliance with data protection laws can result in significant fines
The Australian Regulatory Landscape
The regulatory landscape in Australia has also shifted significantly. Notably, the Australian government has introduced stronger protections and requirements to combat the rising tide of cybercrime. In May 2025, mandatory ransomware reporting came into effect for businesses with annual turnovers of $3 million or more. Consequently, eligible businesses must now report ransomware payments to the Australian Signals Directorate within 72 hours—adding another layer of compliance to manage during an already stressful situation.
The True Cost of Cyber Attacks
However, here’s what keeps us up at night on your behalf: the true cost of a cyber attack extends far beyond the ransom payment or the immediate repair bill. Additionally, there are several hidden costs to consider:
Direct Financial Costs:
- Emergency IT support and forensic analysis
- Ransom payments (if applicable)
- System restoration and data recovery
- Legal fees and regulatory fines
Indirect Business Costs:
- Downtime losses (no sales, no productivity)
- Customer notification expenses
- Reputation damage and lost customers
- Opportunity costs of recovery efforts
According to recent studies, businesses experiencing a data breach face an average cost of $3.35 million when all factors are included. For a small business, that’s often an insurmountable figure. Therefore, the harsh reality is that many businesses never fully recover—not because the technical damage was irreparable, but because the combined financial, operational, and reputational impact was too much to bear.
Ultimately, understanding these threats isn’t about living in fear. Rather, it’s about recognising that cyber security is now as essential to business operations as having insurance, maintaining your premises, or keeping accurate financial records. The businesses that thrive in 2025 and beyond will be those that treat cybersecurity as a fundamental business practice, not an optional extra.
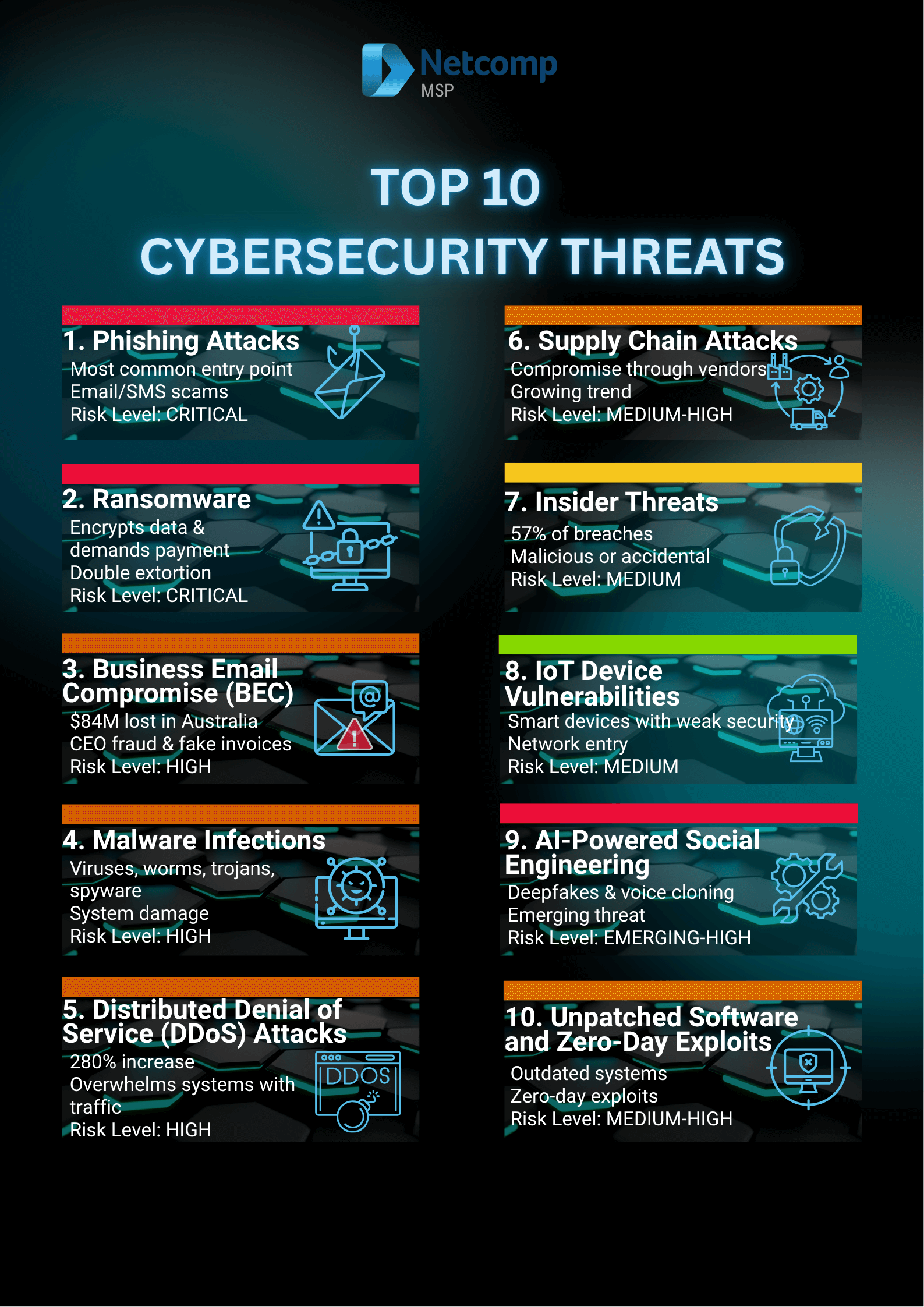
Top 10 Cyber Security Threats Every Australian Business Should Know
Let’s get into the specifics. These are the ten most significant cybersecurity threats targeting Australian businesses right now, based on the latest data from the Australian Cyber Security Centre (https://www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/annual-cyber-threat-report-2024-2025) and our experience protecting businesses across the country.
1. Phishing Attacks
What Is Phishing?
Phishing attacks remain the most common entry point for cybercriminals targeting Australian businesses. In simple terms, phishing is when an attacker disguises themselves as someone trustworthy—like your bank, a supplier, or even your CEO—to trick you or your employees into handing over sensitive information or clicking malicious links.
How Phishing Attacks Work
These attacks typically arrive via email or SMS, and they’ve become frighteningly sophisticated. Specifically, gone are the days when phishing emails were easy to spot with their broken English and suspicious attachments. Instead, today’s phishing campaigns use:
- Legitimate-looking branding from trusted organisations
- Personalised details that make them appear genuine
- Urgent language that pressures immediate action
- Convincing sender addresses with minor variations
For example, you might receive an email that appears to be from Australia Post about a parcel delivery, from the ATO about tax documents, or from your software provider about an urgent security update.
The AI Factor
Furthermore, artificial intelligence continues to shape the cybercrime landscape, with cybercriminals leveraging AI tools to conduct increasingly targeted attacks, including social engineering attacks. As a result, phishing emails are getting harder to detect, even for security-aware staff.
Why Small Businesses Are Vulnerable
Small businesses are particularly vulnerable because attackers know you’re busy, often working with limited staff who wear multiple hats. Consequently, when you’re rushing to meet a deadline or dealing with a dozen urgent tasks, it’s easier to let your guard down and click that “urgent invoice” link without thinking twice.
Warning Signs to Watch For
Common red flags include:
- Unexpected requests for sensitive information
- Extreme pressure to act immediately
- Slight variations in sender email addresses (like ‘support@bankofaustraIia.com‘ instead of ‘support@bankofaustralia.com‘)
- Requests to click links or download unexpected attachments
- Generic greetings instead of personalised messages
Remember: If something feels off, it probably is.
2. Ransomware
Understanding Ransomware
Ransomware has become one of the most destructive threats facing Australian businesses. Essentially, this malicious software encrypts your files, locking you out of your own data, then demands payment (usually in cryptocurrency) to restore access. Indeed, ransomware is effective, high-impact malware that can cripple an organisation’s ability to function, causing serious operational, financial, and reputational consequences for victims.
Modern Ransomware Tactics
What makes ransomware particularly nasty is the evolution of attack methods:
Double Extortion:
- First, criminals steal your data
- Then, they encrypt your systems
- Finally, they threaten to publish sensitive information if you don’t pay
Triple Extortion:
- All of the above, plus
- Threats to attack your customers or suppliers
- Demands for additional payments to prevent further damage
Why Small Businesses Are Targeted
Moreover, criminals target small businesses with ransomware because they know you often can’t afford extended downtime. Specifically:
- Every day your systems are locked means lost revenue
- Frustrated customers may take their business elsewhere
- Mounting pressure builds to pay the ransom just to resume operations
- Limited backup options increase vulnerability
According to the Australian Institute of Criminology, small to medium business owners are more likely to be victims of ransomware attacks compared with employees or individuals who are not business owners.
Australian Reporting Requirements
The ransomware threat has become so significant that the Australian government introduced mandatory ransomware reporting for businesses with annual turnovers exceeding $3 million, requiring reports within 72 hours of any payment.
Ransomware-as-a-Service (RaaS)
Additionally, the rise of “Ransomware-as-a-Service” has made these attacks accessible even to less technically skilled criminals who can essentially rent ransomware tools and split the profits with the developers.
3. Business Email Compromise (BEC)
What Is BEC?
Business Email Compromise attacks are the financially devastating cousin of phishing. While phishing might steal your login credentials, BEC attacks use those credentials—or sophisticated impersonation techniques—to trick your business into transferring money or sensitive information directly to criminals.
How BEC Attacks Unfold
Here’s how it typically works:
Stage 1: Reconnaissance
- Attackers compromise a legitimate business email account or create a convincing fake one
- They monitor your email communications to learn about your business
- They identify payment processes and approval authorities
Stage 2: The Attack
- Criminals strike at the perfect moment (e.g., when your CEO is traveling)
- They exploit busy periods or times when scrutiny is lower
- They create urgency to bypass normal approval processes
Common BEC Scenarios
Typical attack methods include:
- Fake invoices from suppliers with “updated” payment details
- Urgent requests from the “CEO” to make immediate wire transfers
- Instructions to change payroll direct deposit details
- Requests to purchase gift cards for supposed business emergencies
- Emails with plausible explanations that create time pressure
The AI and Deepfake Threat
In 2025, BEC attacks have become even more dangerous with the addition of AI-generated deepfake technology. Specifically, criminals can now create:
- Convincing voice recordings that mimic executives
- Video calls that appear to show your boss or trusted suppliers
- Personalised messages that perfectly match communication styles
Artificial intelligence continues to shape the cybercrime landscape, with cybercriminals leveraging artificial intelligence tools to conduct increasingly targeted attacks.
The Financial Impact
Australian businesses reported total BEC losses of almost $84 million in FY2023-24, with each confirmed BEC incident costing an average of over $55,000. Unlike ransomware, where you might retrieve data from backups, money transferred to criminals is almost impossible to recover.
Red Flags to Recognise
Warning signs your employees should watch for:
- Unexpected changes to payment details
- Requests to bypass normal procedures
- Unusual urgency or secrecy
- Requests for gift cards or cryptocurrency
- Communications asking you to verify information through the same channel
Best practice: Always call on a known phone number to confirm unusual requests.
4. Malware Infections
What Is Malware?
Malware—short for “malicious software”—is an umbrella term covering various types of harmful programs designed to damage your systems, steal your data, or give attackers unauthorised access to your network. Think of malware as the digital equivalent of various burglar tools, each designed for a specific malicious purpose.
Types of Malware
The malware family includes several dangerous variants:
Viruses:
- Attach themselves to legitimate programs
- Spread when those programs are run or shared
- Can corrupt files and damage systems
Worms:
- Exploit security vulnerabilities to spread automatically
- Move across networks without human action
- Can rapidly infect entire organisations
Trojans:
- Disguise themselves as helpful software
- Secretly open backdoors for attackers
- Provide unauthorised remote access
Spyware:
- Silently monitor your activities
- Steal sensitive information like passwords and financial data
- Operate undetected for extended periods
Ransomware:
- Encrypts your data and demands payment
- As discussed in detail above
- Often delivered through other malware types
How Businesses Get Infected
Small businesses typically encounter malware through:
- Phishing emails with infected attachments
- Drive-by downloads from compromised websites
- Infected USB drives and external storage
- Vulnerabilities in outdated software
- Malicious downloads disguised as legitimate software
Business Impact
Once malware infiltrates your systems, the consequences can be severe:
Operational Impact:
- Systems slow down to a crawl
- Important files become corrupted
- Network resources become unavailable
- Productivity grinds to a halt
Data Security Impact:
- Customer data gets stolen
- Financial information is compromised
- Identity theft becomes possible
- Competitive information is exposed
Long-Term Impact:
- Attackers gain persistent access to your systems
- Silent data theft continues for months
- Secondary attacks become easier to launch
- Recovery becomes increasingly complex
The Phishing Connection
What makes malware particularly challenging for small businesses is that it’s often delivered through the same phishing emails we discussed earlier. Therefore, that innocent-looking invoice attachment or that “important document” from a trusted contact might actually be malware in disguise. This is why malware protection needs to be multi-layered—it’s not enough to just install antivirus software and forget about it.
5. Distributed Denial of Service (DDoS) Attacks
How DDoS Attacks Work
DDoS attacks work on a simple but effective principle: overwhelm your online services with so much traffic that legitimate customers can’t access them. To illustrate, imagine trying to enter a shop when thousands of people are blocking the entrance—that’s essentially what a DDoS attack does to your website or online services.
The Botnet Problem
Attackers use networks of compromised computers (called botnets) to flood your servers with requests. Notably, the ACSC responded to more than 200 DDoS attacks over the last 12 months, a year-on-year increase of 280 percent.
These compromised computers are often Internet of Things (IoT) devices with weak security, including:
- Smart cameras and security systems
- Home and office routers
- Connected appliances
- Devices that owners don’t even realise have been compromised
Direct Business Impact
The business impact of DDoS attacks is straightforward but painful:
Immediate Consequences:
- Online stores can’t process purchases
- Service providers become inaccessible to clients
- Email communication grinds to a halt
- Customer frustration leads to lost business
Financial Impact:
- Direct revenue loss during downtime
- Cost of mitigation services to stop the attack
- Emergency IT support expenses
- Lost opportunities during the outage
Reputation and Long-Term Effects:
- Potential damage to your reputation when customers can’t reach you
- Loss of search engine rankings if your site stays down too long
- Customer migration to competitors
- Opportunity cost of IT team fighting the attack instead of working on business priorities
Why Small Businesses Are Targeted
Small businesses are increasingly targeted because criminals know that most don’t have sophisticated DDoS protection in place. Furthermore, these attacks serve multiple purposes:
Extortion:
- “Pay us or we’ll keep your site offline”
- Demands escalate if initial attack is successful
- Threats of prolonged attacks during busy periods
Smokescreen Tactics:
- While attention is focused on restoring your website
- Attackers might be breaching other parts of your systems
- The chaos provides cover for more serious intrusions
6. Supply Chain Attacks

Understanding Supply Chain Attacks
Supply chain attacks represent a growing threat that many Australian businesses don’t fully appreciate. Instead of attacking you directly, criminals compromise one of your suppliers, service providers, or software vendors, then use that trusted relationship as a backdoor into your systems.
Why Australia Is Vulnerable
Australia’s economy relies heavily on global supply chains for both goods and services. While this interconnectedness is necessary for business, it creates multiple potential entry points for attackers. Indeed, third-party software vulnerabilities are becoming an increasingly popular initial attack vector in cyberattacks, with findings suggesting a continued upward trend of supply chain attacks.
How Supply Chain Attacks Happen
Here’s a common scenario:
The Setup:
- Your business uses accounting software, project management tools, or cloud services from various vendors
- You trust these vendors and their updates
- Your security systems recognise them as legitimate
The Compromise:
- Attackers compromise one of these vendors
- They push out malicious updates to customers
- These updates carry the vendor’s legitimate digital signature
- Your security systems don’t flag them because they come from a trusted source
The Result:
- Criminals essentially hijack the trust you’ve placed in your supplier
- Multiple businesses get infected simultaneously
- Detection becomes difficult because the infection looks legitimate
Real-World Examples
The impact of supply chain attacks is particularly severe because they can affect many businesses simultaneously. For instance, remember the Medibank and Optus data breaches that made headlines? Those weren’t isolated incidents—they’re symptoms of a broader trend where attackers target the weakest link in the chain rather than trying to breach every company individually.
Your Supply Chain Vulnerabilities
For small businesses, supply chain risks aren’t limited to software vendors. Consider these potential weak points:
Technology Partners:
- IT support providers
- Cloud hosting companies
- Payment processors
- Software-as-a-Service vendors
Business Partners:
- Accounting firms
- Legal advisors
- Marketing agencies with system access
- Contractors with network credentials
The Challenge: What makes this threat particularly insidious is that you’re partly dependent on other organisations’ security practices, which are beyond your direct control. Therefore, you need to carefully vet and monitor all third-party relationships.
7. Insider Threats
The Internal Risk
Sometimes the biggest threat to your business comes from within. Insider threats involve people who have legitimate access to your systems—current or former employees, contractors, or business partners—using that access to cause harm, whether intentionally or accidentally.
The Shocking Statistics
According to a Verizon report, 57% of all database breaches involved insider threats. This statistic surprises many business owners because we tend to focus on external hackers while overlooking the risks posed by people already inside the organisation.
Types of Insider Threats
Malicious Insiders:
These are people who deliberately misuse their access:
- Disgruntled employees who steal data before leaving
- Staff who copy customer lists for personal gain
- Employees selling trade secrets to competitors
- Individuals motivated by revenge or financial gain
Importantly, these individuals have significant advantages:
- They know your security measures
- They understand where valuable data lives
- They have legitimate credentials that don’t raise immediate red flags
- They can act over extended periods without detection
Accidental Insiders:
More commonly, insider threats are unintentional:
- Employees clicking phishing links on work computers
- Staff sharing passwords with colleagues
- Team members working from unsecured public wifi
- Individuals storing sensitive data on personal cloud accounts for convenience
While these aren’t malicious acts, they create serious security vulnerabilities that criminals can exploit.
The Detection Challenge
The challenge with insider threats is that traditional security measures like firewalls and antivirus software can’t stop them. Since these individuals have legitimate access, their activities don’t necessarily trigger alarms until the damage is done. For example:
- A staff member could copy files to a USB drive undetected
- Employees might email customer databases to personal accounts
- Team members could gradually download proprietary information over weeks
Small Business Vulnerability
For small businesses where employees often have broader access than they might in larger organisations (because everyone needs to pitch in on multiple tasks), this risk is magnified:
- The receptionist might have access to customer records
- The junior salesperson might be able to view all pricing data
- The casual IT contractor might have administrative access to your entire network
8. IoT Device Vulnerabilities
The Internet of Things Challenge
The Internet of Things has transformed how businesses operate, but it’s also created a massive security headache. IoT devices include everything from smart security cameras and printers to climate control systems, point-of-sale terminals, and even that smart coffee machine in the break room. Essentially, if it connects to your network and isn’t a traditional computer or phone, it’s probably an IoT device.
The Security Problem
Here’s the problem with IoT devices:
Design Flaws:
- Most are designed with convenience and cost in mind, not security
- They often ship with default passwords that users never change
- They run outdated software with known vulnerabilities
- They have no built-in security features
Network Risk:
- They’re connected to your business network
- They have potential access to everything else on that network
- They’re often forgotten after installation
- Updates are rarely applied or unavailable
Why Criminals Love IoT Devices
Cybercriminals target IoT devices because they’re easy targets that businesses often forget about:
Common Scenarios:
- That security camera installed three years ago still using “admin/admin” credentials
- Smart thermostats serving as gateways to your business network
- Compromised devices added to botnets for launching DDoS attacks
- Devices used as surveillance tools by attackers
- Exploited entry points to reach more valuable targets on your network
Australian Legislation
Australia has introduced cybersecurity legislation in 2024 addressing IoT device security standards, recognising the growing risk these devices pose. However, legislation can only do so much when businesses have already deployed countless IoT devices without considering security implications.
Smart Office Equipment Risks
For small businesses, smart office equipment poses particular risks:
Internet-Connected Printers:
- Store copies of every document printed
- May contain financial records and confidential client information
- Become goldmines for attackers if compromised
- Often have web interfaces with weak passwords
Other Vulnerable Devices:
- Video conference systems with cameras and microphones
- Smart door locks controlling physical access
- Connected alarm systems
- Building management systems
Consequently, all of these devices expand your attack surface while potentially providing sensitive information or access to criminals if not properly secured.
9. AI-Powered Social Engineering
The New Era of Cyber Threats
We’re entering a new era of cyber threats where artificial intelligence isn’t just helping defenders—it’s supercharging attackers’ capabilities. Specifically, AI-powered social engineering represents an emerging threat that’s making traditional security awareness training less effective and attacks more convincing than ever before.
Understanding Deepfakes
Deepfakes—AI-generated fake videos and audio—are no longer science fiction. In fact, criminals can now create:
- Realistic video calls that appear to show your CEO
- Convincing voice calls that sound exactly like a trusted supplier
- Manipulated recordings that seem to come from a colleague
- Content that mimics speech patterns, accents, and mannerisms with frightening accuracy
Real-World Scenarios
To illustrate the threat, imagine these scenarios:
The Fake Video Call:
- You receive a video call from someone who looks and sounds exactly like your managing director
- They ask you to urgently transfer funds to a new account
- The “deal” is time-sensitive and confidential
- Every visual and audio cue appears legitimate
The Impersonated IT Manager:
- A voice message perfectly mimics your IT provider’s support manager
- Instructions to install “urgent security software” that’s actually malware
- The voice, tone, and terminology all match perfectly
- Traditional warning signs are completely absent
Enhanced Targeting Capabilities
The sophistication and personalisation that AI enables represents a significant challenge for small businesses:
AI-Enhanced Reconnaissance:
- Attackers analyse your social media profiles
- They study website content and public information
- They craft highly targeted attacks based on real data
- They understand your business relationships and industry jargon
Timing and Personalisation:
- Attacks coincide with real business events
- Messages reference actual projects or transactions
- Communication matches known patterns in your operations
- Personal details make attacks appear more legitimate
The Detection Problem
What makes AI-powered social engineering particularly dangerous for small businesses is the difficulty in detecting these attacks. Specifically, traditional warning signs don’t apply:
What No Longer Works:
- Checking for poor grammar (AI writes perfectly)
- Looking for generic greetings (AI personalises everything)
- Verifying sender addresses (deepfakes use legitimate channels)
- Trusting your instincts about voice or appearance
Instead, the gut feeling that “something doesn’t quite seem right” becomes harder to rely on when attackers can perfectly mimic legitimate communications.
Preparing for the Future
The future trajectory of this threat is concerning. As AI technology becomes more accessible and powerful, we’ll likely see these attacks become more common and harder to defend against. Therefore, small businesses need to prepare now by:
Implementing Verification Procedures:
- Requiring callback confirmations on known phone numbers for financial requests
- Using pre-agreed code words for sensitive communications
- Establishing multi-person approval for significant transactions
- Never relying solely on recognising someone’s voice or appearance
10. Unpatched Software and Zero-Day Exploits
The Overlooked Vulnerability
One of the simplest yet most overlooked vulnerabilities facing Australian businesses is running outdated software. Essentially, software vendors regularly release updates and patches to fix security holes that researchers or hackers have discovered. When you don’t install these updates, you’re leaving windows unlocked that criminals know how to open.
Why Small Businesses Fall Behind
Unpatched software is a particularly common problem for small businesses. Here’s why:
Common Reasons for Delayed Updates:
- You’re busy running your company
- Update notifications feel like inconvenient interruptions
- The software is working fine (why risk breaking it?)
- Updates take time and might require system restarts
- They could interfere with busy work periods
We understand these concerns—we hear them regularly from clients. However, the risks far outweigh the inconvenience.
The Reality of Unpatched Systems
Here’s what actually happens: Cybercriminals use malware designed to covertly harvest information from Australian victims, using stolen data, usernames and passwords to launch subsequent attacks and compromise corporate networks and accounts.
The Attack Process:
- Attackers actively scan the internet for systems running vulnerable, outdated software
- When a vendor announces a security patch, criminals immediately know what vulnerability exists
- They can then exploit it in the unpatched version
- These are among the easiest targets because the solution (updating) is already available
Understanding Zero-Day Exploits
Zero-day exploits take this threat to another level:
What Are Zero-Days?
- Security vulnerabilities actively exploited by criminals
- Attacks occur before the software vendor even knows about them
- Or before vendors have had time to develop and release a fix
- The term “zero-day” refers to vendors having had zero days to address the vulnerability
Why They’re Dangerous:
- No patch is available yet
- All users are temporarily vulnerable
- Traditional security measures may not detect them
- Attackers have a window of opportunity before defenses catch up
The Cascade Effect
For small businesses, unpatched software becomes an entry point for various other attacks:
How Vulnerabilities Connect:
- Ransomware often exploits known vulnerabilities in outdated systems to gain initial access
- Once criminals find one unpatched system on your network, they use it as a foothold
- From there, they can spread across all your devices
- A single vulnerability can compromise your entire infrastructure
Historical Example: The 2017 WannaCry ransomware attack affected over 200,000 computers across 150 countries. Notably, it primarily targeted organisations that hadn’t applied a Windows security patch Microsoft had released two months earlier.
The Protection Connection
The connection between unpatched software and other cybersecurity threats can’t be overstated:
- Firstly, that phishing email we discussed earlier might not succeed if your email client has the latest security features
- Secondly, that malware infection might be blocked if your operating system had the latest defenses
- Thirdly those network intrusions might be prevented with updated firewall software
The Bottom Line: Keeping software updated isn’t glamorous or exciting, but it’s one of the most effective security measures available—and one of the most frequently neglected by businesses.
Responding to a Cyber Attack: What to Do

Despite our best efforts, no system is 100% secure. Therefore, knowing how to respond when an attack occurs can make the difference between a minor disruption and a business-ending catastrophe. So quick, decisive action minimises damage and speeds up recovery.
Immediate Steps When an Attack Is Suspected
Time is critical when you suspect a cyber attack. These immediate actions can contain the damage:
First 5 Minutes:
- Don’t panic, but act quickly
- Stay calm and think clearly
- Don’t try to “fix” things yourself if you’re unsure
- Avoid deleting anything (you may destroy evidence)
- Disconnect affected systems
- Unplug network cables or disable Wi-Fi on compromised devices
- Don’t shut down computers (this can destroy valuable evidence)
- Isolate infected systems to prevent spread
- Alert your IT support immediately
- Contact your MSP or internal IT teamIf you don’t have IT support, call the Australian Cyber Security Hotline: 1300 CYBER1
- Have basic information ready: what happened, when, which systems are affected
Next Steps (First Hour):
- Document everything
- Take photos of error messages or ransom notes
- Note the time you discovered the incident
- Record what was happening before the attack
- List affected systems and data
- Document any unusual activity noticed recently
- Change passwords
- Change passwords for affected accounts (from a clean device)
- Enable MFA if it wasn’t already activated
- Use unique, strong passwords
- Don’t reuse old passwords
- Preserve evidence
- Don’t delete logs or files
- Keep affected systems turned on (unless advised otherwise)
- Save any suspicious emails or messages
- Take screenshots of anything unusual
Who to Contact
Having the right contacts can speed up your response significantly:
Immediate Support:
- Australian Cyber Security Hotline: 1300 CYBER1 (1300 292 371) – 24/7 assistance
- Your IT support provider or MSP (like Netcomp Solutions)
- Your cybersecurity insurance provider (if applicable)
Recovery and Support Services:
- ReportCyber: Official incident reporting
Law Enforcement (if required):
- Your local police station for serious crimes
- Australian Federal Police (AFP) for significant incidents
- State police cybercrime units for regional support
Regulatory Authorities:
- Office of the Australian Information Commissioner (OAIC) if personal data is compromised
- Australian Securities and Investments Commission (ASIC) for financial services firms
- Industry regulators specific to your sector
Documentation and Evidence Preservation
Proper documentation is crucial for recovery, insurance claims, and potential legal proceedings:
What to Document:
- Firstly, timeline of events (when you first noticed, what happened next)
- Secondly, systems and data affected
- Thirdly, actions taken in response
- Additionally, communications with attackers (if any – but never negotiate alone)
- Furthermore, financial losses incurred
- Also customer data potentially compromised
- Finally screenshots and photos of errors, ransom demands, or suspicious activity
Why Documentation Matters:
- Insurance claims require detailed evidence
- Law enforcement needs information to investigate
- Regulatory reporting requires specific details
- Post-incident analysis helps prevent future attacks
- Supports any legal proceedings
Communication with Customers and Stakeholders
Transparency is important, but so is timing and accuracy. Here’s how to handle communications:
Internal Communication First:
- Firstly, inform key staff members immediately
- Secondly, brief all employees once you understand the situation
- Thirdly, provide clear guidance on what staff should and shouldn’t do
- Lastly, keep teams updated as the situation evolves
External Communication:
- Consult legal advisors before public announcements
- Additionally, notify affected customers if their data may be compromised
- Moreover, be honest but don’t speculate on what you don’t know yet
- Furthermore, provide regular updates as you learn more
- Also explain what steps you’re taking to address the issue
- Finally, offer support resources for affected parties
What to Say:
- “We’ve identified a cybersecurity incident affecting our systems”
- “We’re working with cybersecurity experts to investigate and resolve the issue”
- “We’ve taken steps to secure our systems and prevent further unauthorised access”
- “We’ll provide updates as we learn more”
- “Customer security and privacy are our top priorities”
What Not to Say:
- Firstly, don’t speculate about causes or scope
- Secondly, don’t promise timeframes you can’t guarantee
- Thirdly, don’t assign blame prematurely
- Fourthly, don’t minimise the incident
Recovery Process Overview
Recovery takes time, but a systematic approach helps you get back to business faster:
1 Phase: Containment (Days 1-3)
- Firstly, isolate affected systems
- Secondly, stop the attack from spreading
- Thirdly, engage professional help
- Also, assess the scope of damage
2 Phase: Eradication (Days 3-7)
- Firstly, remove malware and unauthorised access
- Moreover, patch vulnerabilities exploited
- Additionally, reset compromised credentials
- Finally, clean affected systems
3 Phase: Recovery (Week 2+)
- Restore systems from clean backups
- Furhtermore, verify data integrity
- Moreover, gradually bring systems back online
- Lastly, monitor for signs of persistent threats
4 Phase: Post-Incident (Ongoing)
- Firstly, conduct thorough review of what happened
- Secondly, identify how the attack succeeded
- Thirdly, implement improvements to prevent recurrence
- Additionally, update incident response plan
- Finally, provide additional staff training
Mandatory Reporting Requirements
Understanding your legal obligations is critical:
Ransomware Payment Reporting:
- Firstly, mandatory for businesses with $3M+ annual turnover
- Secondly, must report to Australian Signals Directorate within 72 hours of payment
- Thirdly, applies to payments made from May 2025 onwards
- Lastly, report via cyber.gov.au
Data Breach Notification:
- Required under the Privacy Act if personal information is compromised
- Additionally, must notify OAIC and affected individuals
- Furthermore, report “as soon as practicable” after becoming aware
- Finally, must include specific information about the breach
Industry-Specific Requirements:
- Financial services: APRA reporting
- Healthcare: Additional privacy obligations
- Critical infrastructure: SOCI Act reporting
- Check with your industry regulator for specific requirements
When in Doubt:
- Report to the Australian Cyber Security Hotline for guidance
- Consult with legal advisors
- Generally, better to over-report than under-report
Important: Undoubtedly, recovery from a cyber attack is a marathon, not a sprint. So focus on doing it right rather than doing it fast. Additionally, don’t hesitate to seek professional help—this is not the time for DIY solutions.
Protecting Your Business Starts Today
We’ve covered a lot of ground in this guide—from the ten most critical cybersecurity threats facing Australian businesses to practical steps you can take to protect yourself. Now, let’s bring it all together and, more importantly, get you moving in the right direction.
The Threats Are Real, But So Are the Solutions
Remember those statistics from the beginning? A cyber attack every six minutes in Australia. 43% of attacks targeting small businesses. Also an average cost of $49,600 per incident. Finally, these numbers aren’t meant to frighten you—they’re meant to motivate action.
The reality is this: cybercriminals are counting on you to do nothing. They’re betting that you’ll think “it won’t happen to me” or “I’ll deal with it later.” Meanwhile, they’re actively scanning for vulnerable businesses just like yours.
However, here’s the empowering truth: most cyber attacks are preventable with basic security measures. You don’t need a massive budget or a team of experts. You need to take action on the fundamentals we’ve discussed:
The Quick Wins:
- Enable multi-factor authentication on all critical accounts
- Start backing up your data daily
- Update your software and systems regularly
- Train your staff to recognise phishing attempts
- Use strong, unique passwords with a password manager
These five actions alone will protect you against the majority of cyber threats. That’s not theory—that’s proven protection based on what actually stops attacks.
Cybersecurity Is a Journey, Not a Destination
One of the biggest mistakes businesses make is treating cybersecurity as a one-time project. In other words, you can’t “finish” cybersecurity any more than you can “finish” maintaining your business premises or “finish” managing your finances. So it’s an ongoing practice that needs regular attention.
Think of it this way:
- You don’t lock your doors once and forget about it—you lock them every day
- You don’t backup your data once—you backup regularly
- You don’t train staff once—you provide ongoing education
- You don’t update software once—you keep systems current
The good news? Once you establish good cybersecurity habits, they become routine. Just like checking your email or reviewing your bank statements, security practices become part of how you do business.
The Cost of Inaction
Finally, let’s talk about what inaction really costs. Yes, implementing cybersecurity measures requires an investment of time and money. But consider the alternative:
- The average cyber attack costs $49,600
- 60% of small businesses close within six months of a significant attack
- Recovery takes weeks or months, not days
- Reputation damage can last years
- Customer trust, once lost, is incredibly difficult to rebuild
Compare that to the cost of protection:
- Basic security tools: A few hundred dollars annually
- Staff training: Free to a few hundred dollars
- Professional IT support: Less than the cost of one significant incident
- Peace of mind: Priceless
The question isn’t whether you can afford to invest in cybersecurity—it’s whether you can afford not to.
Your business is worth protecting. And your customers’ trust is worth safeguarding. So your future success depends on the actions you take today.
Don’t wait for a cyber attack to be your wake-up call. Take action now, while you still have the choice.
Need help getting started with your cybersecurity journey? Contact Netcomp Solutions for a complimentary security consultation. We’ll assess your current situation and provide practical recommendations tailored to your business needs and budget. Because your success is our business.